MITRE Shield is a classified matrix of Active Defence Techniques (as we’ve mentioned before). The Shield matrix gives a simple framework to define and measure the coverage of your security programme when it comes to dealing with different attacker techniques. Why does that matter?
To quote a CounterCraft customer, “Shield classification gives leadership a way to describe risk and show how our security deployment mitigates that risk.”
That’s it in a nutshell.
Shield finally gives Blue Teams a way to quantify their work and the ability to show how the security techniques they have deployed reduce the risk of attack.
This is also a big deal for CounterCraft, because we can classify different campaigns and provide a standardised, qualitative measure of the security coverage it provides.
In fact, we have applied this classification to the campaigns in the Campaign Catalogue. This means that when you choose a campaign, you can also have a detailed picture of the Shield Active Defence techniques you are deploying.
The Shield classification is applied in many other ways within the CounterCraft Deception Director. In a previous blog, our CEO David Barroso went into technical detail about how this has been achieved, but here I would like to explain what this means in practical terms:

Campaign Catalogue
As we have already mentioned, we can choose any campaign from our catalogue and see which Shield classified Active Defence techniques it deploys. This gives a clear idea of how a specific campaign can augment your security posture. Specifically, you can see how a simply deployed campaign can provide demonstrable mitigation to a specific risk.
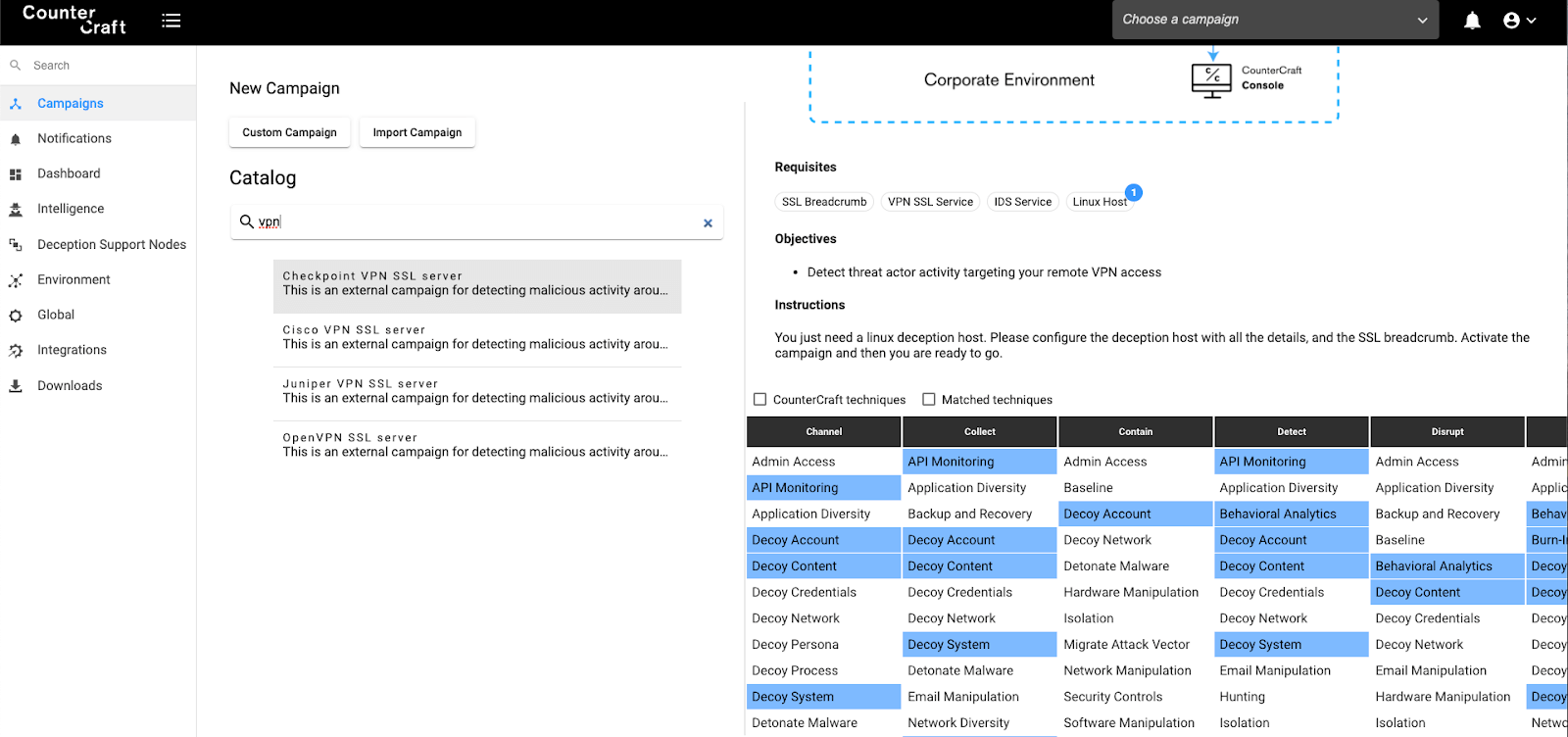

Threat Actor Database
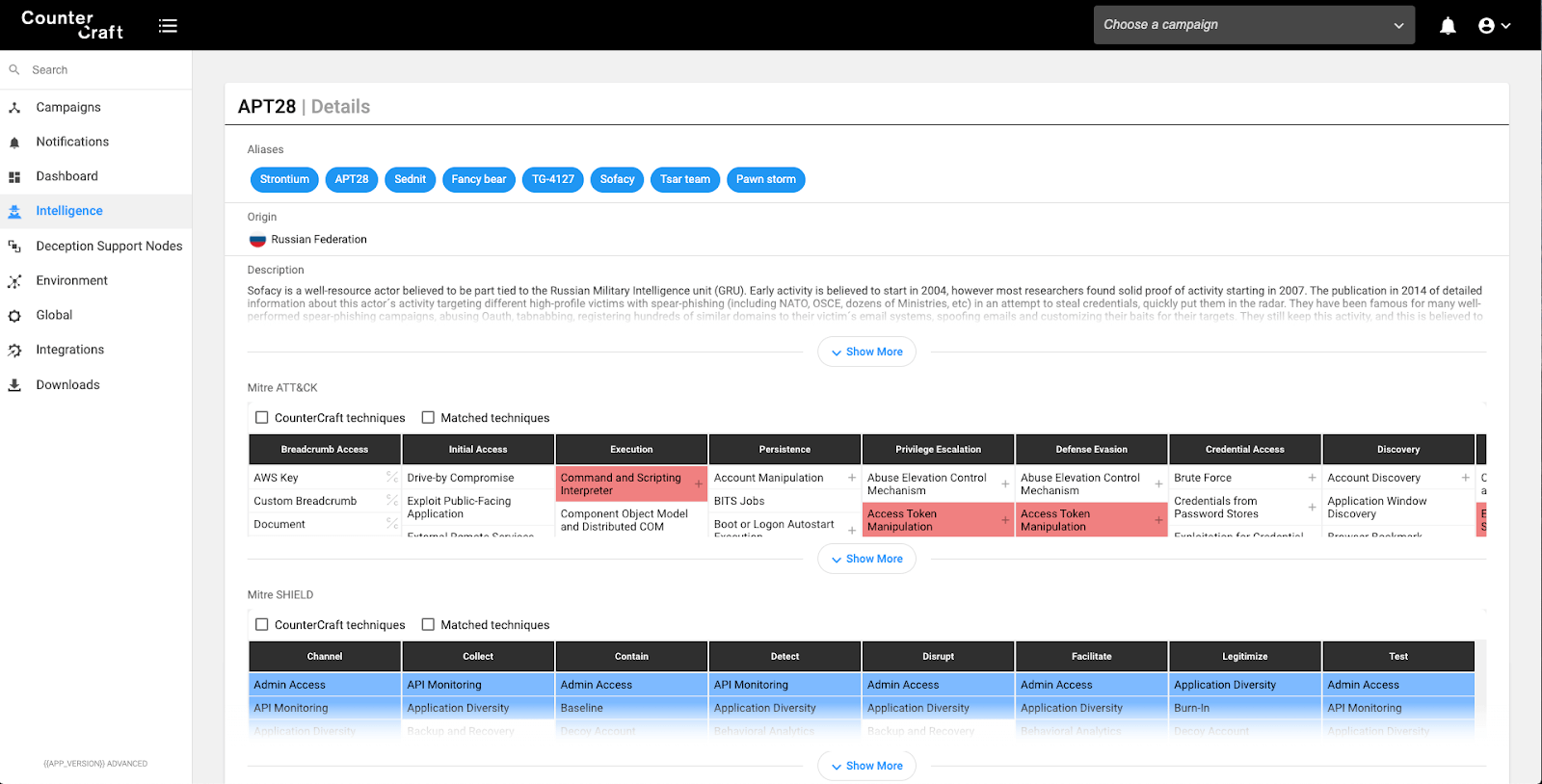
