The cybersecurity industry is short more than 4 million professionals worldwide. This post walks you through the vicious alert-overload cycle, shows how deception-powered cyber threat intelligence slashes false positives by up to 95 percent, and details concrete wins, from proactive threat-hunting and Zero Trust integration to a healthcare ransomware case study.
Global demand for cybersecurity expertise has never been higher. The World Economic Forum reports more than 4 million open positions worldwide, while Boston Consulting Group places average vacancy rates at 28% across critical security functions. Meanwhile, adversaries weaponize generative AI to launch faster, more targeted attacks. Even enterprises with sizable budgets struggle to recruit, onboard, and retain enough talent to keep pace.
Traditional stop-gaps such as outsourcing, signing bonuses, or “train-and-retain” schemes help but do not solve the underlying throughput problem: analysts spend valuable time trying to keep up with ambiguous alerts. Deception technology provides a clear signal in the sea of noise. By embedding realistic but harmless assets across the network, organizations generate high-fidelity signals that also feed through real-time cyber threat intelligence. The result is less noise, faster insight, and a increased effectiveness with existing staff.
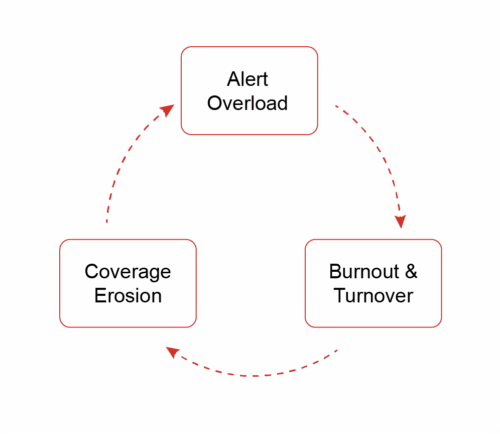
The Vicious Cycle of the Talent Gap
Not enough talent creates daily operational risk. This looks like a vicious cycle that feeds itself and is constantly being recycled.
Alert Overload: Legacy SIEM and XDR tools flag thousands of anomalies daily. Analysts must triage each event without clear context.
Burnout & Turnover: Repetitive triage erodes morale; seasoned professionals leave, draining institutional knowledge.
Coverage Erosion: Vacant seats extend Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR), giving attackers room to pivot deeper.
This is a vicious feedback loop: more sophisticated attacks, fewer experienced eyes, and greater business risk.
Why Does Deception Beat Just Hire More?
Throwing more headcount at the talent gap isn’t scalable when qualified candidates are scarce. Instead of adding eyes, try removing noise. Deception technology flips detection from reactive to proactive and beats the spray a pray method for several reasons:
Reliable Alerts
Decoy servers, documents, credentials, and databases resemble genuine crown- jewel assets. Any interaction, such as port scans, credential use, file access, is inherently malicious. CounterCraft production data shows false positives fall by 90-95 percent, allowing analysts to focus on incidents that matter.
Threat Actor Insights
Deception sensors capture every command an intruder issues, building a timeline of lateral movement, privilege escalation, and exfiltration attempts. This telemetry becomes actionable cyber threat intelligence that security teams use to take action that has real and immediate impact.
AI-Driven Orchestration
Modern deception platforms apply machine-learning clustering to group related events across endpoints, cloud workloads, and operational-technology segments. When a pattern surfaces, automated SOAR playbooks quarantine hosts, push new detection rules, and notify IR teams, all before human triage begins. Deception-powered cyber threat intelligence cuts 95 % of alert noise and lets lean teams win. For deeper data on those alert-reduction metrics, see our blog Cybersecurity Skills Are Scarce: How Deception Technology Turns a Shortage into a Strategic Advantage..
How Can You Build a More Proactive Security Culture With Your Team?
Too many security teams stay stuck in reactive mode. But when alert volume drops and detection becomes more precise, analysts finally get breathing room to go on offense. Deception technology gives them that room and the tools to make the most of it.
