Read on to find out how deception technology enhances identity threat detection by deploying decoy credentials, fake user accounts, and digital twin directory environments within Active Directory and Microsoft Entra ID infrastructure. When attackers interact with these deliberately planted assets during reconnaissance or lateral movement, organizations receive high-fidelity alerts that map directly to MITRE ATT&CK techniques, enabling faster detection of credential theft and privilege escalation compared to traditional behavioral analytics.
Your stolen domain admin credentials are already for sale in underground markets. The attacker bought them yesterday, used them this morning to enumerate your Active Directory, and your SIEM logged every action as legitimate administrative activity. By the time your security team notices anything suspicious, the attacker has already moved laterally to your financial databases.
This is the reality of modern identity-based attacks. Adversaries now use valid identities, stolen credentials, and legitimate tools to move quietly through Active Directory, Entra ID, and cloud platforms, making identity threat detection increasingly difficult. Deception, however, shifts the advantage by surrounding your real identities and directory infrastructure with realistic decoy users, groups, credentials, and domain objects that no legitimate person or process should ever touch. When an adversary interacts with those assets, you get a clean, high-confidence signal that turns identity-based attacks into specific, actionable intelligence.
Why identity has become a primary attack vector
We’re sure that you are aware that your users with the most valuable access in your organization are no longer sitting behind a neat clear cut network boundary. Their identities, permissions, and tokens live across on-prem Active Directory, Microsoft Entra ID, SaaS applications, and third-party integrations. That is exactly why attackers have shifted from malware-heavy exploits to identity-based attacks that simply borrow or steal the keys.
The numbers back this up. The Verizon 2025 Data Breach Investigations Report shows that 88% of basic web application attacks involve stolen credentials. Microsoft’s identity team reports roughly 1,287 password attacks every second…that’s more than 111 million per day. Credentials remain the primary battleground in ransomware ecosystems and advanced persistent threats alike.

Traditional identity threat detection struggles because attackers use legitimate tools and accounts, blending into normal day-to-day human behavior. Your EDR sees valid PowerShell commands. The SIEM sees authorized account activity. Your identity analytics engine sees expected authentication patterns. Deception changes that equation by planting digital twin identities, credentials, and directory objects. When an adversary interacts with those assets, you get a signal that maps directly to your Active Directory and Entra ID reality, feeds Zero Trust telemetry, and turns identity from your weakest point into an early-warning sensor.
How identity-based attacks really work
Most identity-based attacks and identity threats follow a recognizable pattern, regardless of sector or size.
-
- Initial access and credential theft
Attackers rarely begin by “hacking AD.” They start with human engineering, identifying gaps in your people’s knowledge to gain access to their credentials:
-
-
- Adversaries deploy phishing and MFA fatigue attacks that trick users into sharing passwords, one-time codes, or approving malicious prompts, increasingly used to bypass MFA according to Microsoft’s 2024 Digital Defense Report.
- Stealer malware is released quietly that empties browser password vaults and session cookies, then resells them in underground markets.
- Password spraying or credential stuffing with usernames and passwords stolen in earlier breaches still causes many of the incidents highlighted in the Verizon Data Breach Investigations Report.
-
The result? A set of working identities, often with enough permissions to start discovery inside your environment. Your identity threat detection strategy needs to assume this stage will eventually succeed.
-
- Privilege escalation and directory abuse
Once inside, attackers turn their attention to identity infrastructure. In hybrid environments, that means both Microsoft Entra ID and traditional Active Directory.
We go really deep into these Entra ID and APT attack vectors here, but common steps include:
-
-
- Enumerating AD to discover domain trusts, admin groups, and high-value servers.
- Using techniques such as Kerberoasting, pass-the-hash, or DCsync to obtain more powerful credentials.
- Abusing misconfigured delegation, shadow admin roles, or legacy identity systems such as ADFS, all of which turn into Identity Threats when not monitored and contained.
-
Want to see to how to stop this type of privilege escalation? Check out our blog Active Directory Security: How Deception Detects and Prevents Privilege Escalation.
-
- Lateral movement to the crown jewels
Now with higher privileges in hand, attackers move laterally, pivoting from identity infrastructure to critical applications, domain controllers, file shares, databases, and SaaS platforms that hold financial data, intellectual property, or regulated customer information. This often happens with legitimate tools and credentials, which makes it very difficult to distinguish from routine admin traffic. By the time traditional identity threat detection tools raise a confident alert, the attacker is often already at the data they came for.
Why classic identity threat detection struggles
The struggle with classic identity threat detection is not a technology problem as much as it is a visibility problem. Most organizations have done the “right” things on paper: multifactor authentication is everywhere, conditional access policies gate sensitive apps, identity threat detection and response tools are in place, and sign-in analytics are getting richer. Yet identity-based attacks and broader identity threats still slip through. The main reason is that attackers are using the exact same tools and paths as your admins and users. They log in through standard flows, use built-in utilities like PowerShell or ADSI, and move through environments in ways that look legitimate. To your SIEM or identity analytics engine, this all reads as “valid user, valid app, valid protocol,” so detection ends up relying on complex heuristics that generate a lot of noise and not many clear answers.
