Operational Technology (OT) environments are the backbone of critical infrastructure. From power grids and manufacturing plants to water treatment facilities and transportation networks, these systems enable essential services to function seamlessly. As Advanced Persistent Threat (APT) actors adapt their tactics to exploit the convergence of IT and OT, securing these environments requires a proactive, intelligence-driven defense strategy tailored to the unique demands of industrial systems.
Characterized by stealth, persistence, and impact, APTs are a top concern for enterprise cybersecurity leaders. Their targets aren’t just data—they are also after control of systems. And the consequences of a successful attack go far beyond financial loss. They can result in operational shutdowns, environmental hazards, and risks to public safety.
Stopping APTs requires more than traditional defenses. It demands proactive detection, real-time visibility, and a smarter approach to defense, one that deception technology excels in providing.
What Makes APTs So Dangerous in OT?
APTs differ significantly from opportunistic attacks. Rather than targeting immediate gain, APTs are meticulously planned, often executed by state-sponsored or highly organized adversaries with substantial resources at their disposal. These sophisticated attackers aim to infiltrate OT environments silently, employing tailored techniques and tactics designed explicitly for stealth, persistence, and long-term presence. Once embedded within critical infrastructure, APTs patiently navigate through networks, escalate privileges, and exfiltrate sensitive data or disrupt operations over extended periods typically months or even years, without triggering conventional alarms. The complexity, prolonged duration, and precise targeting of OT environments distinguish APTs distinctly from common cyber threats.
Why Traditional Security Falls Short in OT
OT environments present a unique challenge for cybersecurity:
- Legacy Systems: Many industrial control systems (ICS) and SCADA platforms are decades old, making them incompatible with modern security tools or patching processes.
- Downtime Sensitivity: Updating, scanning, or restarting OT systems can result in service interruptions or safety risks—leaving many systems perpetually unpatched.
- Limited Visibility: Unlike IT, many OT networks lack internal monitoring, leaving east-west traffic uninspected.
