Attackers bypass MFA by hijacking SaaS sessions and OAuth tokens, then blend in as trusted users. Deception-powered threat hunting deploys high-value breadcrumbs and twin OAuth flows to trigger clean, ATT&CK-mapped signals that cut triage time and stop abuse before data moves.
Your team has multi-factor authentication. You’ve trained users on phishing. You monitor your logs. And attackers are still getting in through session hijacking.
Here’s how: They’re stealing OAuth tokens and session cookies. Once they have a valid token, they don’t need to crack passwords or bypass MFA: they already look like a legitimate user. Your logs show normal activity. Your alerts stay quiet. And they’re inside, browsing files, reading emails, and mapping your environment.
Session hijacking has become a primary attack method because it completely bypasses traditional authentication controls. Recent incidents show attackers using stolen session tokens from third-party integrations to access CRM systems like Salesforce, exfiltrate data, and even delete audit logs to cover their tracks. Microsoft reported detecting 147,000 token replay attacks in 2023, representing a 111% increase year-over-year.
Microsoft reports a continued increase in consent phishing attacks, where users are tricked into granting malicious applications access to their data. Once an attacker has that access token, they can operate for days or weeks without triggering a single alert.
The real problem? Traditional detection can’t tell the difference between a stolen token and a real user. API calls look valid. IP addresses seem normal. Everything appears legitimate because technically, it is.
Why Traditional Detection Fails to Prevent Session Hijacking
After a token is stolen and replayed, attackers move carefully. They list users and check permissions, which looks like normal admin work. They enumerate files and mailboxes, which looks like someone searching for a document. They test API scopes, which looks like a developer checking access. They use residential proxies, so it looks like someone working from home.
Your SIEM might flag it as “unusual activity,” but unusual isn’t the same as malicious. SOC analysts are left guessing: Is this a real threat or just someone working odd hours?
This is the gap deception technology fills. Instead of trying to guess intent from ambiguous logs, you plant something in the environment that only an attacker would touch. When they touch it, you know instantly.
How It Works : A Deception Campaign
CounterCraft uses deception technology to protect your environment by creating a digital twin, a replica of your SaaS and OAuth patterns that lures attackers away from your real systems.
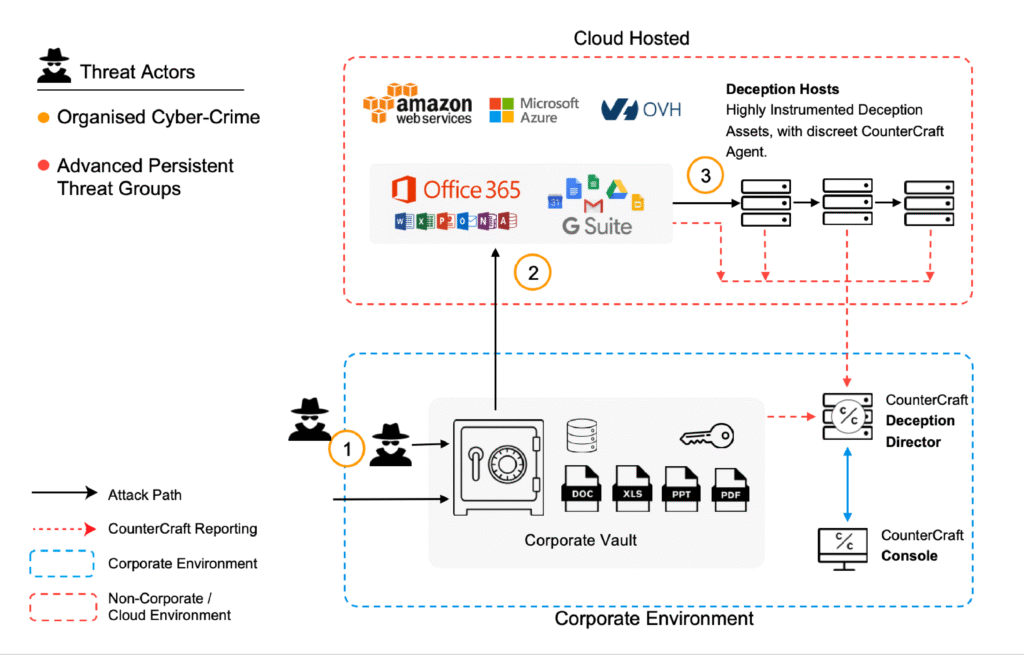
The Campaign : High Value Breadcrumbs for Sessions and Identity
This campaign plants realistic, instrumented credentials in places where attackers typically hunt during reconnaissance. Think browser caches, code repositories with OAuth examples, cloud drive folders labeled “API Keys – DO NOT SHARE,” email drafts containing session tokens, or helper tool configuration files. These are honeytokens—they look valuable but are completely harmless to your business.
