Our team has been a fan of the MITRE ATT&CK framework since the beginning. Every time there is a new update, we eagerly analyze the changes and incorporate the new features into our solution.
The framework is a great tool to describe techniques associated with threat actors, but we also love using it to gain a bird’s eye view of what is going on in a deception environment, mapping the activity we observed in our monitoring to TTPs in real time.
This task is a complex and an ongoing process—mapping one implementation doesn’t mean we have full coverage of the technique. However, the earlier we start experimenting with the new techniques, the earlier we start improving the quality of the mapping.
Each technique has its own particularities, some of them easier than others to map. Let’s see a few examples of the additions in the latest v9 version of the ATT&CK framework.
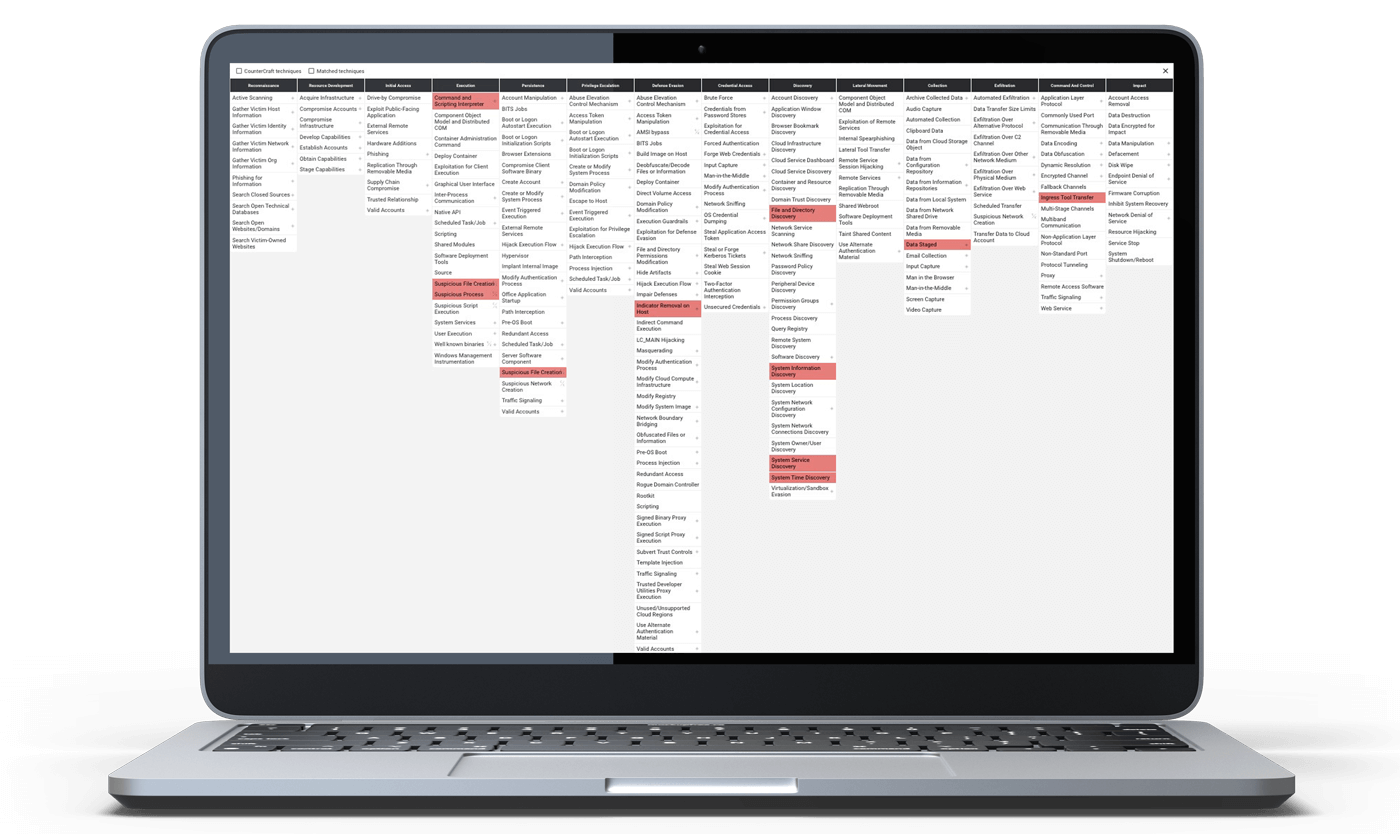
The MITRE matrix in the CounterCraft Cyber Deception Platform.

Let’s start with the System Location Discovery (T1614): This TTP could be detected each time that the System Locale of the system is being retrieved (api, registry), but it is also pretty common to use external services. In these cases, having an initial approach for its detection seems easy. Here is an example of an outbound connection to an external service, marked as T1614.
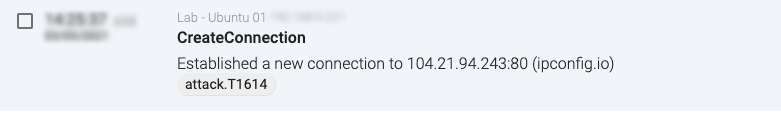
Figure 1: T1614 mapping on a network connection

Another novelty is the Credentials from Password Store (T1555), which has also been updated with two new subtechniques, Windows Credential Manager (T15555.004) and Password Managers (T15555.005). Both of these examples are accessing relatively specific information, and adding detection for those actions based on commands or file access could be quite straightforward.
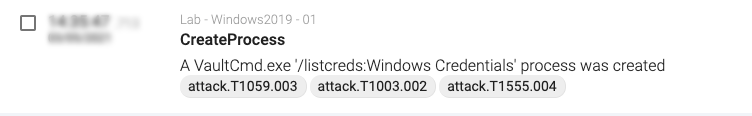
Figure 2: T1614 mapping on a command execution

