MITRE has released Shield this August to great community approval. Shield is the defensive partner to the well known ATT&CK Matrix that defines threat actor activity. Shield is a set of defensive techniques that defend and protect against specific threat actor actions. This is a massive step forward for defensive teams in conceptualising and communicating defensive tactics, techniques and procedures. CounterCraft has already integrated the Shield Matrix and ATT&CK mappings into our proactive defensive platform. You can start using this information today. This article, by CEO David Barroso, explains in-depth where the value of Shield lies and how it is implemented in CounterCraft’s platform.

A few days ago, MITRE released the first version of Shield, a free knowledge base of common techniques and tactics that can help experts take proactive steps to defend their networks and assets. MITRE Shield takes a similar approach to presenting active defense concepts as MITRE ATT&CK®, a framework that catalogs adversary behavior and is widely used throughout the cybersecurity industry.
According to MITRE, “Shield was culled from MITRE’s work over the past 10 years observing and engaging adversaries in defense of their own network. It spans the range from big-picture opportunities and objectives that chief information security officers (CISOs) may want to consider to practitioner-friendly tactics, techniques, and procedures”.
This new framework is the missing piece of the blue teams’ puzzle, as it provides clear and well defined active defense techniques that can be used to improve our security status in different areas:
– Better threat detection: by applying these new techniques inside or outside your organization.
– Threat intelligence generation: by collecting data from adversaries that are targeting your organization.
– Adversary engagement: by deploying services and data, in real time, to influence their behavior.
Leveraging ATT&CK along with MITRE Shield offers the potential to create active defense playbooks to address specific adversaries. So by clicking on a particular adversary’s behavior in ATT&CK, defenders can quickly pull up MITRE’s recommended tactic and technique for dealing with that specific behavior.

Shield Tactics and Techniques
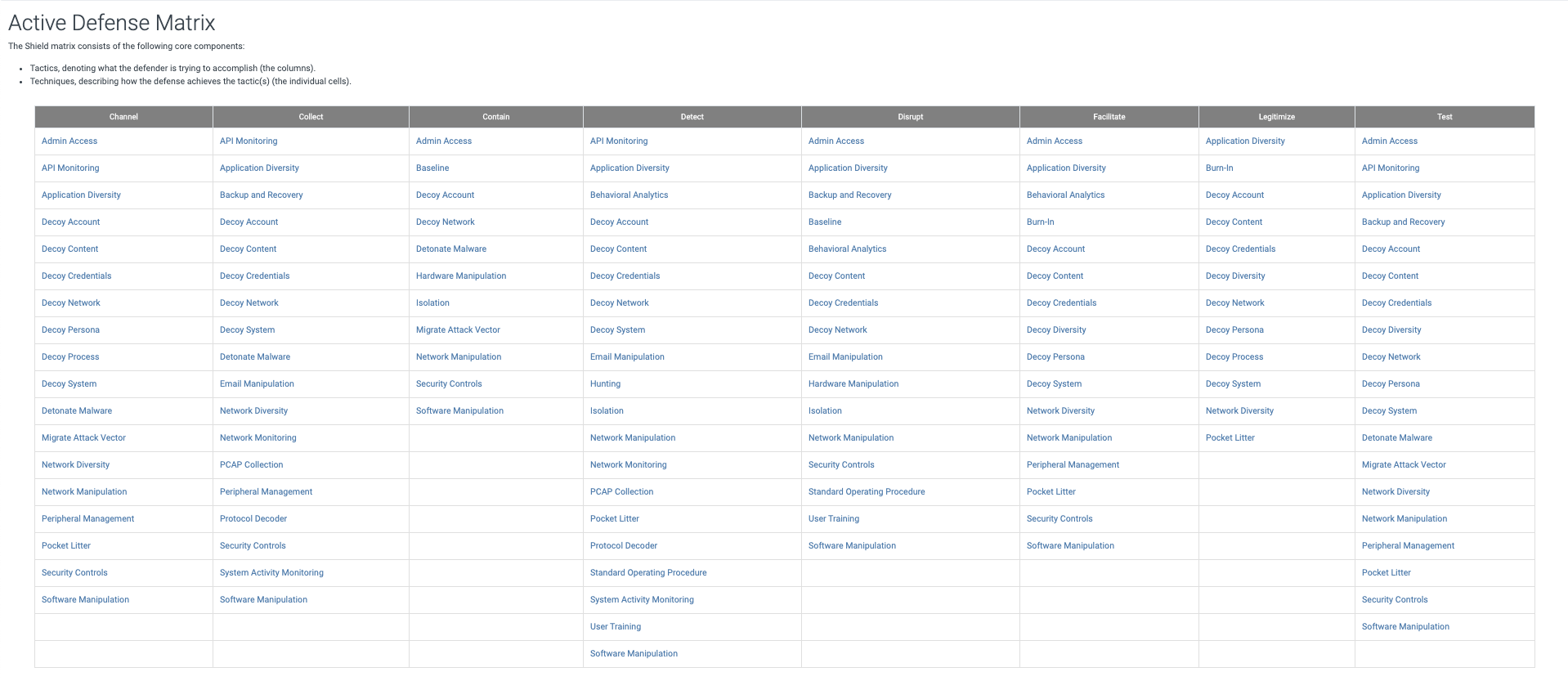
Similar to MITRE ATT&CK®, Shield also uses tactics and techniques. Tactics describe the desired effect of active defense activities and are useful to describe why a defender would choose to use a specific active defense technique. Techniques describe things that can be done (by defenders) in active defense. The detail page for each technique provides information about which tactics it supports, what opportunities are available based on adversary TTPs, as well as use cases and procedures to prompt implementation discussions.