- More Time for Threat Hunting: Analysts repurpose reclaimed hours to launch hypothesis-driven hunts, validate MITRE ATT&CK coverage, and red-team the environment using deception-derived indicators
- Faster, Cleaner Incident Response: When alerts are high-fidelity and context-rich, MTTD and MTTR shrink. One Fortune 500 company saw a 67% reduction in containment time after deploying CounterCraft deception technology.
- Better Retention Through Better Work: Analysts want to solve problems, not clear tickets. A joint SANS/ISC² study links diverse daily tasks to 25 percent lower turnover among SOC staff. With deception, monotony goes down and engagement goes up.
The extra time and focus also fuel long-term gains, including better tuning of detection rules, stronger SOAR workflows, and hands-on mentorship for junior analysts using real-world attack data.
Want to see the technical side of how this all works? Read Unveiling the Powerful Fusion of Threat Intelligence and Deception Tactics.
How Can Extra Analyst Time Drive Zero Trust?
Reducing alert fatigue is a win, but it’s what teams do with that time that creates lasting value. Deception technology not only filters out noise; it also generates high-fidelity threat intel that helps enforce Zero Trust principles like “never trust, always verify.”
Here’s how: deception assets act as early-warning tripwires. When attackers engage, their behavior gets captured and mapped in real time. That telemetry feeds directly into your network, showing exactly which users, paths, or assets attackers target first. Teams can then apply that intel to prioritize patches, tune access policies, and test microsegmentation, all without adding headcount.
Again, deception doesn’t just buy time. It turns reclaimed analyst hours into strategic gains: stronger controls, faster Zero Trust alignment, and a leaner team that can defend more with less.
How One Global Bank Turned a Live Attack into an Intelligence Win
A leading multinational bank needed visibility into reconnaissance attempts on its exposed API infrastructure, but it didn’t have the staff to monitor every scan. To solve this, the CounterCraft team deployed a high-fidelity digital twin of the bank’s API server, seeded with realistic breadcrumbs designed to attract adversaries. Within 30 days, an organized threat actor engaged the decoy environment, giving analysts a rare opportunity to observe tactics in real time before any breach occurred.
The deception layer filtered out background noise and delivered only high-confidence alerts, freeing analysts from manual triage. Every command executed by the attacker was captured and mapped to the MITRE ATT&CK framework, feeding directly into the bank’s SIEM and SOAR workflows. This allowed the team to fight back using insights drawn straight from the attacker’s playbook.
Instead of scrambling to contain an incident, the bank turned a live intrusion into a fast-learning loop that reinforced security across departments. The outcome proves that deception-powered cyber threat intelligence delivers enterprise-grade defense without adding headcount.
Read the full story. Download the case study: Digital Twin for the Win: Global Bank Accesses Attacker Playbook
From Talent Gap to Tactical Edge: Deception-Powered Cyber Threat Intelligence
The cyber skills shortage is widening, yet attacks are accelerating. This blog shows why hiring alone cannot close the gap and how deception-driven cyber threat intelligence does. By diverting adversaries into decoy environments, security teams cut false positives, shorten detection and response times, and gain the breathing room to adopt Zero Trust and Continuous Threat Exposure Management. Real-world proof from a global bank that turned a digital twin into an active attacker playbook, demonstrates that lean teams can still outpace sophisticated threats, strengthen compliance, and deliver executive-level ROI metrics without expanding headcount.
CounterCraft converts every decoy interaction into specific, actionable intelligence in real time. Rapid cloud deployment, autonomous attack-path mapping, and out-of-the-box SIEM/SOAR hooks ensure analysts see only what matters. Built-in generative summaries create incident-ready reports, enabling lean SOCs to close skills gaps, demonstrate ROI, and safeguard analyst wellbeing.
See deception in action by requesting your personalized demo today.