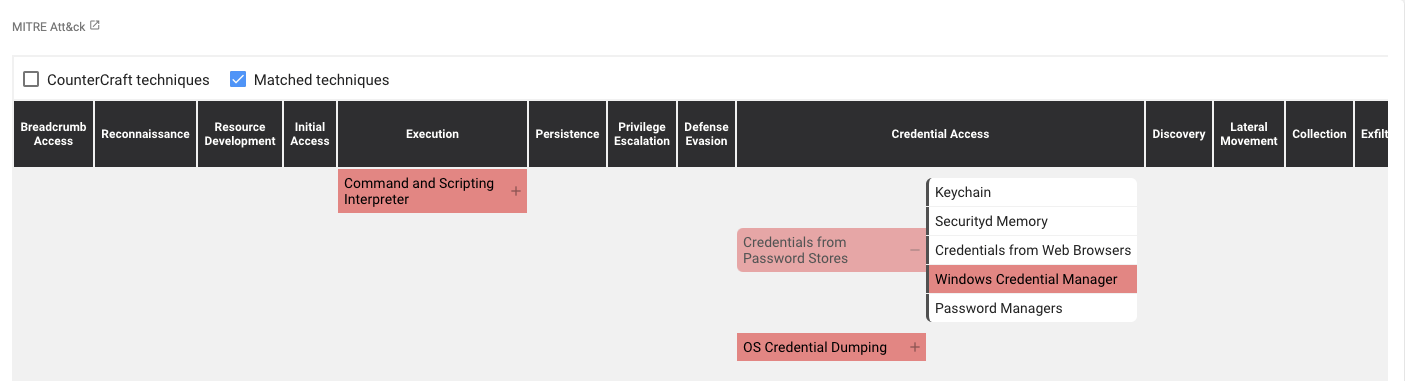
Figure 3: ATT&CK Matrix view for the previous command

For T15555.005, we could, for example, monitor for access to files with any known Password Manager related file extensions, or the access to the memory of these applications.
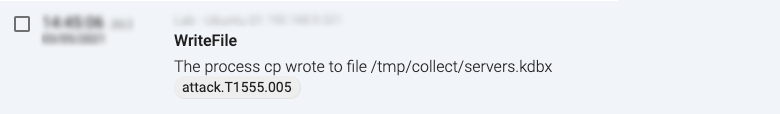
Figure 4: T15555.005 mapping in a file event

But even if it sounds easy, it often gets more interesting. We can’t always map certain TTPs by simple actions, as they depend on the context, and Internet Connection Discovery (T1016.001) is a good example.
An Internet Connection Discovery is usually done by connecting to an external server. It doesn’t matter if using ping or doing a HTTP request. But this connection on its own can’t be marked as suspicious, and contrary to System Location Discovery (T1614), the url itself doesn’t help here.
A couple of possible scenarios where this connection could be marked as suspicious could be when the connection is made after pivoting in the host from the local network (lateral movement), or when an automatic connection is made by a tool/malware to any public server in order to confirm that internet connection is available.
Taking the latest example, we could map this TTP when a file that is dropped into a system is executed connects to the internet in a very short period of time, which could be hunted with an EQL query similar to this one:
sequence by host_id with maxspan=10s
[file where event = "CreateFile" ] by file_basename
[process where event = "CreateProcess"] by process_basename
[network where event = 'CreateConnection' and remote_fqdn != null] by process_basename
For this example, we will download and run a trojan in a deception environment from a compromised network host, as simple as the following:
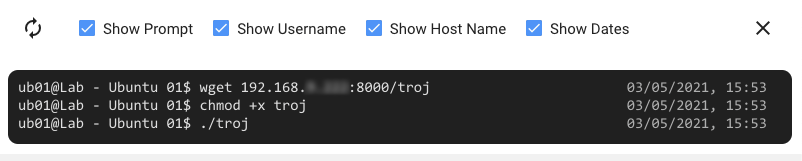
Figure 5: Shell monitoring view in the deception host

The event monitoring gives us more detailed information about what exactly happened in the deception (though that is out of scope for this blogpost), and we can see how those three events are being marked as part of the TTP, giving some context to the connection itself.
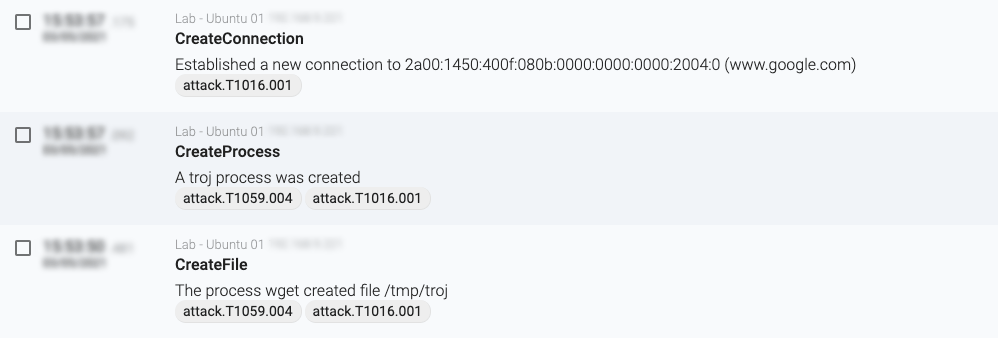
Figure 6: T1016.001 mapping based on sequence

These are just a few examples of the novelties in the latest MITRE ATT&CK version. There is so much left to explore, like how to use ATT&CK for the events we collect from deception containers. Stay tuned for more to come! These changes allow us to take small steps toward a stronger and more cohesive cybersecurity strategy.