Let’s have a look at one of the tactics and see how it works. There are other good examples in the ‘Getting started with MITRE Shield paper’.

DTA0002: Collect
The Collect (DTA0002) tactic is used to gather information about an adversary or their activity that can inform other defenses. It includes a number of techniques, from using decoys to network monitoring.
In our example scenario, let’s imagine that there is a specific threat actor that is searching for ways to compromise our organization by looking for external weak points.
We will then create a possible scenario to use several of those techniques combined to achieve our objectives:
– Creating a GitHub repository (Decoy Content – DTE00011) that belongs to your organization. This repository contains information about a Jenkins server.
– That Jenkins server is installed in a Decoy System – DTE00017 which is monitoring all operating system activity (API Monitoring – DTE0003) and all the system logs (System Activity Monitoring – DTE00034)
– Once an adversary compromises the Jenkins server, the adversary will find some Decoy Credentials – DTE00012 belonging to a Windows 2019 server in Azure (DTE00017, DTE0003, DTE00034).
– The adversary will then connect to the Windows 2019 server through RDP. We’ll create some Office documents describing a new strategic but fictitious project (Decoy Content – DTE00011) so that the adversary can find them.
This example scenario can offer a number of Shield opportunities:
–DOS0001– There is an opportunity to study the adversary and collect first-hand observations about them and their tools.
– DOS0005 – There is an opportunity to deploy a tripwire that triggers an alert when an adversary touches a network resource or uses a specific technique: any connection to the Jenkins server.
– DOS0074 – There is an opportunity to influence an adversary to move toward systems you want them to engage with: our GitHub repository will help.
– DOS0082 – There is an opportunity to introduce data to an adversary to influence their future behaviors: the Office documents.
– DOS0084 – In order to prolong an adversary engagement operation or enable detections, there is an opportunity to introduce credentials to an adversary that you want them to collect and use: the Windows 2019 RDP breadcrumb.
– DOS0133 – In an adversary engagement scenario, there is an opportunity to observe how an adversary might manipulate data on a system: deep telemetry in the Decoy Systems and Applications.
