According to a recent article in the Financial Times, worries about attacks on the SWIFT banking platform have only grown since the Russian invasion of Ukraine, which prompted the ousting of seven Russian banking lenders from the global payment network.
Additionally, in compliance with EU Council Regulation (EU) 2022/398 of 9 March 2022, SWIFT disconnected three Belarusian entities (and their designated Belarus-based subsidiaries) shortly thereafter. These sanctions have prompted Russia to work on creating a replacement for SWIFT, the CELLS industrial blockchain, which appears to be nearing readiness. They have also sparked widespread worry about retaliatory attacks on the SWIFT network by Russia and its allies.
SWIFT is an attractive target because of how it links the entire global financial network. More than 11,000 financial institutions use the system, and trillions of dollars in transactions pass through it every day.
Threat actors with access to an individual bank’s SWIFT network have the keys to a gold mine. Insiders or other cyber criminals prowl around networks, and for those that are financially motivated, SWIFT credentials are a major target. Fortunately, cyber deception offers protection against lateral movement and insider threat in the financial.
The Temptations & Rewards of SWIFT for Threat Actors
If threat actors can penetrate a single bank, that grants them access across third-party systems and networks, meaning the whole system is only as strong as its weakest link. Small banks in developing countries often do not have the security in place to stop sophisticated attacks. This was the case in 2016 with the Bangladesh Central Bank hack, but more about that later. Member organizations of SWIFT must harden their security to protect and prevent fraudulent attempts by threat actors.
When an insider or someone with access credentials gains access to a bank’s SWIFT network, they have unlimited capabilities to make financial transfers. Catching the threat actors that are attempting access can prevent fraudulent transfers of money, in addition to serving as tempting bait for insider threats.
Historically High Stakes: The Bangladesh Hack & the Security Response
Historically, the most important exploit has been the 2016 Bangladesh central bank hack. Attackers were able to make off with $81 million after exploiting a vulnerability in a single bank via SWIFT, using a malware to send payment requests under the guise of various banks in the system.
As a result of this hack, SWIFT’s 2016 profit before tax and rebates to its owner-customers fell by 31 percent to 47 million euros ($53 million)1, an incredible loss for the financial giant. The cost of additional investments in security together with the money lost resulted in a big financial blow. This is just one anecdote of many (see the Carnegie Endowment’s exhaustive list of cyber incidents involving financial institutions).
In response to this attack, SWIFT introduced its Customer Security Controls Framework (CSCF), a set of mandatory and advisory security controls for SWIFT users. These controls finally established a security baseline for the entire banking community, mandatory to be implemented by all users on local SWIFT infrastructure. This necessary step for risk reduction resulted in tangible security gains, and it continues to be updated according to changes in threats.
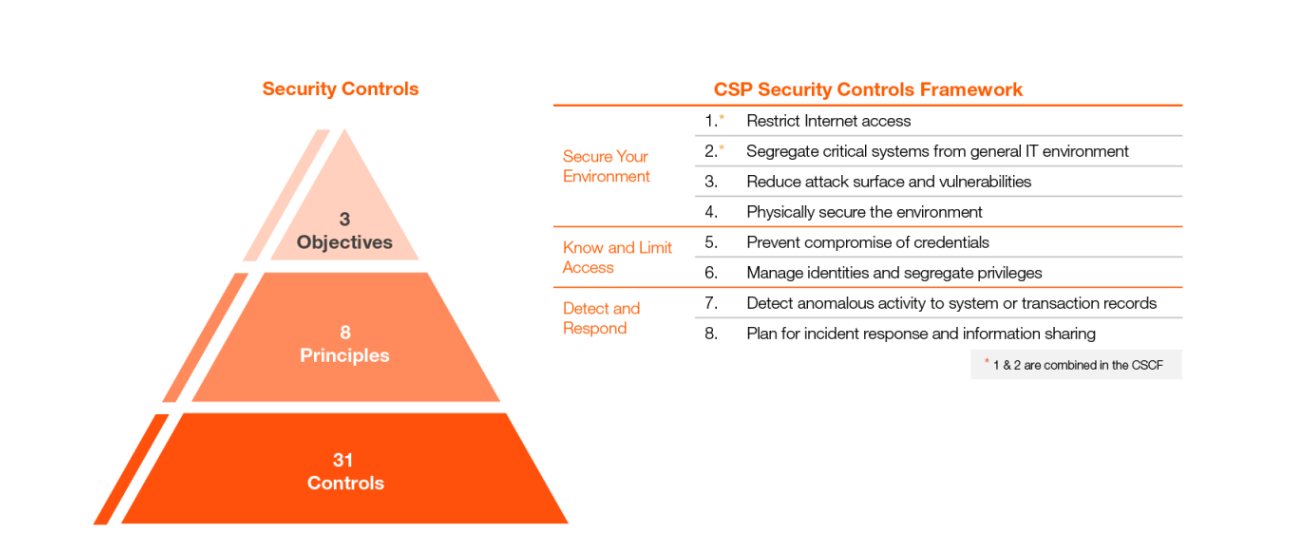
The security framework for SWIFT consists of three pillars: Secure Your Environment, Know and Limit Access, and Detect and Respond.
