If you have been following our blog, you already know that we are big fans of the MITRE ATT&CK framework. ATT&CK has become the de-facto framework for describing attacker tactics, techniques and procedures (TTPs).
Another MITRE framework that we really love is MITRE Engage, a framework built to describe the different approaches and activities for engaging with adversaries.
At ATT&CKcon 3.0, the latest and most awesome ATT&CK conference yet, we presented on how to map ATT&CK techniques to Engage activities, a strategy that allows you to use the TTPs observed during an incident, or from a specific threat actor, to design engagement activities that effectively gather more threat intelligence.
Just a week before ATT&CKCon, the MITRE Engage team did a fantastic presentation together with Karen Lamb from HSBC at ShmooCon on how they were able to use Engage to interact with a specific threat actor, FIN7, and gather more threat intelligence about them. There was also a nice discussion about it during Cyber Deception Day (April 1, 2022) that we also recommend.
If you are familiar with MITRE Engage (or if you have read our previous blog post about Engage), you will remember that it uses both Cyber Denial and Cyber Deception, within the context of strategic planning and analysis, as the foundation of Adversary Engagement.
Actually the strategic planning and analysis phases are vital for getting the most out of those engagements. If we have a look at the ten-step process proposed by Engage, we can see that we need to carefully consider those phases, as they are even more important than running your operations.
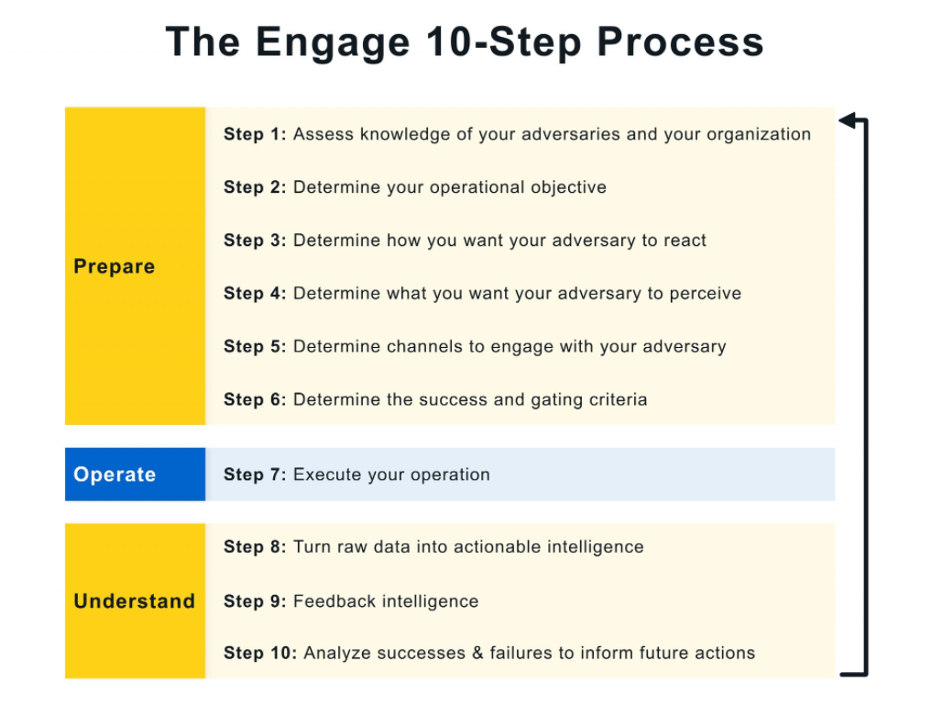
Engage uses ‘Approaches’ and ‘Activities’ (instead of Tactics and Techniques, to make it easier to differentiate them), but the idea is similar to ATT&CK. Approaches let you make progress towards your selected goals and Activities are concrete techniques that you can use to structure your Approaches.