- Assumed Isolation: Air-gapping was once considered sufficient protection. Today, OT is increasingly connected to IT networks and the cloud—expanding the attack surface.
For example, a power generation facility may house systems running Windows XP to manage turbines. These machines can’t be taken offline for antivirus updates, and yet they’re connected to a central monitoring system accessible via remote access tools. The risk is real, and attackers know it.
Traditional tools like firewalls and intrusion detection systems still have value, but they weren’t built for OT’s complexity, fragility, and interdependencies.
How Deception Technology Elevates APT Detection
Deception flips the attacker-defender dynamic. Instead of trying to block every possible entry point, it creates interactive decoys, fake systems, credentials, and files, designed to lure, engage, and reveal attackers.
Here’s how deception works in OT:
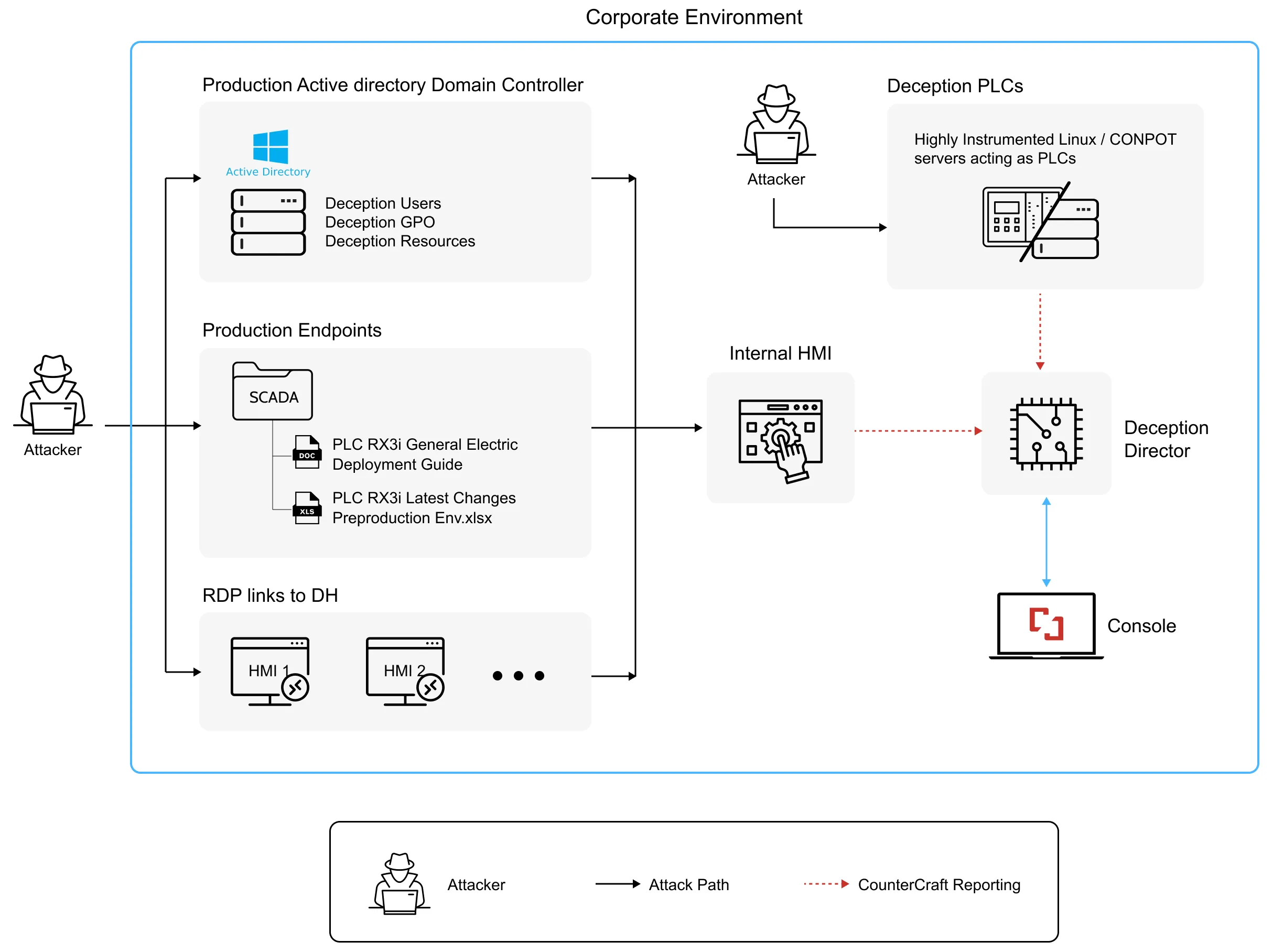
- Decoy PLCs and HMIs (human-machine interfaces) mimic real industrial devices.
- Breadcrumbs (like fake credentials or configuration files) are placed in accessible systems.
- Interaction monitoring detects unauthorized access and triggers alerts instantly.
If an attacker follows the trail, it’s not a breach, it’s a controlled engagement. You see them. You study them. You stop them often before they even touch real infrastructure. By leveraging deception-driven threat intelligence, organizations can proactively expose and disrupt APT activity, significantly strengthening their cybersecurity posture.
An OT Cyber Deception Campaign
Real-World Scenario: Deception in Action
Imagine a threat actor breaches an OT-adjacent IT system in a manufacturing company. Their next move? Scanning for connected control systems to escalate their foothold.
But instead of discovering actual PLCs, they find a decoy, an emulated device that responds realistically, logs all commands, and captures their behavior. The attacker interacts, thinking they’ve found a real asset. In reality, the security team has just received an alert and is watching every move.
No disruption to production. No damage to real systems. But now, the organization has intelligence on the attacker’s tools, techniques, and intent. That’s the advantage of deception: high-fidelity alerts, no false positives, and real-time intelligence.
