Canary tokens and honeytokens are simple digital tripwires that generate high-fidelity alerts when an intruder accesses them. While effective for initial detection, they lack the context and engagement capabilities of a full deception platform, which can safely observe, mislead, and gather detailed intelligence from an attacker.
Canary tokens and honeytokens are clever digital decoys that alert you the moment an attacker touches them. A fake AWS key, a bogus document, a dummy database entry…whatever form they take, they generate zero false positives and catch intruders early. But here’s the problem: detection alone isn’t enough. An alert tells you someone broke in, but it doesn’t tell you who they are, what they’re actually after, or how sophisticated they are. That’s where advanced deception platforms come in, transforming a simple tripwire into a full intelligence-gathering operation.
First, let’s dig in a little deeper to see what exactly a canary token is, what a honeytoken is, and what makes them work.
What Is a Canary Token and Honeytoken?
Miners once carried canaries into coal mines as a primitive but effective early warning system. If dangerous gases leaked into the mine, the bird would collapse, signaling an invisible threat and giving the miners time to evacuate. In cybersecurity, we have a digital equivalent: the canary token.
A canary token, or honeytoken, is a decoy digital asset designed to be irresistible to an attacker. It could be a fake AWS key, a specially crafted document, or a false database entry. These tokens serve a single purpose: to lie dormant and unnoticed by legitimate users. The moment an unauthorized actor interacts with one, it triggers a silent alarm, providing a high-confidence signal that someone is exploring areas of your network where they do not belong.
What Is the Difference Between a Canary Token and Honeytoken?
While the two items are virtually interchangeable, there’s a small difference in what they typically refer to:
Canary Token: Often seen as lightweight, easy-to-deploy tokens (e.g., a specific URL, a fake SSH key) designed primarily for quick alerts.
Honeytoken: Can refer to a more integrated part of a larger deception platform, aiming to gather more attacker TTPs (Tactics, Techniques, and Procedures) and blend into the network.
How Do Canary Tokens and Honeytokens Work?
The mechanism behind a canary token is straightforward yet effective. The process involves four key steps:
- Creation: The security team generates a unique token. This token is essentially a resource with a built-in notification trigger, like a unique URL, a DNS entry, API credential, or a file.
- Deployment: The token is strategically placed in a location an attacker is likely to find. This could be within a configuration file, a public code repository, a network share, cloud storage buckets (AWS S3, Azure Blob), or database table. The goal is to make it look like a valuable, legitimate asset.
- Trigger: The attacker, believing they have found something useful, interacts with the token. They might try to use the API key, open the document, or visit the embedded URL.
- Alert: The token sends a real-time notification to the security team, often including valuable data like the source IP address, user agent, and the exact time of access. This rapid alert empowers your team to investigate and respond while the attacker is still in the early or reconnaissance phase.
Their versatility is a major advantage. Here are a few common examples of canary tokens and honeytokens in action:
- Fake AWS or Azure Credentials: Placing fabricated API keys in a public GitHub repository. When an automated script scrapes and attempts to use these keys, it immediately alerts the organization to the attempted credential theft.
- Decoy Documents (Word, Excel, PDF): A file named 2026 Salary and Bonus Projections.docx placed on a file server. The document is configured to trigger an alert the moment it’s opened or previewed, signaling that an unauthorized user is searching for sensitive internal data.
- Invisible Web Bugs and Trackers: A transparent 1×1 pixel image or unique tracking link embedded in a sensitive web application page or an email. When the page or email is loaded, the image fetch sends a notification, acting as a tripwire for unauthorized access.
- Honeytoken Database Entries: A seemingly legitimate but entirely fake customer record within a production or staging database. An attacker exfiltrating data who queries this specific record reveals their presence and activity.
Canary Token Benefits: Why Honeytokens Are a Good Starting Point
Canary tokens are a popular entry point into deception-powered security for several reasons.
- High-Fidelity: If the canary token is well placed and intentional, any interaction with a canary token is, by definition, suspicious. Unlike other security tools that can generate a flood of notifications, alerts from canary tokens and honeytokens are almost never false positives. This provides what security teams crave most: zero noise alerts.
