Discover how deception technology identifies the early warning signs of ransomware – specifically during the discovery and lateral movement phases – so you can neutralize the threat before serious damage occurs.
Your system is locked. Your files have disappeared. All you have is a note from your attacker asking for an eye-watering ransom. It’s a horrible feeling, and for most security teams, the start of the incident.
But long before the adversaries encrypt your files, they’ve likely been roaming around your environment undetected, abusing credentials, escalating privileges, exploring routes to your most critical assets. If only you could’ve stopped them then, before they did the real damage.
Despite years of investment in cybersecurity tools and staff awareness, ransomware remains one of the most persistent cyber threats that organizations face. Verizon’s 2025 Data Breach Investigations Report found that ransomware was present in 44% of all data breaches, up from 32% in 2024. Sophos’ State of Ransomware 2025 puts the average recovery cost from a ransomware attack at $1.53 million.
But there’s a solution. With deception, you can stop ransomware attackers in their tracks, neutralizing them before they encrypt.
Ransomware Defense: It’s Not Just About the Lock
Ransomware tactics have evolved. Encryption remains a threat, but it is no longer the default choice. Sophos reports that in 2025, data encryption occurred in only 50% of ransomware attacks, down from 70% in 2024. Data exfiltration and extortion now deliver equal or greater leverage. More threats increase the likelihood that the organization will pay the ransom.
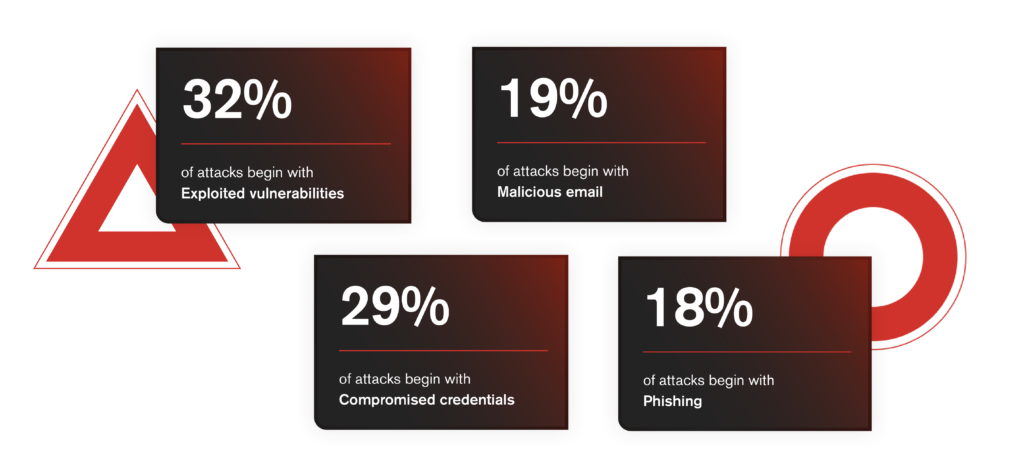
Whatever the end goal, the root causes of ransomware attacks remain consistent. Attackers gain entry through preventable weaknesses:
- Exploited vulnerabilities – 32% of attacks begin this way
- Compromised credentials – 29%
- Malicious email – 19%
- Phishing – 18%
Once inside, attackers focus on understanding the environment and expanding access privileges without detection. That way, they can maximize their leverage beyond anything encryption alone could deliver.
As well as the financial impact, ransomware attacks also have a human cost. Sophos found that 41% of IT and cybersecurity teams experienced increased anxiety and stress about future incidents.
SOC teams face constant pressure to respond faster to alerts with less tolerance for false positives. They do not need more tools that add to the noise. Rather, they need earlier, cleaner signals that boost confidence and minimize damage.
The Critical Gap in Ransomware Prevention: Discovery and Lateral Movement
Once an adversary gains access to the environment (however they got there), they do not rush to encrypt and demand a ransom. Instead, they take time to understand where they are and what they can reach. They achieve this during two phases, Discovery and Lateral Movement.
The Discovery Phase (MITRE TA0007)
MITRE describes Discovery as the orientation phase of the attack, during which attackers observe the environment and plan their next moves while avoiding detection.
They look for critical assets, such as:
- Domain controllers
- Backup servers
- Sensitive databases and business-critical operations
The challenge for defenders is that this activity often blends into everyday operations, making it difficult for traditional security controls to detect. For example, attackers may ‘live off the land’, using legitimate tools.
The Lateral Movement Phase (MITRE TA0008)
Lateral Movement occurs when the adversary executes on what they learned during Discovery. Attackers move through the organization’s network – often through multiple systems and accounts – to find their (potentially business-critical) target.
Techniques identified by MITRE include:
- Exploiting remote services
- Reuse of credentials
- Abuse of admin channels
At this stage, adversaries might install their own remote access tools, but often continue using the legitimate tools the host provides.
Deception’s Advantage in Ransomware Detection
Movement creates noise. Every interaction produces a signal. It may be hard to detect as it blends in with legitimate activity, and in a standard environment, signals can be lost in a sea of false positives, but that signal is there if you can find it.
That’s where deception comes in.
Deception changes the dynamic by luring attackers to places where they reveal their intent. There, you can disrupt them, neutralizing the attack before they achieve their goal. Deception is often the only tool able to detect ransomware at these stages.
How Deception Technology Detects the Early Stages of Ransomware
CounterCraft’s approach to combating ransomware is specific, actionable threat intelligence powered by deception. The goal is early detection of intent, not post-incident analysis.
