You may have heard of Kubernetes, what it is and how it works. At the moment it is one of the hottest technologies when it comes to building a distributed environment in the cloud, public or private.
This is the first of several blog posts in the Kubernetes as a Deception Platform series. In this series, you will learn about Kubernetes and why it matters from a cybersecurity point of view. The series will also cover how to apply deception techniques in order to detect threats, gather intelligence and act on those threats.
In this blog post you will discover what Kubernetes is, why use it, if it is secure, if it can be exploited and a brief introduction to deception using Kubernetes.

What is Kubernetes?
Kubernetes is an open-source container orchestration system, with which you can deploy, manage and scale applications in a distributed environment. Kubernetes was created by Google engineers and open source in June 2014. It was inspired by Borg and Omega, tools Google have used in their own infrastructure. The applications run in containers in clusters. Kubernetes takes care of managing the resources and making sure the application is running on a cluster of servers.
You can find more information here.

Why use Kubernetes?
Long gone are the days of running applications in one server and scaling it up vertically as more resources are needed. Currently many of the applications we can find online need to serve many users and must be highly available. While this can be achieved by creating bespoke software, it’s easier to let other tools like Kubernetes handle the hard parts of keeping a system running in a cluster.
The most important cloud providers (AWS, GCE and Azure) support creating and managing Kubernetes clusters easily.
Kubernetes helps to easily build distributed applications by providing several services and a framework to describe how the application should be deployed. Here is short list of services provided by Kubernetes:
- Service discovery
- Process isolation, by running everything in containers
- Role based access control
- Secure and reliable way to distribute configuration and secrets
- Metrics
- Authentication
- Secure communication between services
The above is by no means a comprehensive list of features—it’s only the tip of the iceberg.
By standardizing how the applications are deployed and adding a level of abstraction that takes care of most of the problems for you, you can mostly focus on the developing the business logic and leaving the rest to Kubernetes and the tools build around it, knowing they will take care of security and reliability for you.
This article features a list of big companies that use Kubernetes and why they choose to do so.

Is Kubernetes secure?
When an application is running in Kubernetes there are four security layers:
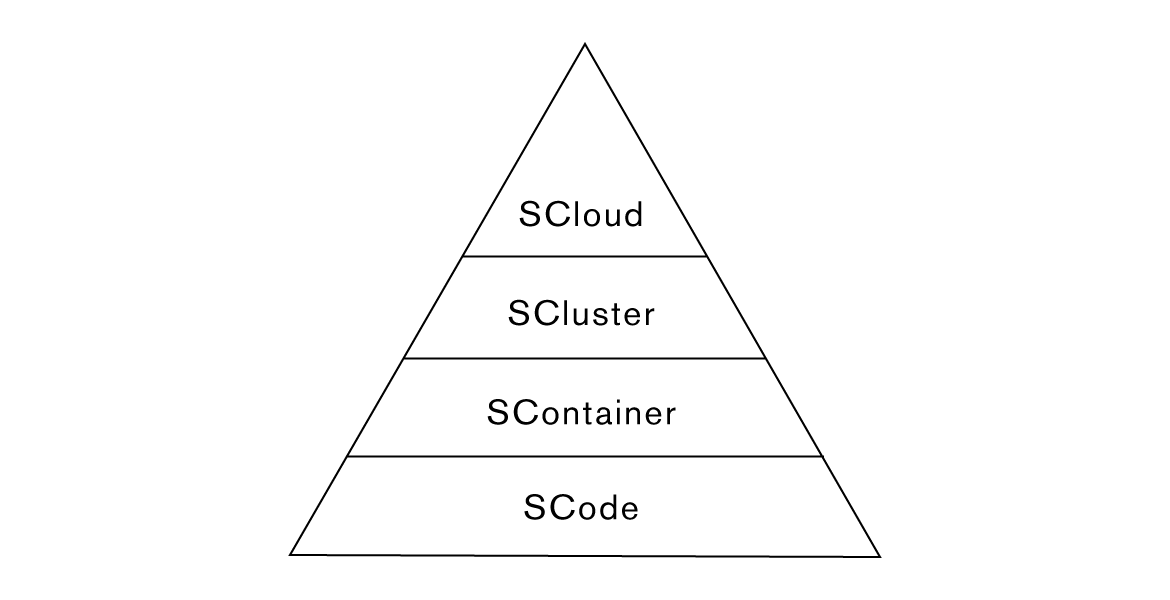
Kubernetes provides very good documentation on how to make sure that all the layers are secure. Because you can configure the security in each of the layers down to the level of limiting which system calls can run in a particular container, you can create secure applications that are really difficult to exploit.
The biggest disadvantage is that it’s a very big and complex system and you must make sure that all the four layers are well configured or else an attacker might find a way in and then move laterally. But Kubernetes, and the services built with it, can make it really difficult for someone to do anything useful once they exploit some application’s vulnerability.
To find out more about this topic click on this link.

Can Kubernetes be exploited?
Just like any other software, Kubernetes has some vulnerabilities . However, there are very few CVEs.
Keep in mind that Kubernetes is only a way to launch applications—therefore it’s easier for attackers to use an exploit for the other layers such as the Container or the Code. For example, any java application using Log4j2 <=2.14.1 would be vulnerable running in Kubernetes. Kubernetes does make it easier to limit what a container can do, and in this case, you could limit all outbound connections and the exploit wouldn’t work.
When an attacker tries to get into any system they will always look for a weak point. As long as one single component is vulnerable, there is a path to get in.

Kubernetes Deception
CounterCraft wants to build the go-to solution when it comes to creating a deception environment. That’s why we are working on integrating our Deception Director with Kubernetes so anybody can easily create deception services, deploy breadcrumbs, monitor them and gather intelligence on threat actors. Kubernetes makes it possible to create deception environments that attackers can’t distinguish from the real production environment.
Stay tuned for the next post in this series, where will go over how to use Kubernetes to build a deception environment.



Xabier Eizmendi is the Lead Software Architect at CounterCraft where he is in charge of designing and developing the backend infrastructure. You can find him on LinkedIn.