- Low Cost and Simplicity: They are relatively easy and inexpensive to create and deploy. Open-source tools and commercial services allow even small security teams to start using them without a massive investment in infrastructure or training.
- Early Detection: Tokens can detect attackers during the early stages of a breach, such as reconnaissance or lateral movement, before they can access critical systems or exfiltrate data. Getting an early warning, as recommended by security bodies like CISA and NIST, is crucial for minimizing impact.
We love reddit (who doesn’t?) and here’s a thread that goes even more into the basics of canary tokens.
Canary Token Limitations: Why Basic Honeytokens Aren’t Enough
Now that you know why these alerts are effective, let’s get into where they fall short.
An alert from a canary token confirms your network has been breached. But this confirmation is often where the intelligence trail goes cold. While valuable for initial detection, honeytokens have critical limitations that prevent a deeper understanding of the threat. That’s where deception technology’s strengths come into play.
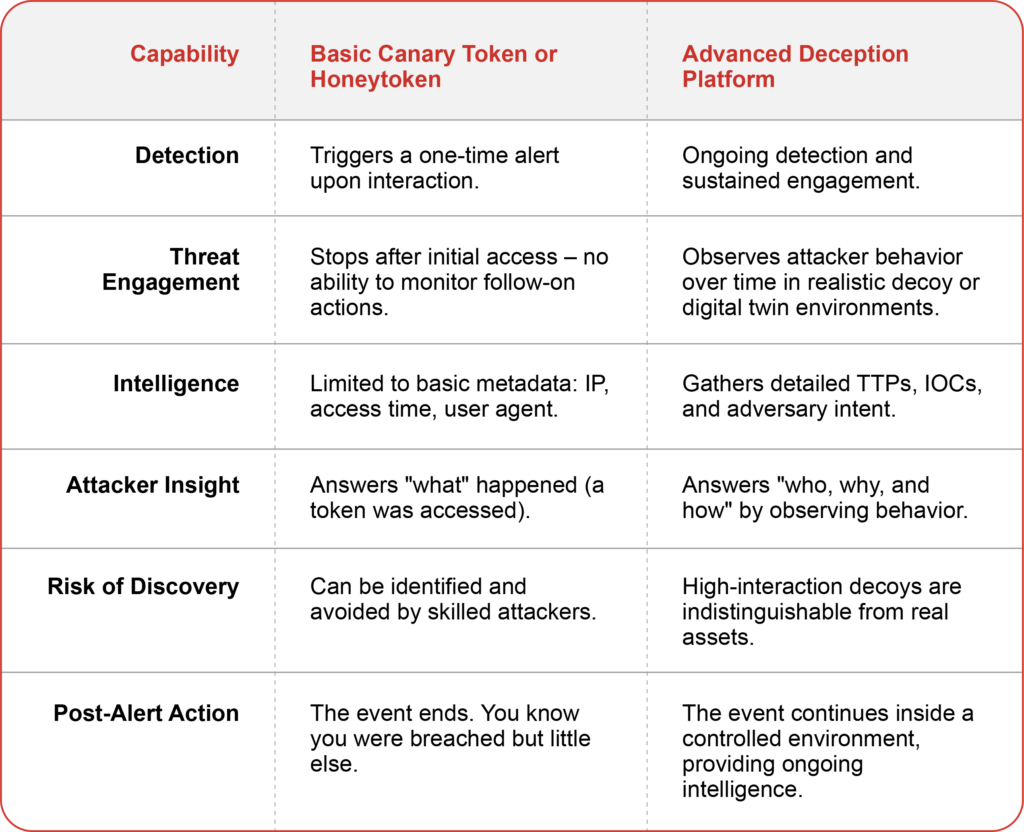
We often hear people conflating deception technologywith honeytokens. “It’s just fancy honeytokens.” And while deception can use honeytokens, that’s far from the truth. Modern deception platforms are a completely different beast. A canary token is a tripwire—one touch and it’s done. A deception platform is an entire fake environment where attackers can roam around, try their tools, and reveal exactly how they operate. You’re not just catching them; you’re studying them in real time. The difference is night and day:
The alert from a canary token is a dead end. It tells you a wire was tripped but provides very little context. Who is the attacker? Is it an automated scanner or a sophisticated nation-state actor? What is their ultimate goal? The interaction ends the moment the alert fires, leaving these critical questions unanswered. You have detected them, but you cannot learn from them, missing a golden opportunity to gather adversary-generated intelligence specific to your organization.