In the following diagram, we can see that the strategic approaches (highlighted in yellow) are also the main steps of the ten-step Engage process. This underlines the fact that you need to make some important decisions before running any operation:
- – defining the storyboarding
- – deciding if you need to create personas
- – analyzing your threat model so that the engagement operation will obtain the best results
- – or just defining when you should stop the operation (gating criteria)
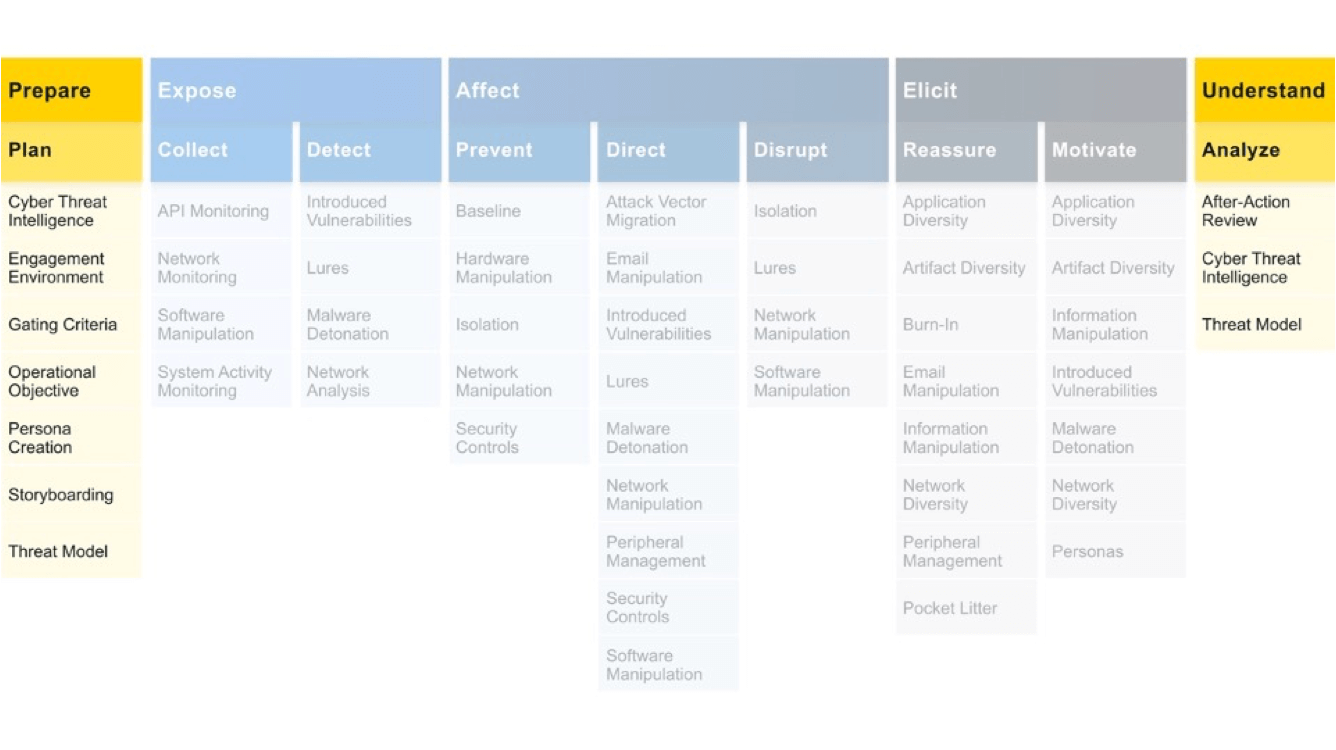
The other approaches are activities that are more related to the execution of the operation. Depending on your goals, you will use different activities, trying to improve your threat intelligence collection process.