At the same time, the identity environment itself has become sprawling and fragmented. Modern estates stretch across on-prem Active Directory, Microsoft Entra ID, multiple SaaS platforms, and legacy identity providers.
Hybrid AD and Entra ID environments add a level of complexity that traditional controls were never designed to handle, which is why blind spots tend to appear exactly where attackers prefer to operate. These gaps are not theoretical; read more here about how missing context and limited monitoring can turn routine misconfigurations into serious identity threats.
All of this feeds directly into alert fatigue. Your analysts are now flooded with low-confidence signals such as an “unusual login from a new IP” or “elevated token issuance,” even though those patterns can be completely benign in a global, flexible workforce. Then your teams are asked to infer malicious intent from weak signals, and over time it becomes harder to separate what matters from all the background noise. Deception breaks that pattern by introducing a different class of signal. When an attacker touches a decoy identity, a fake group, or a planted credential that no legitimate user would ever use, the alert is not a probability score. It is a clear indication of hostile activity that your SOC can treat as a high-priority incident from the very first event.
Deception for identity threat detection
Deception introduces a fundamentally different class of signal. When an attacker touches a decoy identity, queries a fake security group, or attempts to use a planted credential, the alert isn’t a probability score or behavioral anomaly. It’s a clear indication of hostile activity that your SOC can treat as a high-priority incident from the very first event.
Deception in identity environments works by surrounding your crown jewels with realistic but fake identities, credentials, and assets. Any interaction with those assets is inherently suspicious because no legitimate human or automated process ever needs them.
In Active Directory and identity contexts, deception includes:
- Decoy identities and groups. Fake but believable user and admin accounts, security groups, and service principals that mirror your naming conventions and privilege patterns.
- Decoy domain controllers and directory objects. Digital twins of domain controllers, OUs, and GPOs that look like genuine infrastructure but sit inside an isolated deception environment.
- Honeytokens for credentials and tokens. Realistic credentials, API keys, and OAuth tokens planted where attackers typically look during reconnaissance, such as browser caches, configuration files, and internal repositories.
From an identity threat detection standpoint, this does something very powerful. It converts ambiguity into certainty. Touching a decoy domain admin account or using a planted OAuth token is not “unusual behavior.” It is adversary-initiated behavior that you can treat as a high priority incident from the first event. This is exactly the type of signal that changes how you handle identity threats.
Protecting Active Directory: Turning AD into a sensor
Active Directory isn’t just a directory service—it’s the control plane for most enterprises. Even as organizations modernize with Entra ID and other cloud identity services, AD remains central to how privileges are assigned and how access flows across environments. That makes it both a high-value target for attackers and the perfect place to instrument deception.
In practice, this means creating believable decoy admin accounts that appear in group membership searches but are never used in production. You seed the directory with decoy groups and organizational units that mirror your real structure (“Payment Processing Tier 0,” “Executive Access Group,” or “Domain Controller Backup Admins.”) You stand up decoy domain controllers that respond to discovery queries but live inside a digital twin environment where attacker actions are completely isolated from production systems.
When an attacker uses a decoy credential, queries a decoy DC, or tries to escalate privileges through a fake group, the resulting alert maps directly to MITRE ATT&CK techniques for credential access (T1078), privilege escalation (T1548), and lateral movement (T1021). At that moment, Active Directory stops functioning as passive infrastructure and becomes an active sensor for identity-based attacks.
Detecting lateral movement before it reaches critical systems
Lets face it, identity is the engine that powers lateral movement. Once an attacker can impersonate a user or admin, they can move quietly across systems. Deception lets you intercept that movement without trying to guess intent from logs.
By placing decoys along likely lateral movement paths, you can:
- Trap credential misuse early. Breadcrumbs such as decoy credentials on jump hosts or admin workstations turn lateral pivots into instant alerts when attackers try to reuse them.
- Observe behavior inside digital twins. Digital twins of critical applications, AD, and Entra environments allow you to watch tools, scripts, and privilege escalation techniques without putting production at risk. This is the core of the Entra digital twins story and the APT Detection in OT guide.
- Shrink dwell time. Because no business process touches decoy assets, detection does not rely on long dwell-time analysis. The first interaction provides a trusted signal that can feed automated containment. CounterCraft’s Is Deception the Best Technology to Stop Lateral Movement? blog makes this point clear.