– DOS0190 – In an adversary engagement scenario, there is an opportunity to introduce decoy content to entice additional engagement activity: the Windows 2019 RDP breadcrumb.
– DOS0199 – In an adversary engagement scenario, there is an opportunity to introduce decoy systems that can influence an adversary’s behavior or allow you to observe how they perform a specific task.
– DOS0208 – There is an opportunity to feed content to an adversary to influence their behaviors, test their interest in specific topics, or add legitimacy to a system or environment: the Office documents.
And those opportunities totally fit in the following use cases:
– DUC0007 – A defender can use a decoy system running a public-facing application to see if an adversary attempts to compromise the system and learn their TTPs.
– DUC0034 – A defender can use a decoy system to see if an adversary exploits vulnerable software in order to compromise the system.
– DUC0074 – A defender can create breadcrumbs or honeytokens to lure the attackers toward the decoy systems or network services.
– DUC0184 – A defender can utilize decoy files and directories to provide content that could be used by the adversary.

Shield in CounterCraft’s Deception Director
CounterCraft’s Deception Director is an active defense platform that helps in the design, deployment and monitoring of deception campaigns. Those campaigns can be considered as a set of different Shield use cases (and different Shield opportunities). In our example, we will have one deception campaign (the GitHub/Jenkins/Windows 2019 attack tree) that will consist of two deception hosts (a Linux server for Jenkins, and a Windows 2019), two services (Jenkins and the RDP), and three different set of breadcrumbs (the GitHub repository, the Windows 2019 RDP access details and the Office documents).
