Given the current geopolitical tensions, companies in the financial sector and other critical industries are more worried than ever about sophisticated threats. We have seen examples of this in our deception environments, such as with the recent attack detected in early February 2022 involving threat actors attempting to attack Ukrainian government infrastructure.
Sophisticated threats don’t necessarily mean sophisticated attacks. An attack doesn’t have to be sophisticated to be successful. Most attacks use well-known approaches— because they are proven to work.
Here at CounterCraft, we define sophisticated threat actors as well-sourced attackers with a clear mission. They are humans, and therefore we see sophisticated threats as advanced human-operated attacks. Most of them share common characteristics:
- Persistence
- Determination
- Patience
- A desired objective or outcome
CounterCraft’s cyber deception solution is designed to target these sophisticated threat actors as they execute advanced human-operated attacks. Our system automatically extracts command line inputs from human operators enabling analysis and export to other incident response systems.
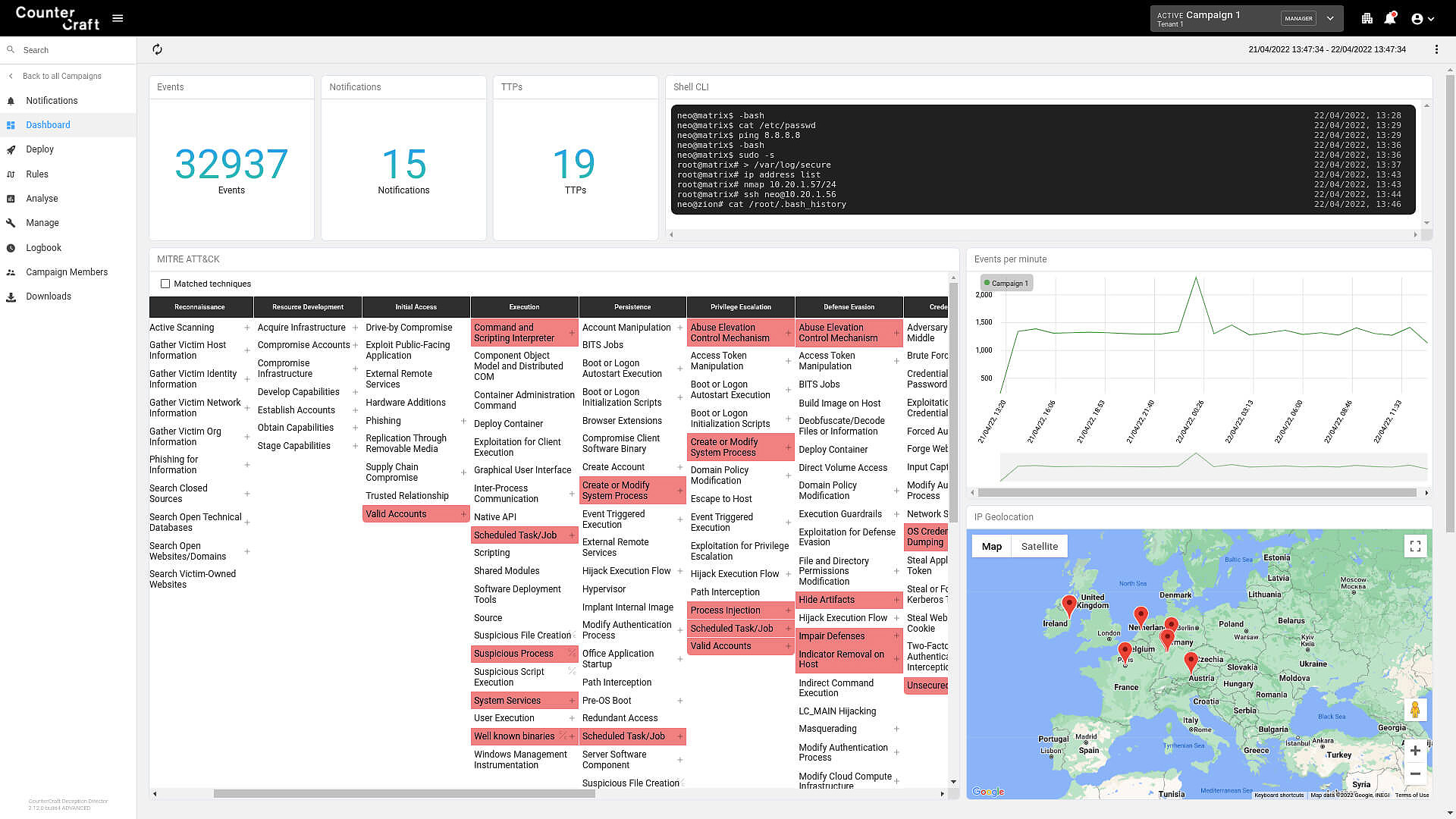
A view of The Platform, with outputs by TTP and geolocation, mapped to the MITRE ATT&CK matrix
In Forbes magazine, Leonard Kleinman says “protecting your organization from attacks like these starts with visibility. Ensuring you have extreme visibility enables effective and timely detection, containment and response. Such capabilities provide dual benefits: alerting you to events of interest that can lead to incursions as well as the ability to investigate, assess and remediate the damage”.