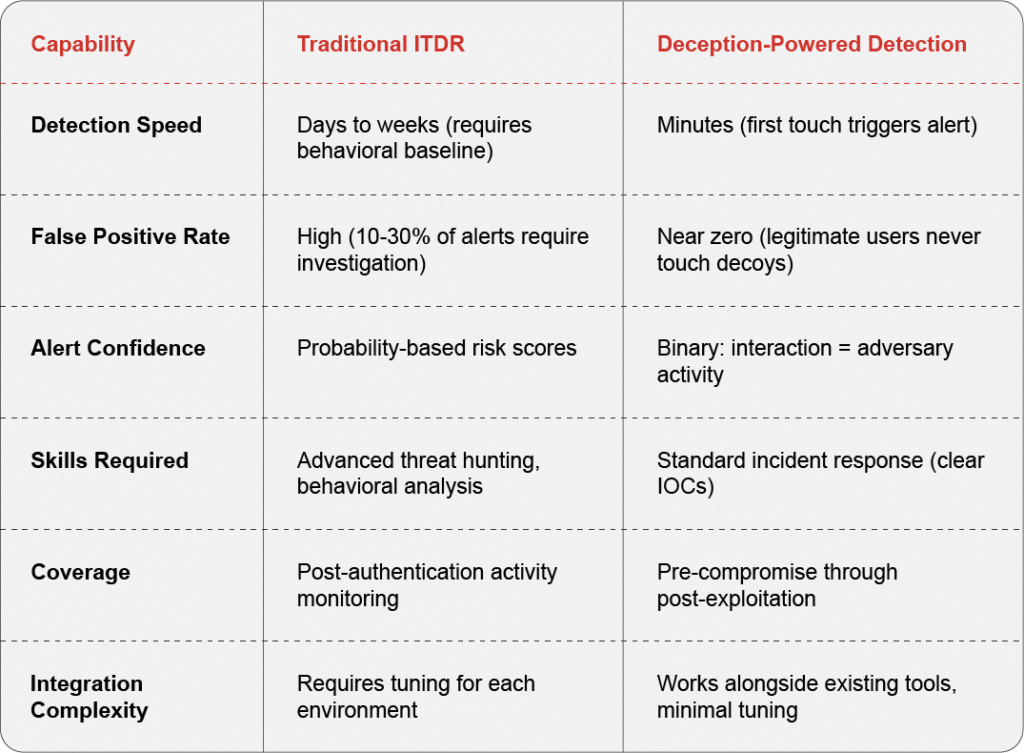
Traditional vs. Deception-Powered Identity Threat Detection
Deception as a Zero Trust enabler
Deception is a natural Zero Trust enabler because it turns the theory of “never trust, always verify” and “assume breach” into something you can see and act on. In NIST SP 800-207: Zero Trust Architecture, NIST explains how Zero Trust moves defenses away from static, network-based perimeters and toward users, assets, and resources, which is exactly where identity threats now live. Microsoft’s identity leaders reinforce this view in blogs such as Microsoft Entra: 5 identity priorities for 2023 and 2023 identity security trends and solutions from Microsoft, where identity is positioned as both the first line of defense and the new battleground. Deception starts from an “assume breach” mindset: instead of trusting that your identity perimeter will hold, you assume adversaries will eventually obtain credentials. Then, you deliberately instrument the paths they’re most likely to take. This approach supports continuous verification with a much higher signal-to-noise ratio. Zero Trust architectures depend on dynamic inputs about user behavior, device posture, and threat intelligence. Deception produces one of the cleanest signals you can feed into those policy engines because a touch on a decoy asset is inherently suspicious.
This also unlocks more automation with fewer false positives. Decoy interactions can be tied directly to SIEM and SOAR playbooks without overwhelming analysts. When a deception alert fires, your automated response can immediately isolate the affected account, revoke active sessions, require re-authentication with elevated verification, and notify your security team—all within seconds, and all with confidence that you’re responding to genuine adversary activity rather than a false alarm.
In practice, this makes Zero Trust far more attainable for identity threat detection, replacing endless low-level anomalies with trustworthy, attack-driven telemetry you can use to contain identity-based attacks early.
What good identity-focused deception looks like
If you and your team are evaluating identity threat detection that uses deception, there are a few qualities to look for.
- Identity-aware design. Campaigns should understand AD and Entra structures, not just drop generic honeypots on the network. Decoy objects must align with your real schema, naming conventions, and privilege tiers. The Active Directory security blog is a good example of this in practice.
- Hybrid coverage. Deception should span on-prem AD, hybrid Entra deployments, and key SaaS platforms where identities and tokens live. The Microsoft Entra ID Protection with Digital Twins article shows how this can work in cloud identity.
- Tight integration with existing tools. High-fidelity identity alerts gain value when they flow cleanly into SIEM, EDR, and SOAR, already mapped to ATT&CK techniques for credential access, privilege escalation, and lateral movement.
- Evidence you can take to the board. Because identity-driven breaches and identity threats are highly visible, leadership wants proof that controls work. Deception-generated telemetry is adversary specific, environment specific, and audit-ready, which makes it easy to show reduced dwell time and improved lateral-movement detection.
How CounterCraft helps you defend your identity crown jewels
Our deception-powered threat intelligence is built for exactly this world, where identities and their permissions are your most valuable assets.
Across Active Directory, Microsoft Entra ID, and critical SaaS platforms, CounterCraft campaigns:
- Plant high-value decoy identities, groups, and credentials that mirror your real users and admin paths
- Stand up digital twins of identity and application environments so you can observe tools, scripts, and lateral movement safely
- Feed specific, actionable identity threat intelligence into your existing SIEM and SOAR stack, mapped to ATT&CK and aligned with modern regulatory frameworks
Ready to turn identity-based attacks into a source of live threat intelligence instead of board-level risk? Book a CounterCraft demo to see deception-powered identity threat detection in action.