APIs are now your front door, and your team feels the pressure. That is exactly where attackers start, probing app-to-app flows for scope abuse, method fuzzing, and token misuse that still looks legitimate in production. With a deception-powered digital twin replicating your production environment, you can mirror those services and watch the behavior safely, then map what you see to MITRE ATT&CK, and turn early probes into clear signals your SOC can act on.
Modern threat response begins where attackers start: at your APIs. In today’s complex technology ecosystems, applications talk to each other more than they talk to people. Microservices, partner integrations, mobile back ends, and SaaS connectors all ride on APIs. That makes service-to-service identity and authorization scopes the master keys to your data and workflows. But traditional detection misses the app-to-app abuse
Independent industry reports from NIST and ENISA point to more probing at public-facing services and a widening gap between what teams can see versus what their APIs allow. That gap is widest in app-to-app flows, where client credentials, JWTs, and refresh tokens can be abused without tripping user-centric controls. At CounterCraft, we understand your pain.
With a deception-powered digital twin replicating your production environment, you can mirror those services, watch the behavior safely, map what you see to MITRE ATT&CK, and turn early probes into clear signals your SOC can act on immediately. That is the theory behind CounterCraft’s API Vulnerabilities & Targeting deception campaign, so read on to see how it works.
What is modern threat response?
Modern threat response is a proactive, behavior-first approach to threat detection that captures adversary intent early—before attackers touch production systems. Unlike traditional reactive security that waits for signatures or breach indicators, modern threat response uses deception technology and behavioral analysis to:
- Detect threats at reconnaissance stage: Catch attackers during initial probing and enumeration
- Generate high-fidelity signals: Create attacker-only alerts that eliminate false positives
- Map adversary behavior: Connect attack steps to MITRE ATT&CK for context-rich investigations
- Enable confident response: Give SOC teams clear narratives instead of ambiguous log entries
For API security specifically, modern threat response means safely studying how attackers abuse OAuth scopes, JWT tokens, and service-to-service authentication without risking your production data.
Where traditional detection fails : The app-to-app blind spot
Picture this: An attacker obtains a legitimate OAuth token for your calendar API. They quietly escalate from “read appointments” to “manage all mailboxes” by probing scope boundaries. Your logs show nothing unusual, just API calls from a valid token. By the time your team notices, sensitive data is already moving laterally across services.
Most traditional controls are tuned for signatures or human login failures, which is why app-to-app abuse continues to bypass security measures. It gets past for three primary reasons:
- Calls look legitimate. Tokens validate, TLS is clean, and every request appears to respect your schema. Attackers still exfiltrate by chaining “allowed” calls that break business logic. Traditional signature-based detection sees valid tokens and approved endpoints, missing the abuse pattern entirely.
- Service identities blend in. The client-credentials grant process has no human in the loop. Once a token is minted, lateral movement looks like routine automation. Recent guidance from Microsoft highlights how refresh-token abuse and OAuth requests against M365 and Teams APIs maintain persistence after an initial compromise.
- Recon reads like background noise. Method enumeration, parameter tampering, and low-and-slow fuzzing hide inside normal traffic. Research from Google Cloud shows adversaries increasingly use legitimate cloud services, so malicious activity resembles everyday operations.
When the signal is late or noisy, your SOC cannot move with confidence. The antidote is a behavior-first approach to threat hunting that creates clean, attacker-only, signals your analysts can trust. We expand on that mindset in Threat Hunting: Giving New Life to IOCs.
How modern threat response works: Digital twins for API security
So how do you turn vague API noise into evidence your investigators can trust without touching production? Modern threat response uses deception-powered detection to get the first clean signal.
A digital twin is an isolated replica that mirrors your real APIs but contains no actual data, a safe sandbox where attackers reveal themselves. It’s a high-interaction environment that behaves exactly like your production services but lives completely outside your critical infrastructure. For more detail on how digital twins play an important role in active defense, read our blog on digital twins.