In the same way as the Campaign Catalogue, the CounterCraft Threat Actor Database now includes the Shield Active Defence techniques that, if deployed, will defeat the known TTPs deployed by a given Threat Actor. If your organisation is being targeted by a specific APT, this will set out the Active Defence techniques necessary to mitigate this risk.
In this screenshot you can see our threat actor information database showing the ATT&CK Matrix (Red) associated with the threat actor and the Shield matrix (Blue) highlighting specific defensive techniques that would apply to this actor.

Campaign Builder
The Deception Director now shows the Shield techniques that are deployed within a specific campaign, based on the deception assets deployed. This is accessed from the campaign front page, by clicking on the SHIELD icon:

This shows all the Shield techniques that are facilitated by the current campaign, useful for checking that your campaign is covering the defensive areas you need.
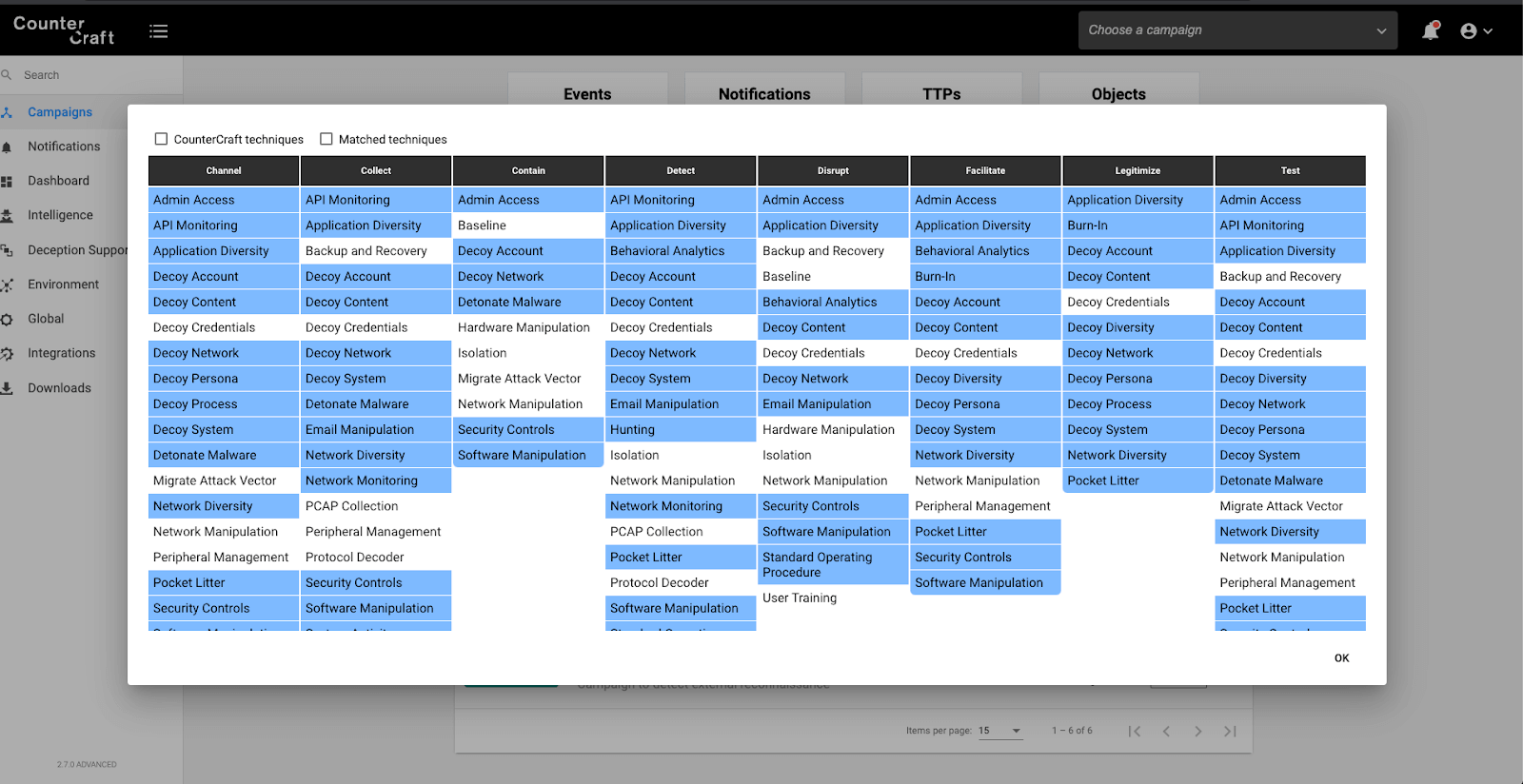
This allows the Active Defense capabilities of any campaign to be measured and increased on the fly. For example, we can add the technique DTE00019 – Email Manipulation by adding an Office365 or Google Suite service to our current campaign.

Deception Environment
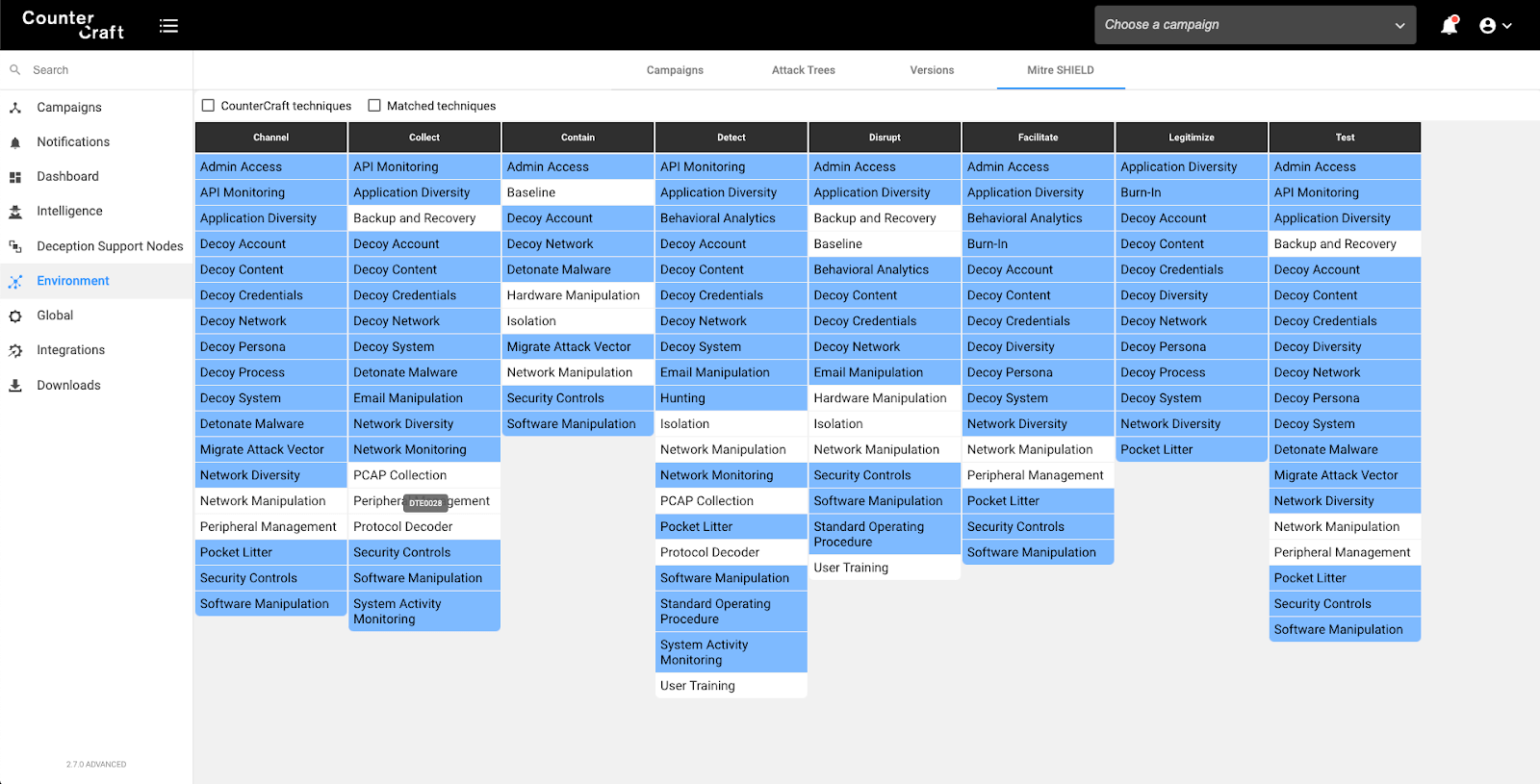
SHIELD techniques are also measures for the whole deception environment. Opening the Environment menu, you see all the Shield tactics and techniques covered by the different campaigns that are currently deployed on this Deception Director. As the CounterCraft Cyber Deception Platform allows you to deploy more than one campaign at a time, you can defend against different adversaries and threats (internal and external) at the same time. This means that risk mitigation through Active Defence techniques can be constantly monitored and refreshed on a global scale.