The objective is threefold: identify when data and credentials are stolen from areas that should be secure, receive immediate reports when documents or credentials leave your corporate environment when they shouldn’t, and observe how attackers operate once they engage with your highly instrumented deception hosts.
When someone uses one of these breadcrumbs, that’s your definitive signal. No legitimate user has any reason to touch them. From that first interaction, you can follow the entire story—which scopes they requested, which APIs they tested, the order they moved through your environment, and what tools they used. Everything maps cleanly to MITRE ATT&CK frameworks (T1528: Steal Application Access Token, T1550: Use Alternate Authentication Material), so you’re not guessing at intent, you’re documenting their exact playbook in real time.
Learn how you can deploy this campaign today by requesting a demo.
What This Gets You
- Alerts you can trust. Deception events arrive in your SIEM already tagged with MITRE ATT&CK techniques, target application, requested scopes, timeline, and full context. Your XDR playbooks trigger automatically because the signal is unambiguous. No more analyst time wasted chasing false positives.
- Investigations that start with proof. An analyst sees the decoy token was used, then pivots to which user account the attacker tried to impersonate, which device and IP they used, and whether they touched any production systems. If they hit production, you know exactly which scopes and data to contain. If they don’t, you stay calm and focused.
- Better defenses for everyone. Each attack teaches you something new—which app IDs are used in malicious consent flows, unusual user agent strings, preferred scope combinations. This intelligence feeds your identity protection systems, CASB, and email controls. Your deception program becomes a source of new detections, not just a consumer of alerts.
- Justification for hardening. You get proof that tighter token controls work: shorter access token lifetimes, stricter refresh token policies, continuous re-authentication for high-risk scopes, phishing-resistant MFA. When leadership asks if these controls are worth the friction, you have data showing they stop real attacks.
Why Preventing Session Hijacking Matters Now
Session hijacking attacks are accelerating. In 2024, 73% of session hijacking incidents targeted cloud-based enterprise platforms, with attackers leveraging stolen tokens for lateral movement across networks. Major incidents involved consent phishing campaigns targeting Chrome extensions with 2.6 million users affected, and OAuth token theft via third-party integrations leading to data exfiltration across multiple SaaS platforms.
The consent phishing protection market is projected to grow at 15.3% annually through 2033, reflecting how seriously organizations are taking this threat. The U.S. government has taken notice too: a 2025 White House Executive Order specifically mandated new federal guidelines for securing session tokens.
You can’t wait for credential failures or impossible travel alerts to catch session hijacking. By then, data is already moving. You need a signal that arrives early and can’t be faked.
A Real Example
An attacker tricks a user into granting a malicious app “read mail” and “read files” permissions in Microsoft 365. They get an access token and a refresh token. They list mailboxes, check shared drives, and start exfiltrating samples. This looks completely normal.
With deception in place, during their reconnaissance, they encounter a credential in a browser cache. They try it. Immediate alert. They attempt to access a look-alike OAuth endpoint for elevated scopes. Second alert.
Your SOC gets the full picture: suspicious app consent attempt, token replay against a decoy endpoint, scopes requested, IP, device, and user agent, plus MITRE ATT&CK techniques involved. Response targets the at-risk user and scopes. No guesswork. No haystack. You have proof.
AI Summary
How CounterCraft Helps Prevent Session Hijacking
CounterCraft’s approach utilizes deception technology to safeguard your environment by replicating it as a digital twin, a replica of your SaaS and OAuth patterns that lures attackers away from your real systems.
We place high-value honeytokens where attackers look during reconnaissance. When they engage, our digital twins hold their attention long enough to capture their full toolchain, scope requests, and next moves. Everything maps to MITRE ATT&CK and routes directly into your SIEM, XDR, and SOAR.
Investigations start with intent. Events are definitive. And your SOC gets the context they need to act fast.
Ready to see this in your environment?
If you’re dealing with SaaS sprawl, app-to-app drift, and too many vague alerts, the fastest path to clarity is a definitive first signal. Plant something only an attacker will touch. When they do, you’ll have irrefutable proof—and the speed to stop them before data moves.
Book a demo to see how deception-powered detection stops session hijacking and OAuth token theft.