To secure the environment, SWIFT recommends the following four actions:
- Restrict Internet Access
- Protect Critical Systems from the General IT Environment
- Reduce Attack Surfaces & Vulnerabilities
- Physically Secure the Environment
To know and limit access:
- Prevent Compromise of Credentials
- Manage Identities & Segregate Privileges
And for detection and response:
- Detect Anomalous Activity to Systems or Transaction Records
- Plan for Incident Response & Information Sharing
SWIFT has also published CSCF v2022 for attestation with revised objectives and requirements.
Using Cyber Deception to Protect from SWIFT-Related Attacks
Cyber deception is an excellent tool in the protection of high stakes, complex networks. By using deception-based threat detection, organizations can dramatically reduce the risk of fraud and other targeted attacks that use the SWIFT network.
Now, we will look at an example of a campaign designed to detect threat actors or insider threats in your network looking for access to SWIFT networks. It allows organizations to identify the data the adversary is seeking and the tools they are using to get there.
This campaign is based around detecting insider threats within the financial sector — where the chief objective of an attacker is fraud or financial crime. The adversary has already gained access to the network and is in the initial stages of internal reconnaissance.
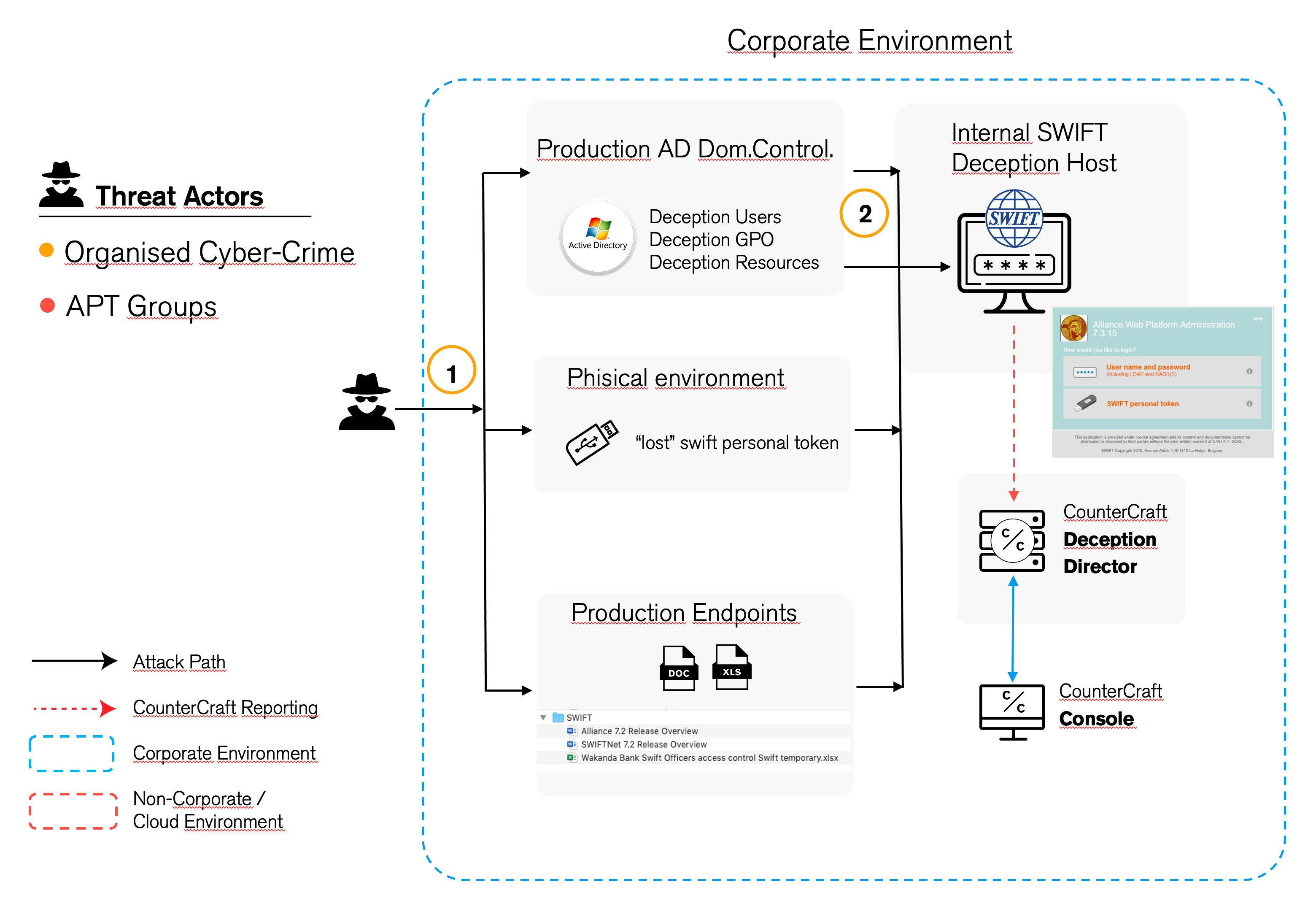