Setting up your API digital twin
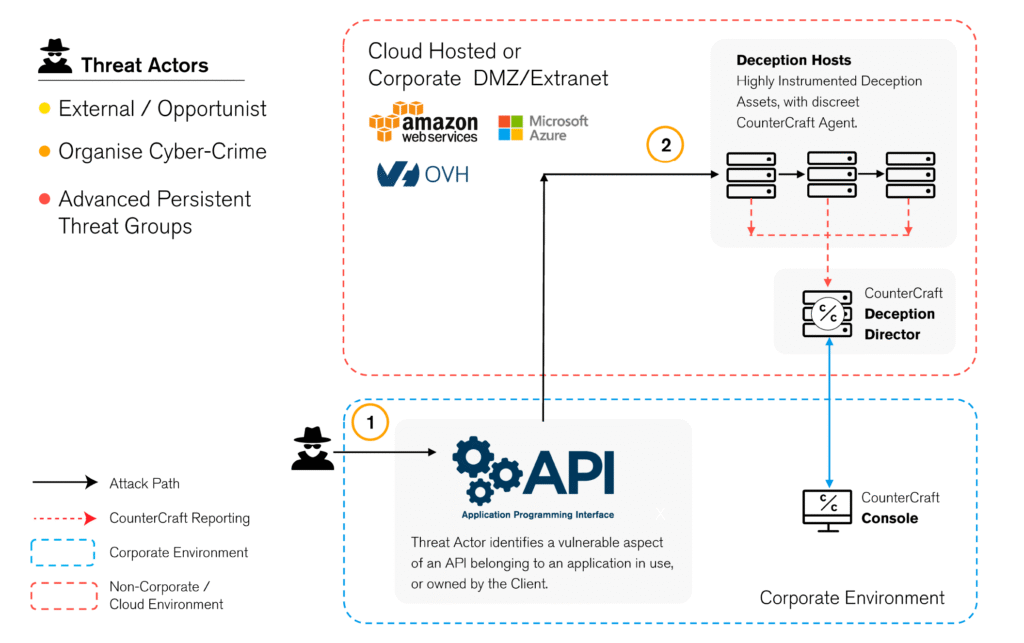
Start by running CounterCraft’s incredibly effective API Vulnerabilities and Targeting campaign.
This campaign uses deception to stand up a controlled, high-interaction digital twin of your APIs, and publish look-alike endpoints that behave like your real services, but that live safely outside production. When an adversary begins to probe, you capture intent, tooling, and next steps without putting your most sensitive data at risk.
The twin mirrors how your apps actually authenticate and authorize. It supports client credentials, signed JWTs, mTLS, and normal refresh behavior, and it exposes just enough objects and verbs to invite realistic reconnaissance. There is no real data behind it. Your team learns safely while the attacker reveals the scopes they ask for, the methods they test, and the pivots they attempt between services.
This is what an API Vulnerability and Targeting campaign looks like with deception:
What modern threat response captures
Once traffic hits the digital twin environment, patterns appear quickly. You see scope choreography where an actor tries to over-privilege access or chain permissions across services, a tactic that aligns with malicious OAuth activity reported in the field. You also see the slow, careful, method fuzzing and parameter tampering that production logs tend to bury. If a JWT is replayed or a refresh token is exchanged in a way that does not match your jobs, the twin records every step with the context analysts need.
The result is a coherent story your team can act on. You know what was tested, how the steps connected, and where the actor planned to go next. Instead of a pile of isolated events, you have an early, clean narrative that maps to MITRE ATT&CK and supports confident decisions. If you want a deeper explanation of why digital twins give you this longer, clearer view, see our analysis of why traditional malware sandboxes often miss the bigger picture.
Modern threat response in the SOC: What good looks like
Telemetry is effective only when it streamlines daily SOC operations. With digital twins in place, deception-derived events arrive in your SIEM and XDR already enriched. They include:
- ATT&CK tags
- the service that was targeted
- the method and parameters that were exercised
- the scopes that were requested
- the token context
- Timeline of attack progression.
Your analysts are not staring at a mystery, they are able to begin with a clear narrative that makes sense on the first read.
From there, investigations follow the actor’s path instead of a hunch. Starting from the initial decoy touch, the team pivots to the services that were tested, the exact scopes that were asked for, the methods that were fuzzed, and any tokens that were replayed. If nothing touched production, containment stays calm and local. If something did cross into a live system, responders know which service principals, secrets, and mTLS certificates to rotate first, and which integrations to restrict while they validate impact.