We have added the Shield matrix in different places of the application so that we can show which tactics and techniques are covered.

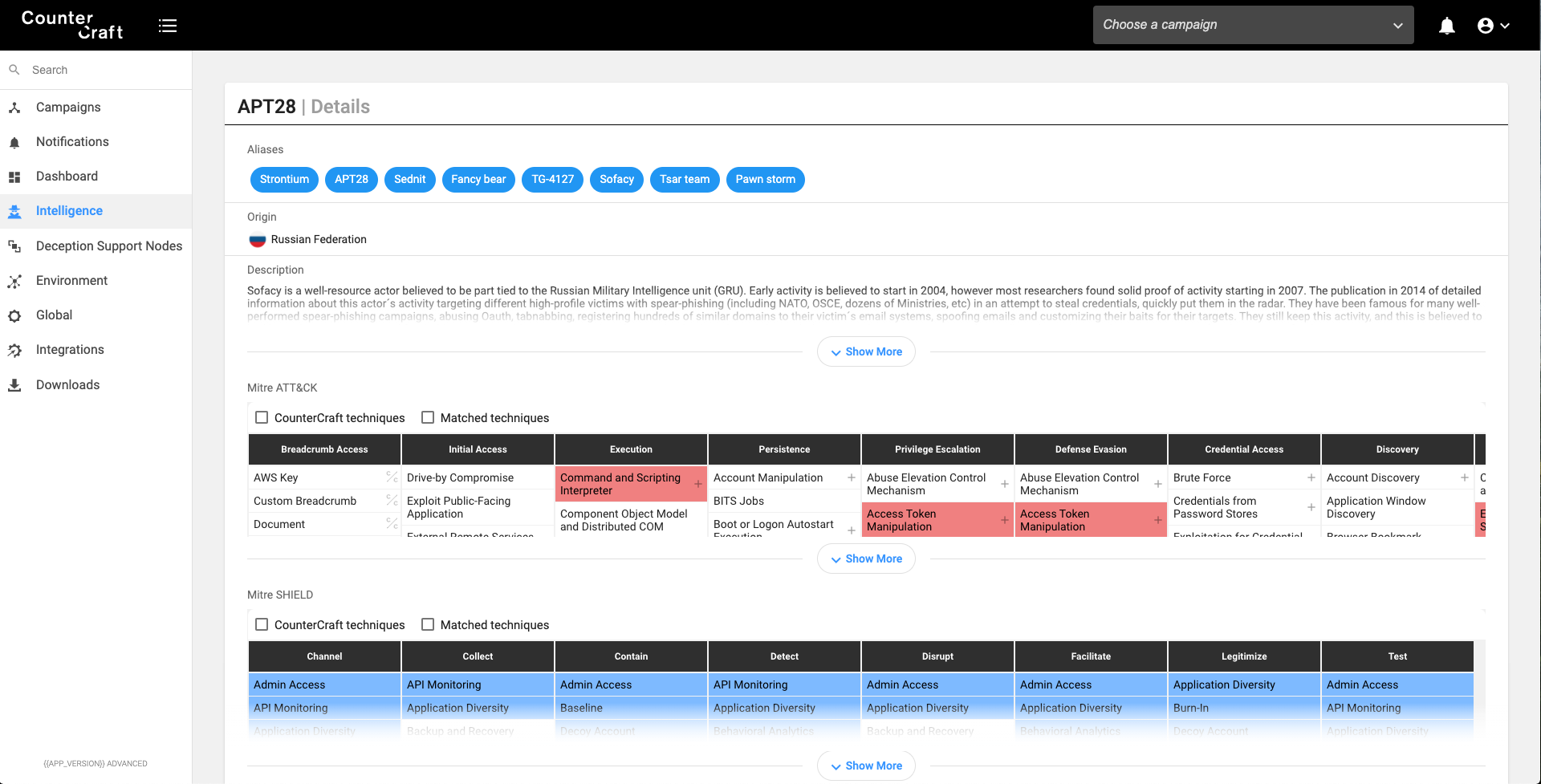
Threat Actor Database
We could start having a look at our threat actor, in order to know which ATT&CK TTPs they use, and which Shield TTPs could be used against them. We can use the ATT&CK mapping provided by Shield in order to select the techniques that can be used by the blue team against this specific threat actor.
In this screenshot you can see our threat actor information database showing the ATT&CK Matrix (Red) associated with the threat actor and the Shield matrix (Blue) highlighting specific defensive techniques that would apply to this actor.

Campaign Catalogue
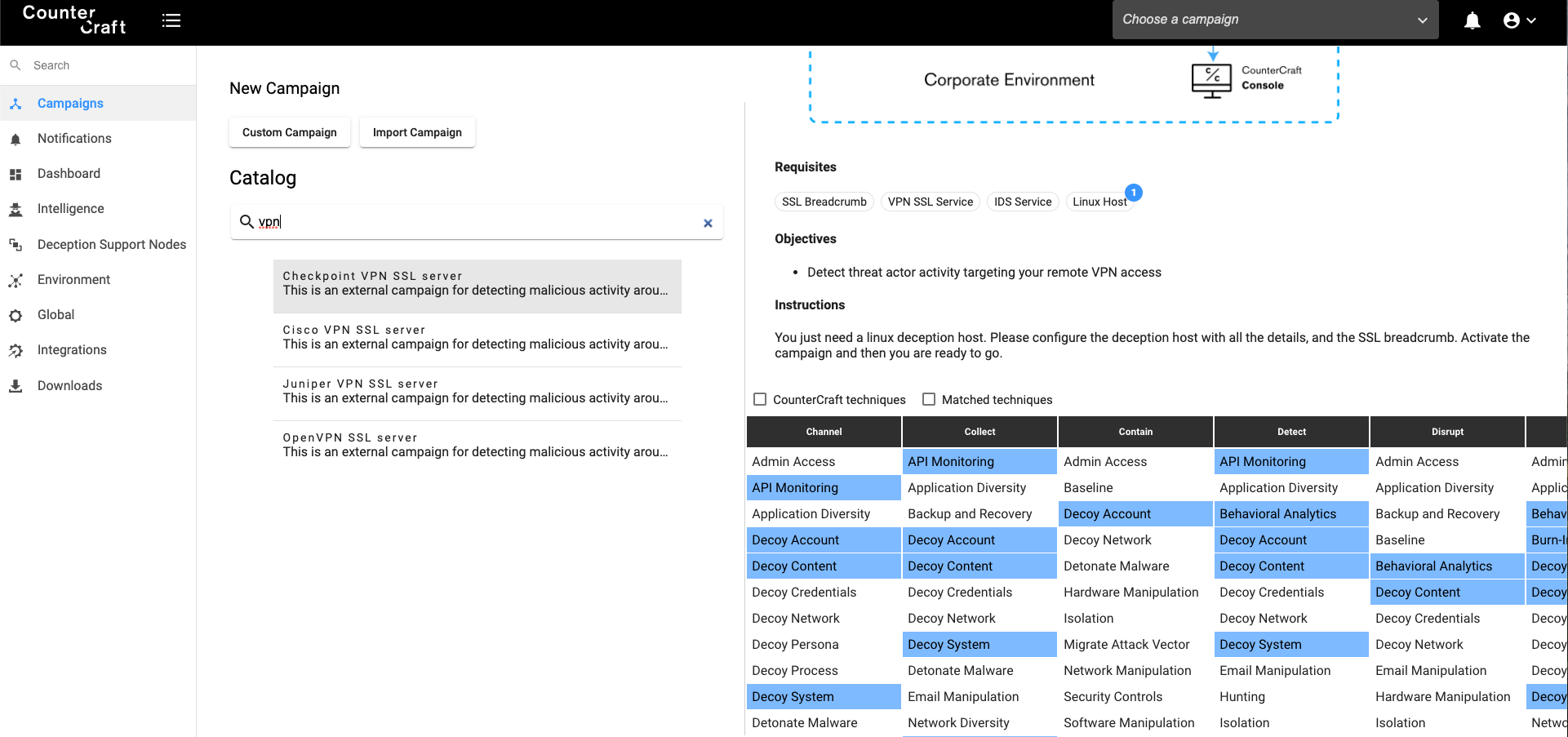
Once we have checked the Shield techniques that we should use, then we can choose any campaign from our catalogue that fits with those techniques. The Campaign Catalogue provides ready made campaigns to start you on an active defense journey using CounterCraft.