Digital Twin for Ransomware Detection
Deception technology uses decoys and digital twins that mirror an organization’s actual production environment. To an attacker, they look like legitimate targets, with realistic services, naming conventions, and credentials.
However, in reality, these environments sit outside production, so when the adversary enters and interacts, they:
- Immediately reveal their identity as attackers, as there’s no legitimate reason for them to be there
- Cannot cause any lasting damage to the organization’s genuine systems
- Can be observed in real-time by security teams
Turning Lateral Movement Into Intelligence
As the attacker attempts to progress through the decoy environment, CounterCraft’s deception technology places breadcrumbs directly in their path. These include fake credentials and RDP sessions.
These breadcrumbs trick attackers into revealing their intents and methods, including:
- The credentials they’re using
- Which systems they will target next
- How far the progression has advanced
Unlike production assets, no legitimate user has any reason to interact with a decoy. An alert from a decoy is high-fidelity. It can never be a false positive. So, with deception, security teams can cut through the noise and act with confidence.
The “Kill Switch” Effect
The 2017 WannaCry ransomware attack demonstrated how fast lateral movement can be if left unchecked – and the devastation it can cause. It impacted more than 200,000 computers across 150 countries, including 70,000 devices inside England’s National Health Service. However, it also revealed an important truth. The attack ended when a researcher registered a domain that acted as a kill switch, a defect accidentally left in by the ransomware’s creators.
Deception creates a minefield of intentional “kill switches”. As soon as the malware infection attempts to spread to a decoy, it alerts the security team, who can isolate the attack. All this happens before the attacker has the opportunity to encrypt.
To learn how deception can combat every stage of cyber attack, download our datasheet.
Case Study: Catching The Thief in the SWIFT Network
The Challenge
For a multinational bank, lateral movement toward its SWIFT payment network is a critical risk. Once inside the environment, adversaries could blend into routine admin activity, making malicious behavior almost impossible to detect.
Any detection capability would also have to operate without disrupting legitimate access or slowing down operations.
The Solution
CounterCraft deployed a deception environment that replicated the bank’s SWIFT access portal – a prime target for potential attackers. No legitimate user would have a reason to access this environment, making any interaction a clear indicator of malicious intent.
Once CounterCraft laid the trap, it didn’t take long for adversaries to walk into it.
The Results
One Friday afternoon, CounterCraft’s Threat Intel team received a high-priority alert from our multinational banking client. Because the alert originated from a decoy, malicious intent was immediately clear.
The bank confirmed that red teams and unauthorized users had accessed our decoy SWIFT portal on five separate occasions in less than an hour.
The CounterCraft decoy had tempted out attackers that had been hiding in the bank’s system for days, weeks, or even months. No other tool in the bank’s security tech stack was able to identify this activity.
The Outcome
CounterCraft deflected adversaries into a non-production environment, allowing the security team to observe behavior, capture attacker TTPs, and review internal access controls. The actual SWIFT portal remained completely safe.
Knowing more about what they were fighting against, the bank was able to harden its internal access controls before any escalation could occur.
This case is a real-world confirmation of the power of deception – and Countercraft’s capabilities in harnessing that power. To find out more, download the full case study.
Why Deception is a CISO’s Best Bet for Ransomware Defense
Other security tools can identify activity, but SOC teams struggle to distinguish adversary activity from legitimate admin use. Deception uncovers malicious intent inside your environment, making it invaluable in ransomware prevention. Beyond just detection, deception has the following benefits:
Reduction in Dwell Time
Ransomware attackers need time to explore the environment and locate high-impact targets. Detecting them during discovery or lateral movement strips that advantage. Early exposure forces attackers to disengage before encryption.
Zero False Positives
False positives – as often produced by reactive cybersecurity techniques – waste time, take teams away from essential work, and destroy morale. However, deception alerts are binary. If an interaction with a decoy occurs, it has to be malicious. SOC teams can then act with confidence.
Adversary-Generated Intelligence
What could be more reliable than intelligence that comes from the attacker themselves? In a deception environment, the attacker reveals the tools they’re using, the credentials they’ve compromised, and the paths they took to get around your system. This is invaluable to neutralize the attack and prevent future incidents.
Safe Engagement
Deception redirects attackers away from your essential systems and data into a controlled environment where they cannot cause further damage. Defenders can watch them without risk and collect valuable evidence for the future, all without disrupting critical services.
Proactive Defense
Deception is proactive, while other cybersecurity techniques are reactive. If your SOC teams are only receiving alerts when an attacker is conducting malicious activities, it’s too late. Deception meets adversaries where they are and spoils their mission, while outcomes remain controllable.
Find Out How Deception Can Work for You
Discover how CounterCraft The Platform stops ransomware attackers in their tracks with specific, actionable, real-time threat intelligence powered by deception.
In 20 minutes, we’ll show you why leading organizations – including the U.S. Government – trust our deception technology to detect, disrupt, and learn from discovery and lateral movement attempts.
Request a demo and take the first step toward proactive ransomware defense.
Takeaways
- Ransomware is a process, not an event. The initial malware infection is just the start; the damage comes after discovery and lateral movement.
- Lateral movement is the choke point. Discover the adversary here, and you stop the encryption.
- Deception delivers the visibility you need. Traditional cybersecurity tools struggle to differentiate between everyday admin activity and an attack. Deception makes this difference obvious.
- Early detection saves millions. With ransomware recovery costs averaging over $1.5 million, there’s an undeniable ROI to stopping an attack.