The last step is closing the loop with automated response. When a digital twin event confirms real abuse, SOAR can instantly revoke the refresh token, block the offending app registration, tighten a scope policy, or push a targeted gateway rule. The signal is clear and attacker-only, enabling your team to act decisively without creating collateral noise.
Why modern threat response matters right now
Three active trends make API-level modern threat response urgent.
- Malicious OAuth to bypass MFA.
Recent campaigns show attackers impersonating Microsoft OAuth apps, securing user consent, and minting privileged tokens that bypass MFA entirely. - Refresh-token abuse after initial compromise.
Microsoft’s October 2025 security guidance calls out refresh-token abuse and OAuth requests against Teams/M365 APIs as a growing tactic once an identity foothold exists. - Attackers hiding in cloud norms.
Google’s H2 2025 Cloud Threat Horizons shows adversaries increasingly abuse legitimate cloud services so their operations blend with expected traffic. Your twin separates signal from noise by design.
A digital twin gives your SOC the early, clean signal it needs to change the outcome. Modern threat response turns “invisible” API abuse into high-confidence alerts before damage occurs.
AI Summary
Building a modern threat response program: A three-step rollout
Start where you are and begin with the basics your team can control today. Modern threat response doesn’t require a complete security overhaul—it builds on your existing infrastructure.
Step 1: Establish Your Baseline
Take stock of public and partner-facing APIs and note how each one authenticates and integrates. Tighten the scopes that carry the most risk. Shift your permissions toward least privilege, shorten access token lifetimes, enforce stricter refresh token policies, and use mTLS on sensitive app-to-app flows.
This gives your analysts a safer baseline and reduces the room an attacker has to move. Document your current API surface area and authentication patterns—this becomes the blueprint for your digital twin.
Step 2: Deploy Your First Digital Twin
With that foundation in place, stand up a small pilot of the digital twin environment. Pick one critical microservice with a single partner path that has the highest value to the business. Mirror the endpoints, seed developer-style breadcrumbs in the places an intruder will look first, and ensure every event is mapped to MITRE ATT&CK and routed into SIEM and XDR.
Now your team can watch real behavior safely and begin investigations with context, not guesswork. This pilot phase validates your modern threat response capability and builds confidence in deception-derived alerts.
Step 3: Validate and Expand
Put the digital twin environment to work and grow with confidence. Run a controlled red team exercise that tests the scenarios you worry about most: method fuzzing, scope escalation, JWT replay, and client credentials abuse.
Validate that your analysts receive a single, high-confidence alert with a clear story they can brief to leadership. Share the KPIs (time to detect, false positive rate, mean time to response) with stakeholders. Agree on the next two APIs to mirror, and expand coverage step by step.
Each cycle strengthens policy, improves detections, and gives your team more certainty when it counts. Modern threat response becomes an iterative capability that grows with your API footprint.
CounterCraft is essential for modern threat response
CounterCraft’s API Vulnerabilities & Targeting campaign delivers modern threat response for your most critical APIs:
Mirror your APIs: Create high-interaction digital twins that replicate authentication flows, authorization scopes, and business logic
Seed breadcrumbs: Deploy developer-centric lures that only an adversary would touch—API keys in documentation, exposed endpoints in config files, overly permissive scopes in sample code
Generate actionable telemetry: Turn ambiguous probes into clean, attacker-only alerts with the threat intelligence needed to advance your cyber defense
Map to MITRE ATT&CK: Every event arrives tagged with relevant techniques—from Initial Access (T1078) to Credential Access (T1528) to Lateral Movement (T1550)
Stream to your stack: Events flow directly to SIEM, XDR, and SOAR so investigations always begin with clear intent
Modern threat response should give your analysts the signal quality they need to make confident decisions under pressure.
Ready to see how it works in your environment?
If your team is wrestling with API sprawl, partner integrations, and hidden app-to-app drift, the fastest path to clarity is a clean signal. Mirror what matters, watch the first probe, and turn it into intelligence you can act on. Modern threat response gives you the visibility traditional tools miss and the confidence to act before attackers reach production.
Book a personalized demo to see how a digital-twin deception campaign powers modern threat response for your APIs. Find out how you can deploy and get your first clean threat signal in minutes, not months.