Blocking Unauthorized Access with Deception-Driven Strategies
Deception technology provides a uniquely effective layer of defense against APTs, specifically in OT environments, where traditional security controls often fall short. Here’s why deception is especially relevant to detecting and mitigating APTs:
Early Identification of Targeted Reconnaissance
APT attackers invest considerable effort in reconnaissance to identify vulnerabilities and gather intelligence about targeted OT infrastructure. Deception platforms deploy authentic-looking decoys, mimicking real OT devices and networks, tricking attackers into engaging prematurely and exposing their presence during the initial reconnaissance phase.
Detecting Lateral Movement Specific to APT Tactics
Once inside, APT actors aim to stealthily move laterally to escalate privileges and embed deeper within OT networks. Deception environments strategically place false resources that appeal specifically to APT behavior, effectively drawing attackers away from legitimate targets and revealing their techniques.
Generating Actionable OT-Specific Threat Intelligence
Deception technology captures attacker interactions within realistic OT scenarios, delivering detailed intelligence on the precise methods and tools APT attackers use against operational technology. This contextual threat intelligence enables OT teams to proactively adjust defenses and response strategies, tailored specifically to the sophisticated methods used by APTs.
Minimizing False Positives in OT Environments
Because deception decoys have no legitimate business purpose, interactions with them signal malicious intent. In OT environments where false positives can disrupt critical operations, this method provides a high-confidence signal that an advanced, persistent attacker is present.
By directly addressing the behaviors unique to APT threats and providing targeted, credible threat intelligence, deception technology significantly enhances OT organizations’ capability to detect, mitigate, and respond to these sophisticated attacks before severe damage can occur.
Deception as Intelligence, Not Just Detection
Every engagement with a decoy asset generates valuable, actionable threat intelligence by capturing critical details of an APT attacker’s behavior. These insights include identifying the tactics, techniques, and procedures (TTPs) that attackers deploy to infiltrate and move within OT networks. Additionally, deception environments detect and analyze any custom malware or specialized tools utilized during interactions with decoys, providing deeper context into attackers’ capabilities. Moreover, deception technology reveals network paths that attackers attempt to traverse, offering precise visibility into how these threats propagate across critical OT infrastructure, enabling faster and more targeted responses.
This intelligence can be fed into EDR/XDR platforms, SIEMs, and threat-hunting programs, strengthening your security posture across both OT and IT environments. It also supports incident response, compliance audits, and strategic planning.
Building a Multi-Layered APT Defense Strategy
Effective APT detection in OT environments requires a holistic, layered approach:
- Insider Threat Detection Software: Monitors user behavior and access anomalies.
- Internal Network Monitoring: Offers visibility into east-west traffic and lateral movement.
- Firewalls and Network Segmentation: Controls access and limits attacker movement.
- Deception Technology: Detects, engages, and misdirects attackers while generating intelligence.
It’s not about replacing your security stack, it’s about enhancing it with proactive tools that see what others miss.
Final Thought: Cyber Resilience Requires Strategic Visibility
The increasing convergence of IT and OT has unlocked innovation, efficiency, and growth. But it has also opened new paths for adversaries, especially those using APTs to target infrastructure that was never meant to be connected.
Deception gives you the upper hand. It allows you to detect unauthorized access, observe adversarial behavior, and act with precision, without compromising uptime or safety.
If you operate in an OT-heavy environment, the question is no longer whether you’ll be targeted by APTs. It’s whether you’ll see them coming in time to respond.
CounterCraft’s deception-powered threat intelligence is uniquely suited to defending OT environments from APTs. With The Platform™, security teams can deploy deception assets across complex ICS and SCADA systems at massive scale and without operational disruption. By engaging adversaries early in the intrusion process and feeding them crafted, misleading telemetry, CounterCraft helps teams detect lateral movement, identify credential misuse, and block unauthorized access to critical systems before attackers reach live infrastructure. Protect your OT environments with high-fidelity deception that sees what other tools can’t.