Cyber deception is the most effective way to identify threat actors in any organization’s network. CounterCraft delivers actionable threat intelligence across industries.
-
Categories: Threat Intelligence
New Threat Actor Alert: CC0628
Using our deception technology, we have detected several new threat actors in the wild, some of which we will be sharing weekly, right here. This is the first in a series of posts in which we will describe the IOCs and TTPs of different threat actors we have uncovered, so be sure to check back… Read more
-
Leveraging MITRE ATT&CK | Threat Deception in A Minute
Threat Deception in a Minute highlights just how simple it is to get powerful deception technology set up in your network. This edition features how to utilize the powerful MITRE ATT&CK platform. Whether you’re a current customer or wondering what it’s like to utilize deception, you’ll find these videos quick, interesting and helpful. Read more
-
The Technology Behind Our Cyber Threat Deception
The proprietary pieces of our cyber deception platform work together to make ours the most advanced, secure, and effective in the industry. Read more
-
The Discovery of a New Traffic Anonymizing Network | Founder Chat
CounterCraft’s team of experts has discovered a unique scheme in which threat actors are abusing SSH servers on captured machines as part of the final layer of traffic delivery. Founders Dan and David talk about it in the latest Founder Chat. Read more
-
Categories: Threat Intelligence
A Distributed Anonymizing Network Abusing SSH
CounterCraft’s team of experts has discovered a unique scheme in which threat actors are abusing SSH servers on captured machines as part of the final layer of traffic delivery. This allows a variety of threat activity to pass by security controls on all kinds of websites. We discovered this traffic thanks to one of our… Read more
-
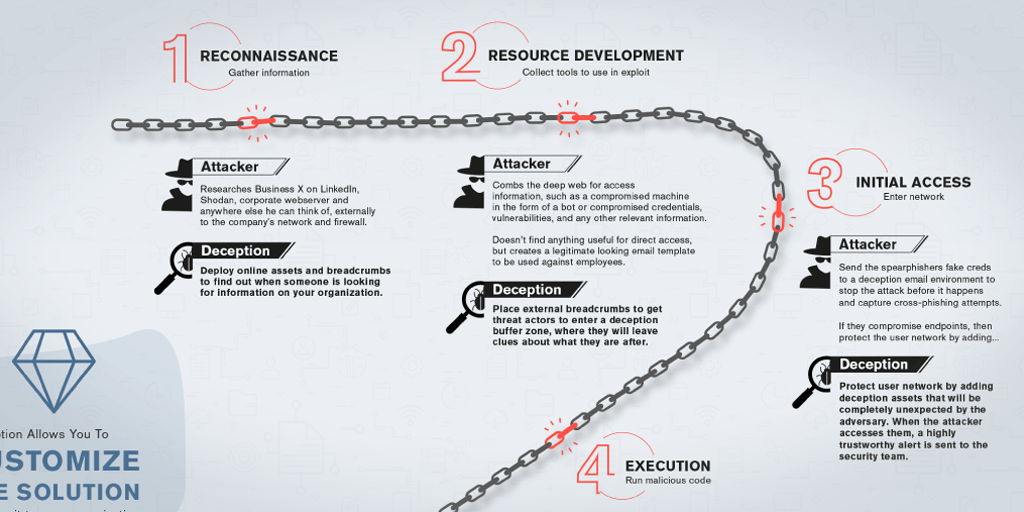
{INFOGRAPHIC} The Anatomy of a Cyber Attack
This infographic breaks down the stages of a typical cybersecurity incident and shows you how to stop it. Read more