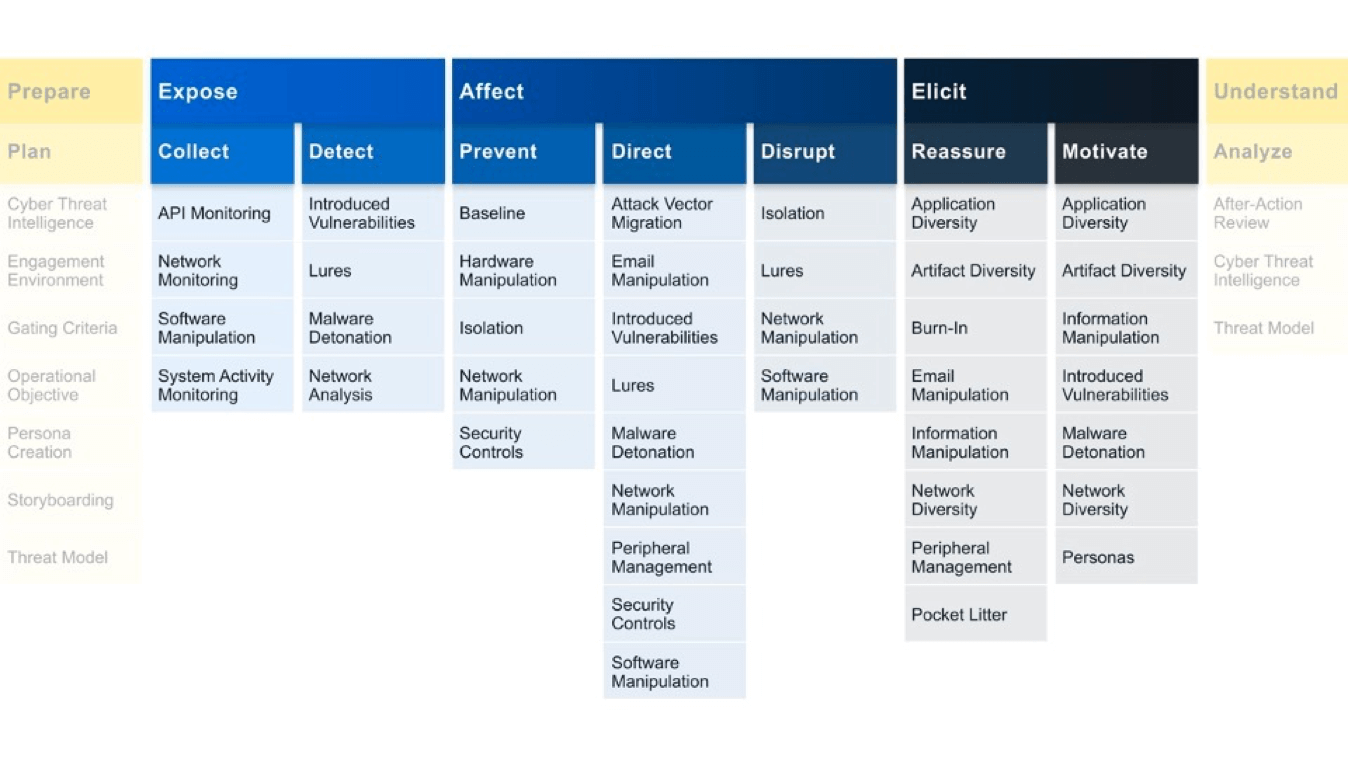
Mapping ATT&CK techniques
In adversary engagement operations, it can be tempting to try to anticipate the adversary’s actions. However, this line of thinking can lead the defender to make incorrect or ineffective decisions due to cultural, experiential, or any number of other differences. By mapping to ATT&CK, we can ensure that our chosen engagement activities are driven by observed and reported adversary behavior, not our expectations.
For each ATT&CK technique, we can examine the weaknesses revealed and identify an engagement activity or activities to exploit this weakness. For example, if we know that an attacker is performing a Remote System Discovery (T1018), we can start deploying decoys or lures (EAC0005) that will be found by the attacker.
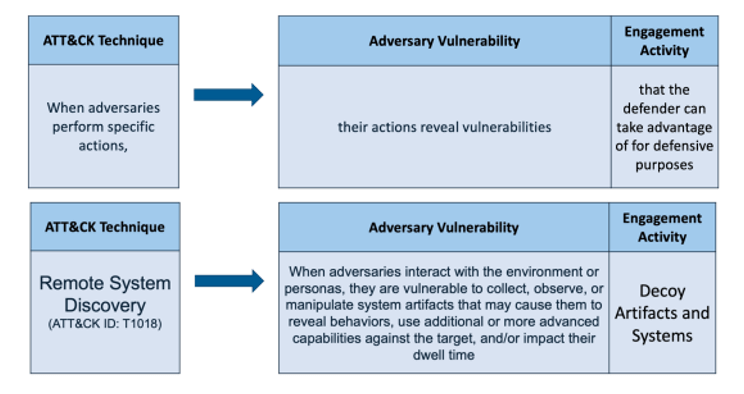
Other mapping examples
Let’s take the ACME organization as an example: the majority of their services are based on containers and some of them are exposed to the Internet. They know that sometimes a misconfiguration or a human mistake can expose not only those services, but the administration services that control the containers (for example, a Docker daemon). They also know that there is a specific threat actor (TeamTNT) that is targeting companies in their sector. Finally, they know that one of TeamTNT’s preferred compromise methods is to get control of Docker daemons connected to the internet.