Furthermore, sophisticated adversaries are often aware of simple honeytokens. They may recognize their patterns, rendering them ineffective or, in worse scenarios, using them to mislead defenders about their true intentions.
Honeytokens vs. Advanced Deception in Action
To illustrate the difference between a canary token and advanced deception, let’s walk through a scenario: An attacker has gained access to an enterprise network and begins looking for sensitive files.
Scenario 1: The Canary Token Alert
The attacker finds a network share labelled Finance_Team containing a file named Q1-2026_Financial_Restructuring_Plans.docx. It’s a honeytoken. They copy the file to their machine and open it. Instantly, your security team receives an alert:
- Alert: File Q1-2026_Financial_Restructuring_Plans.docx opened
- Source IP: 198.51.100.10
- Time: 02:15 AM UTC
You now know a breach occurred. You can block the IP address and start an incident response process, but your knowledge stops there. You have no information about the attacker’s tools, their skill level, or what they will do next. The intelligence event is over.
Scenario 2: The CounterCraft Deception Environment
Now, consider the same attack. Except this time, the Finance_Team share, document, and even environment are part of a CounterCraft high-fidelity decoy or “digital twin” deployment. The attacker sees not only the document but also breadcrumbs: “project database” credentials, links to supposed backup drives, or references to cloud storage.
A deception platform is an entire fake environment where attackers can roam around, try their tools, and reveal exactly how they operate.
The attacker opens the document. Just like before, you receive an immediate, zero-noise alert. Instead of a dead end, the attacker attempts to use embedded credentials. Inside this controlled environment, they begin running queries and attempting to exfiltrate data. CounterCraft observes every action they take:
- You see the exact commands they run and the tools they use (sqlmap, PowerShell, etc.).
- You watch them attempt to escalate privileges and move laterally to other decoy systems.
- The entire session is mapped to theMITRE ATT&CK framework, providing a clear picture of their tactics, techniques, and procedures (TTPs).
Instead of just an IP address, you now have a full dossier of specific, actionable intelligence on an adversary actively targeting your organization. You can use these TTPs to hunt for them in your production network and configure defenses to block their specific methods.
Beyond Alerts: How CounterCraft Turns Detection into Actionable Threat Intelligence
CounterCraft goes beyond the limits of canary tokens by replicating the environment of the organization as a digital twin luring attackers away from critical assets ensuring they remain safe from attack.
Instead of a single-use tripwire, you deploy fully functional, high-interaction digital twins that actively mimic your real-world network infrastructure: a decoy Windows domain controller running Active Directory, a lifelike cloud Kubernetes cluster, or even an OT/SCADA system built to match your production environment. The attacker sees familiar services, files, and even synthetic user activity created by CounterCraft’s platform, so they proceed as they would in a real breach.
When an attacker interacts with these decoys, they are drawn into a sandbox-style environment where their every move generates real-time intelligence. Every command, access attempt, and privilege escalation is logged, correlating intent, TTPs, and tooling with the MITRE ATT&CK framework. Because these high-fidelity decoys or digital twins are completely isolated from your live infrastructure, attackers burn time and resources on fake assets, never threatening your real systems. All adversary actions within the deception environment generate zero-noise, high-confidence alerts, ready for seamless integration with SIEM, SOAR, and XDR tools.
CounterCraft’s real-time, adversary-generated intelligence goes far beyond the capabilities of honeytokens by turning every intrusion attempt into an opportunity to learn, adapt, and prevent real harm.
Ready to move beyond simple honeytoken alerts? Learn how CounterCraft’s deception platform can help you gather real-time, adversary-generated intelligence and stay ahead of attackers.