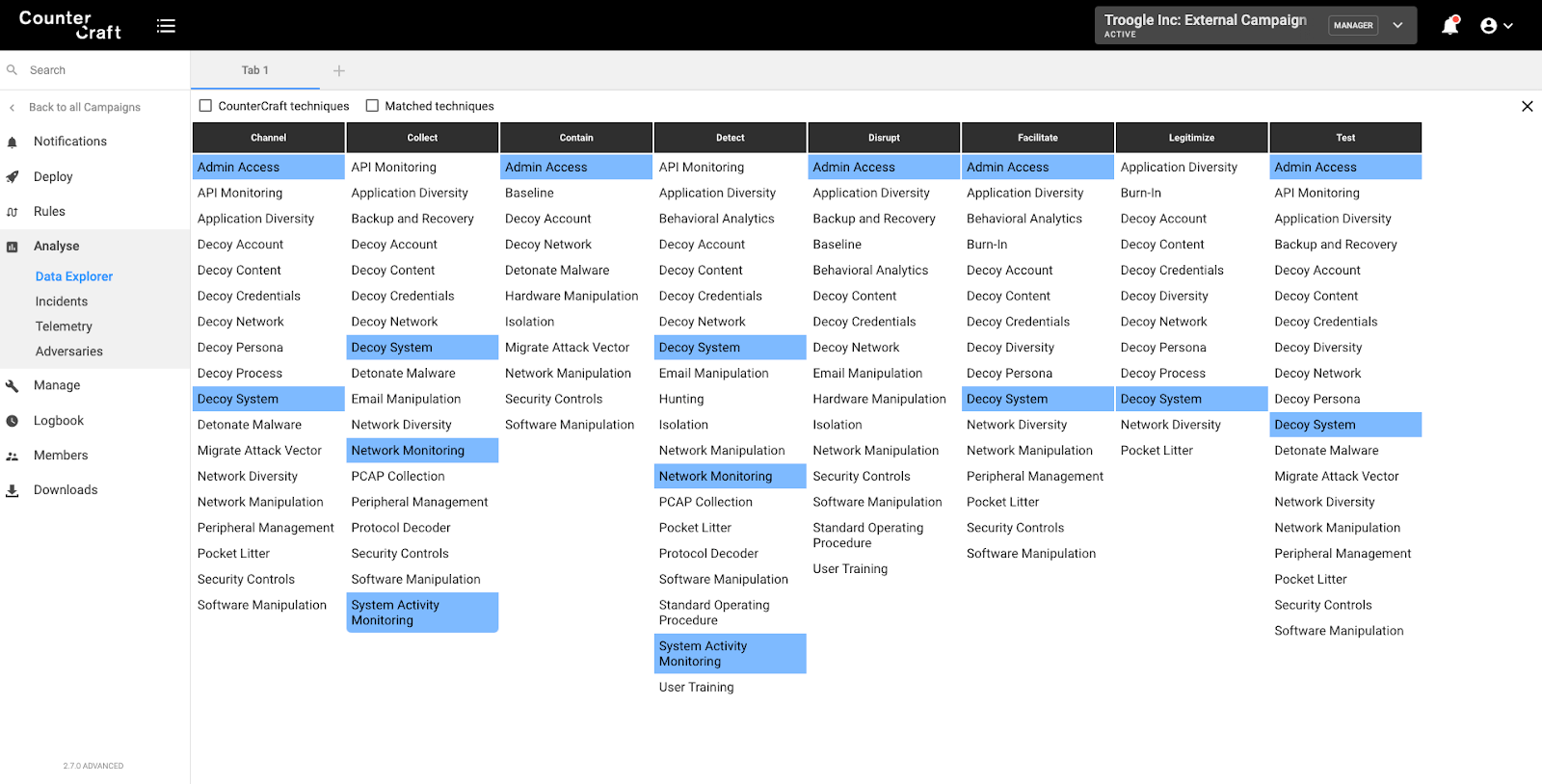
Data Explorer
The integration of the MITRE ATT&CK classification of TTPs in the Data Explorer is well established. It is a really useful tool to visualize all the TTPs detected in a specific campaign, and establish adversary behaviour patterns.
Now we have added a direct ATT&CK →Shield mapping that shows the active defence techniques that relate to the TTPs that have been detected. This gives a useful double check to make sure your campaigns are providing the coverage you need, based on real adversary behaviour.
This is real Threat Intelligence, giving you real, targeted IOCs and directly actionable defensive recommendations on how to mitigate the real risks present in your infrastructure.

CounterCraft Shield Coverage
There are 33 active defence techniques described in the MITRE Shield classification. The CounterCraft Cyber Deception Platform can be used to deploy an industry-leading 30 of these techniques. Some of the techniques are more generic, but in this section we will cover some specific techniques that highlight the flexibility and versatility of the CounterCraft solution. The following examples show how these techniques can be simply and effectively deployed:


Next Steps
MITRE Shield is an excellent tool for bettering security posture, which is why we have worked to integrate it quickly and seamlessly with our Cyber Deception Platform. Find out more about how we use MITRE Shield by contacting CounterCraft. We are only too happy to explain what we do and how we can help you get the best out of deploying deception – from an initial conversation or simple demo to a fully featured deployment.