Campaign Builder
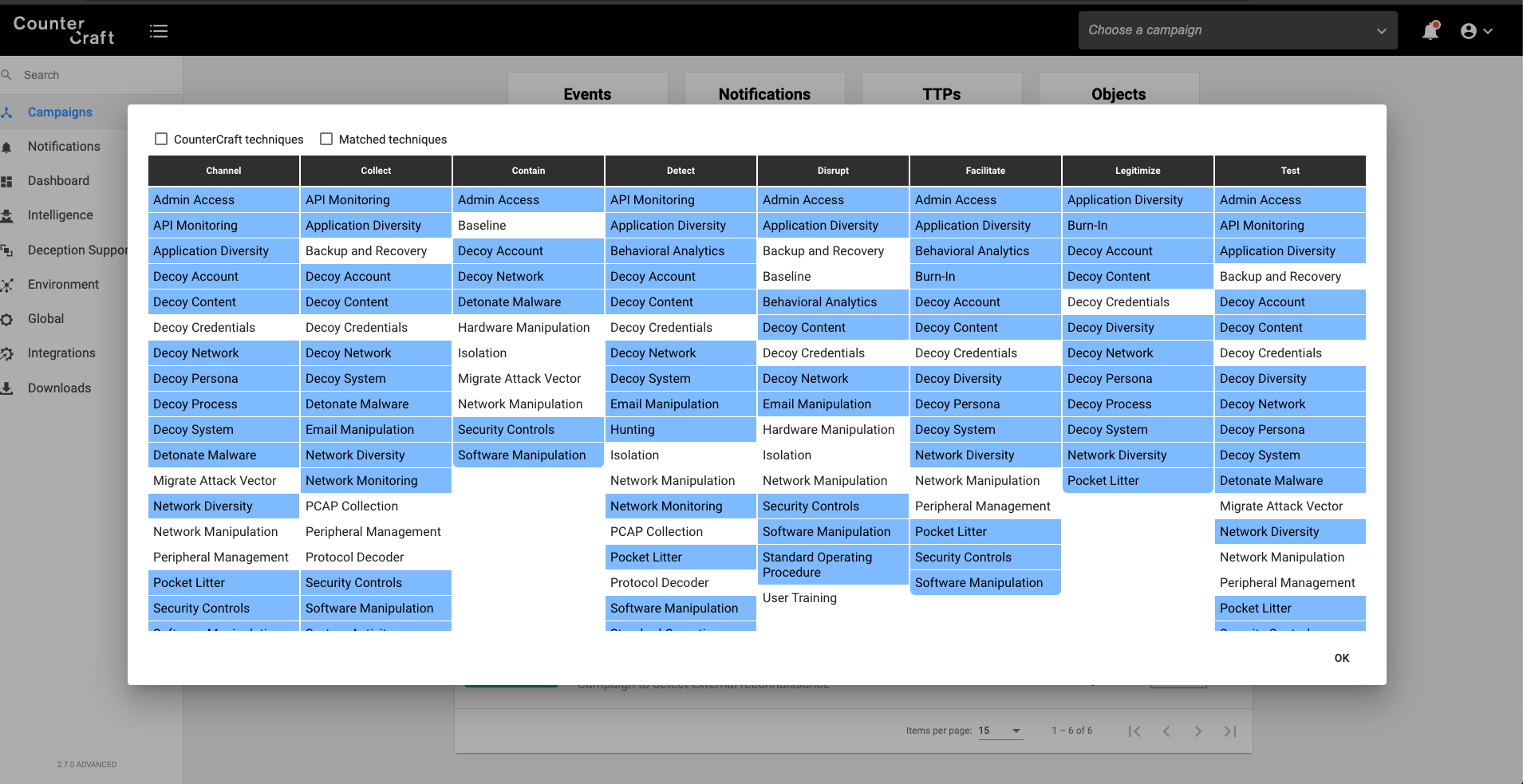
We can then add deception hosts, services or breadcrumbs to our fresh new campaign that will include new Shield techniques, depending on the type of the asset. For example, we can add the technique DTE00019 – Email Manipulation by adding an Office365 or Google Suite service to our current campaign.
This screenshot shows all the Shield techniques that are facilitated by the current campaign, useful for checking that your campaign is covering the defensive areas you need.

Deception Environment
Now we can have a look at all the Shield tactics and techniques covered by all our deployed campaigns. CounterCraft allows you to deploy more than one campaign at a time so you can defend against different adversaries and threats (internal and external) at the same time.