The idea of the deception is to leave a convincing trail of breadcrumbs that point to the SWIFT portal. This is achieved by the clever distribution of breadcrumbs using different mechanisms that not only deflect the attacker from production resources into a deception environment, but also provides valuable intel on the point of compromise, such as vital fingerprints for further investigation and also the ability to respond to the attack before a serious breach occurs.
The campaign is split into two basic phases:
Phase 1
The attacker is in the initial discovery stage of their attack. They try to access the production system via an Active Directory domain control. The attacker finds decoy users, GPOs (Group Policy Objects) and other deception assets. In addition, breadcrumbs have been distributed on production endpoints that also point to the SWIFT terminal. These breadcrumbs can take many forms but will provide traceable credentials. These credentials are unique for each endpoint, and they are automatically generated using a simple template configuration. As each credential is unique, it is easy to trace where the initial compromise was made and follow the path the attacker is taking.
Phase 2
The deception is the actual SWIFT terminal itself. Using an integrated deception service, it is simple to set up a credible SWIFT portal. The portal itself has a login function that corresponds to the distributed credentials and fake users that have been planted.
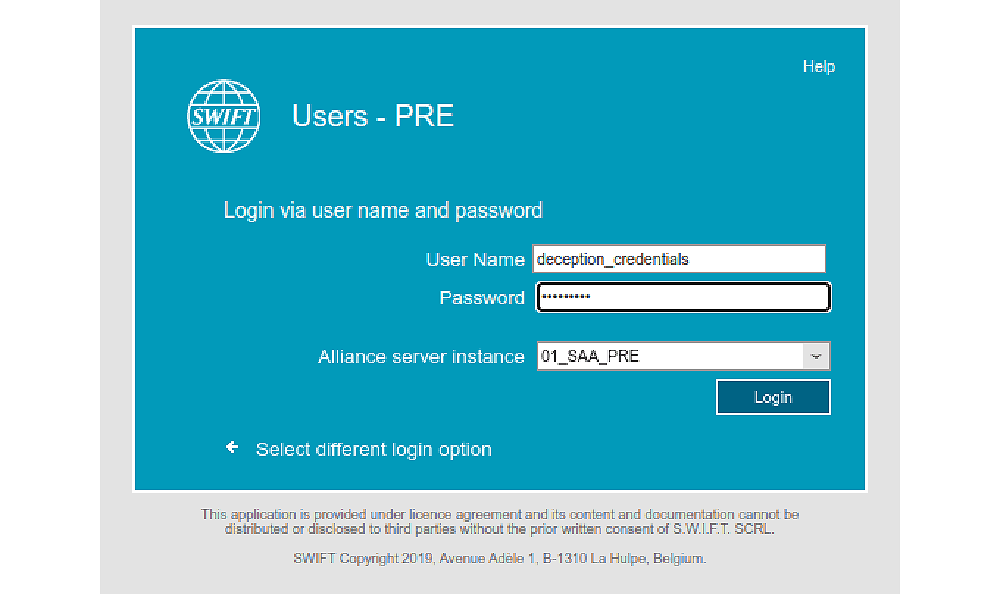
Screenshot of the deception SWIFT portal, and a login as “deception user” and password “evil_insider”
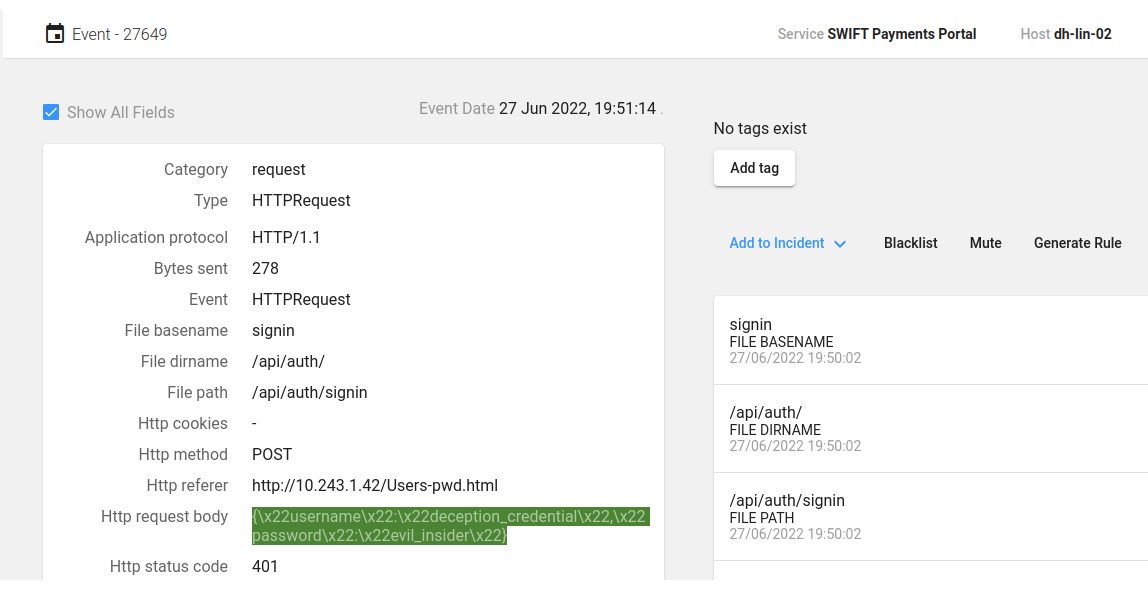
