In my opinion, Gartner released an excellent research report titled, Improve Your Threat Detection Function With Deception Technologies, authored by Gorka Sadowski and Rajpreet Kaur. It was published on March 27, 2019. CounterCraft was recognized as a Representative Provider in this report.
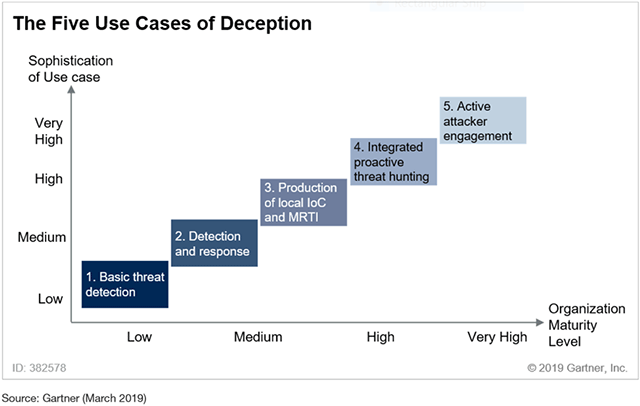
According to the report, “Security and risk management leaders looking for tools to build or expand their threat detection and response function should include deception tools in their stack. These tools are enterprise-ready and fully capable of delivering on five key use cases discussed in this document.” Gartner identified five use cases of deception (see Figure 1 below). In this blog post I want to focus my attention on uses cases 3, 4 and 5. These three uses cases include: 3. Production of local IoC and MRTI, 4. Integrated proactive threat hunting, and 5. Active attacker engagement.
That said if you are in investing in deception technology then I believe you need to ensure it encompasses all five uses cases because you want to future proof your security investment. It may be that currently you want to use deception to meet simple uses cases such as threat detection and lateral movement. However, it is clear to me that no organisation can remain stagnant when it comes to its security posture due to the ever-changing threat landscape. We believe that CounterCraft encompasses all five uses cases, with particular emphasis and expertise on the more advanced use cases.

Why Deception? The CounterCraft Prespective
I believe this report brings to light the current struggle that many in security teams face, which is how to deal with an ever-expanding mountain of data. From within this data they must connect the dots and identify the threat. This is as it sounds, a resource intensive process with no guaranteed outcomes. I believe this is eloquently encapsulated in the report as “Right Data Versus Big Data”. According to the report:
“Threat detection approaches so far have mainly relied on a big data approach. This entails getting as much telemetry as possible from all corners of the organization, and performing the best possible analytics on this dataset to expose potential threats. This approach has proven valuable but at a cost. Log centralization is expensive in operational costs, log management is expensive in storage, and log analytics is expensive in compute. Deception approaches the threat detection problem differently. Deception tools will deploy an ecosystem of deception artifacts across the organization in the form of fakes or decoys that nobody is supposed to interact with (see “Applying Deception Technologies and Techniques to Improve Threat Detection and Response”). Deception tools will not generate any noise unless interacted with, in which case they will start providing extensive telemetry on what the attacker is doing.
- Deception tools adopt a right data approach, as opposed to a big data approach.” *
So, if you are an organisation that faces such challengers then please read on. Apart from bringing the right data at the right time to the security team, a key finding of the report is, “Contrary to more traditional approaches to security, where the defender has to be right 100% of the time and the attacker just needs to be lucky once, deception tools can turn this model upside down. Now the attacker has to be right 100% of the time or trip a mine, and the defender just needs to be lucky once and a mine trips.”
In order to help organisations, build a solid foundation upon which cyber resilience can be delivered CounterCraft collects in an automated manner real time threat intelligence that is specific to the client in question. This delivers a rich seam of data that helps on organisation to understand what type of adversary they face, what types of tools are being deployed against them and what is driving the actions of the threat actor, something that I refer to as intelligence about strategic drivers.

Strategic Drivers
The CounterCraft solution not only generates in real time the automated production of local IOC’s (Indicators Of Comprise) and MRTI (Machine Readable Threat Intelligence), but it goes one step further. CounterCraft delivers intelligence that will identify what are the strategic drivers that are shaping the technical behaviour of the adversary. What is the overarching aim and goal of the adversary.
Having intelligence on the strategic drivers of an adversary allow you to better understand what is the motivation that is driving the threat actor. Technical IOC’s are good but in order to quantify and qualify the risk accurately you need to understand what is driving the adversary, what are his or her objectives. So, in practical terms based on the intelligence (about strategic drivers) I receive I can conclude that the adversary may be driven by financial gain or is a state sponsored actor. Now the security team and the business would respond in different manner depending on what type of adversary they were up against. If you can conclude very early in the detection cycle that the adversary is a state sponsored, you know you are up against an attacker that potentially has unlimited resources your incident response may need to encompass law enforcement assistance. Not only that but other components of your incident response may need to be adjusted too including decisions that may have a direct impact on your business. Intelligence on strategic drivers combined with real time threat intelligence makes for a potent combination in allowing team to get ahead of the attackers and quickly gain situational awareness thus allowing for an informed response based on accurately scoring the threat you are facing.

External Campaigns
The discussion to date has so far focused on the use of deception deployed internally within an organisation to detect an attacker and collect real time intelligence. Now would it not be useful also to collect threat intelligence on threat actors even before they get anywhere near your organisation? What if the security team could deploy external campaigns be, they in the cloud or any variation there of (hybrid cloud) or simply internet facing or focused around the supply chain? That is exactly what the CounterCraft platform can deliver. We know that adversaries are probing and researching almost continuously against internet-based infrastructure that is deployed by an organisation. So, what better way to inform your security stance by understanding what tactics, techniques and procedures are being deployed by threat actors who believe they are engaging with your infrastructure. Not only that with the CounterCraft solution the intelligence gathered is mapped automatically onto the MITRE framework allowing an organisation to understand the technical behaviour of the attacker and how the adversary is attempting to move through your infrastructure.
Do please come back as this is the first part of a series of blog posts that I will write on the potential use cases for deception technology.
Author: Nahim Fazal, BAL – Cyber Threat Intelligence at CounterCraft