Even if Mr Kleinman doesn’t mention cyber deception in his article, I couldn’t think of a better way to describe what CounterCraft’s cyber deception solution does.
Visibility is defined by the Oxford dictionary as “the state of being able to see or be seen”. CounterCraft’s cyber deception gives you real-time visibility of what sophisticated threat actors are trying to do against your network.
There are three key points to achieving the kind of visibility that allows you to detect and protect from these advanced threat actors.
Timely detection
Perhaps the most important aspect of stopping sophisticated threat actors is detecting them, and doing so as soon as possible. Cyber deception is uniquely positioned to do so, for several reasons. Cyber deception doesn’t need to know “what good looks like”. Other cybersecurity tools, such as antiviruses or EDRs, need signatures, patterns, and behaviors as a baseline to determine what is “good” and what looks “bad”. Those tools are also crucial for the overall cybersecurity strategy of any company, but cyber deception covers the gaps left behind.
Most successful attacks need an initial access broker, either external or insider. Cyber deception is one of the most effective ways to detect and gain visibility of insider threats and lateral movement. At the same time, it detours the attacker away from the real infrastructure into the deception environment.
Early detection is crucial, and cyber deception can be designed to detect intent of attack even before it happens. With deception, every stage of the attack, even pre-breach, is an opportunity to trip up and trap cyber criminals targeting your organization. The more we understand the different steps a cyber criminal takes, the more opportunity we have to stop them.
Gathering threat intel
Another important piece of stopping sophisticated threat actors is gathering threat intelligence on them. If the only approach taken is blocking attacks, organizations will never be able to capture the intelligence that can help fight those threats more effectively, making it less likely they will be able to protect themselves. Furthermore, the value of threat intel diminishes as time passes, meaning receiving threat intel in real time should be the priority.
This is where cyber deception shines. Deception-powered threat intelligence comes from the actions and behavior of the threat actors themselves on your attack surface. It lures the attackers away from production to deception environments where relevant threat intelligence is captured in real time so organizations can make informed decisions on how to remediate and shore up defenses.
Adversary profiling
Finally, if your goal is to stop sophisticated threat actors, you must begin building profiles of adversaries. Cyber deception allows you to take a further step as it is one of the only defense tools that help in the process of profiling cyber criminals. A profile provides answers to four key questions;
- What has the adversary been able to do? (e.g. show the TTPs associated with an intrusion)
- What are their objectives?
- Who are they? (e.g. cross reference against 100+ cyber criminal group profiles stored on our system)
- What are they going to do next?
These questions are essential to provide you with the awareness of the situation to respond effectively. Learn more about how to profile cyber criminals here.
Stopping sophisticated cyber threats is a priority for large organizations, financial services, and critical infrastructure. There are many ways to protect against them, including timely detection, relevant threat intel, and a detailed understanding of the adversary—and cyber deception is a fantastic way to accomplish all three.

Marta Fernandez is CounterCraft’s UK Channel Manager, and you can find her on LinkedIn.