When the attacker connects to the web portal, an automatic alert is generated, and the credentials are collected. In addition, the source IP address and user-agent of the attacker will be captured. This means that in a matter of seconds it is possible to trace not only where the attacker has been (the source of the credentials) but also from where they launched their attack and the type of device they are using.
Screenshot showing the username and password are captured by the CounterCraft platform
The result of this campaign, which has been proven effective in real-life scenarios, is not only detection—it also provides deflection away from vulnerable production services and, more importantly, real-time actionable threat intelligence about the threat actors. For organizations not using SWIFT, this can also be adapted and used for any payment system. This enables financial organizations to respond immediately to an attack and to use the data to eliminate the risk that this attack vector is viable for future attacks.
This campaign also fills at least two key directives of the SWIFT network security framework (mentioned above):
- Detect & Respond: 7. Detect Anomalous Activity
- Know and Limit Access: 5. Prevent Compromise of Credentials (By detecting & measuring use of fake credentials)
It also aligns with the broader security strategic controls of Securing the Environment, meaning not only does it assist organizations with learning more about threat actors targeting them, it also brings them closer to alignment with the security directives and recommendations of SWIFT itself.
Read more about how cyber deception can protect financial industry networks, here.
Source:
1https://www.reuters.com/article/us-banks-swift-cybercrime-idUSKBN1910FX