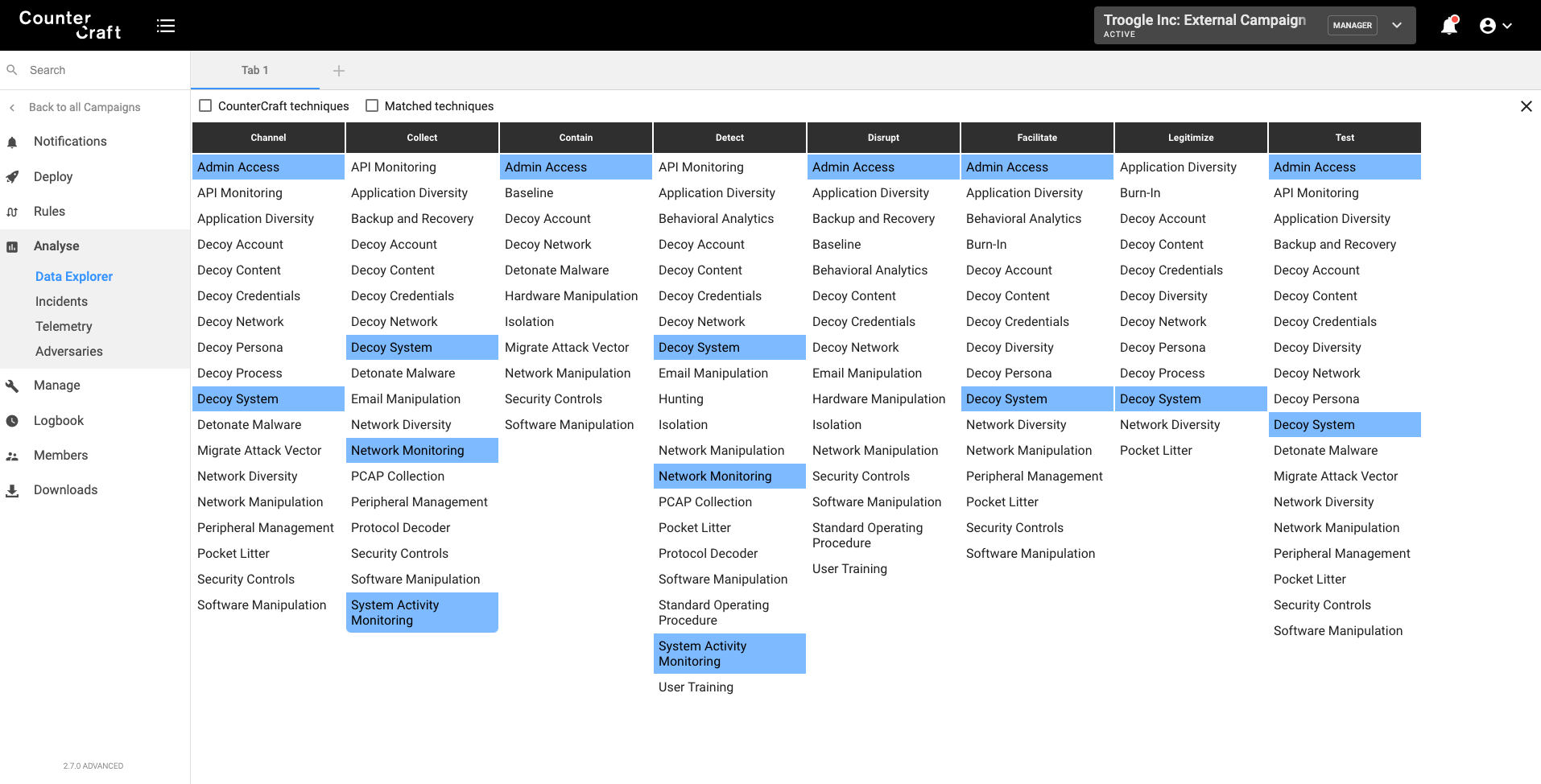
Data Explorer
When we integrated MITRE ATT&CK in our data explorer (that is getting all the events from the campaign) it was a great feature that helped to visualize all the TTPs originated in the campaigns.
Now, thanks to the ATT&CK -> Shield mappings, we can map all the ATT&CK TTPs detected into Shield TTPs.
This is like a real-time map of what you should be doing to defend against attacks in progress. CounterCraft detects attacks and collects intel. The intel is processed and enriched to give you IOCs and further insight such as these defensive recommendations.

Summary
As we have seen in this blog post, the release of MITRE Shield is a fantastic opportunity to improve our active defense strategies. Active defense ranges from basic cyber defensive capabilities to cyber deception and adversary engagement operations. The combination of these defenses allows an organization to not only counter current attacks but also to Learn more about that adversary and better prepare for new attacks in the future.