In a previous blog post, we looked at the techniques they could use. The following table gives us a quick summary of all those techniques:
| Steps | ATT&CK Technique |
|---|---|
| TeamTNT scans your attack surface looking for unprotected Docker daemons | T1133 – External Remote Services |
| They create a new container with privileged mode, mapping the host’s root filesystem into the new container | T1610 – Deploy Container |
| Then they add a new SSH public key to the root user authorized keys | T1098-004 Account Manipulation: SSH Authorized Keys |
| They can now SSH into the host (ssh [email protected]) | T1611 – Escape to Host |
So if we try to map these ATT&CK techniques into Engagement activities, we get the following result:
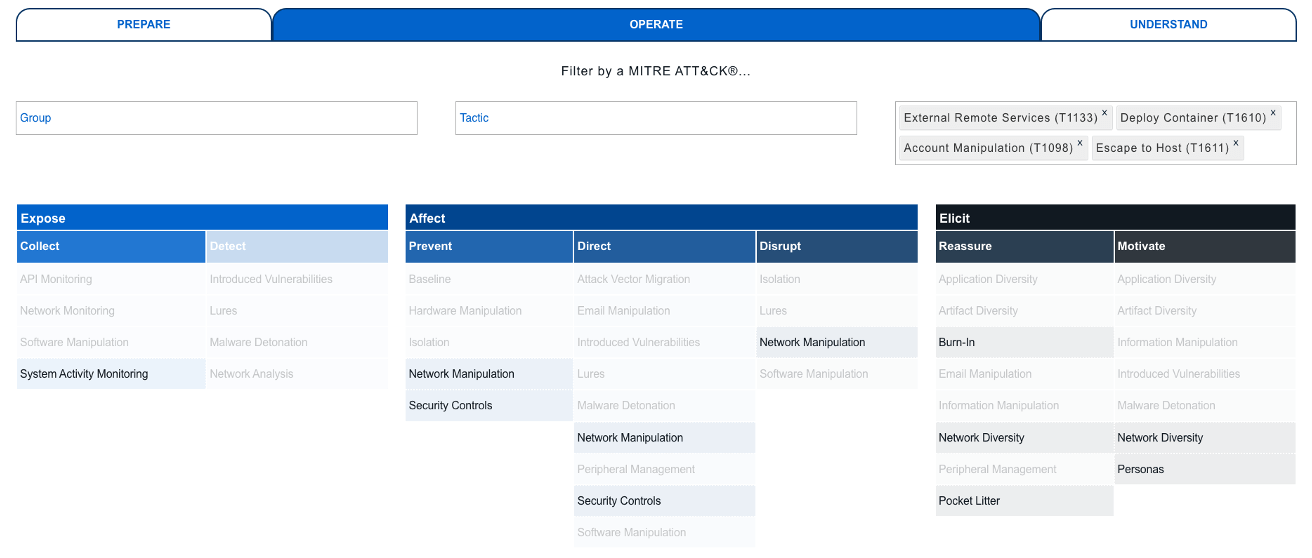
Let’s break down some of these activities so that we can better understand what they mean:
- – Security Controls (EAC0018): alter security controls to make the system more or less vulnerable to attack. In our example, we can change the Docker daemon configuration so that no authentication is needed for managing the containers.
- – System Activity Monitoring (EAC0003): collect system activity logs that can reveal adversary activity. In our example, we need to monitor the creation / deletion of containers, as well as the activity inside them.
- – Pocket Litter (EAC0011): data used to support the engagement narrative. We need to make our Docker server credible enough. One simple example could be to create other containers (like web servers, databases, etc.) so that it is similar to any other of our production Docker servers.
So, by using these engagement activities, we have made significant improvements in our security posture:
- – Receiving high-fidelity alerts when our Docker daemons are being compromised.
- – Collecting detailed threat intelligence about what that specific threat actor is doing in all the attack stages; pre-breach, collecting information about their discovery phase; how they are compromising our services; and what they do after the compromise. In this example, we can also gather more information about the containers they create, how they try to escape from a container to the host, or the binaries and C2C they are using.
In summary, mapping ATT&CK techniques to Engage activities can be a fantastic way to start engaging with our adversaries, as well as defining and running very tailored operations that will help to collect better threat intelligence.
If you would like to find out more about any of the topics discussed in this article, please get in contact with us. We are only too happy to explain what we do and how we can help you get the best out of deploying deception – from an initial conversation or simple demo, to a fully featured deployment.



David Barroso is a founder and CEO of CounterCraft. You can find him on LinkedIn.
