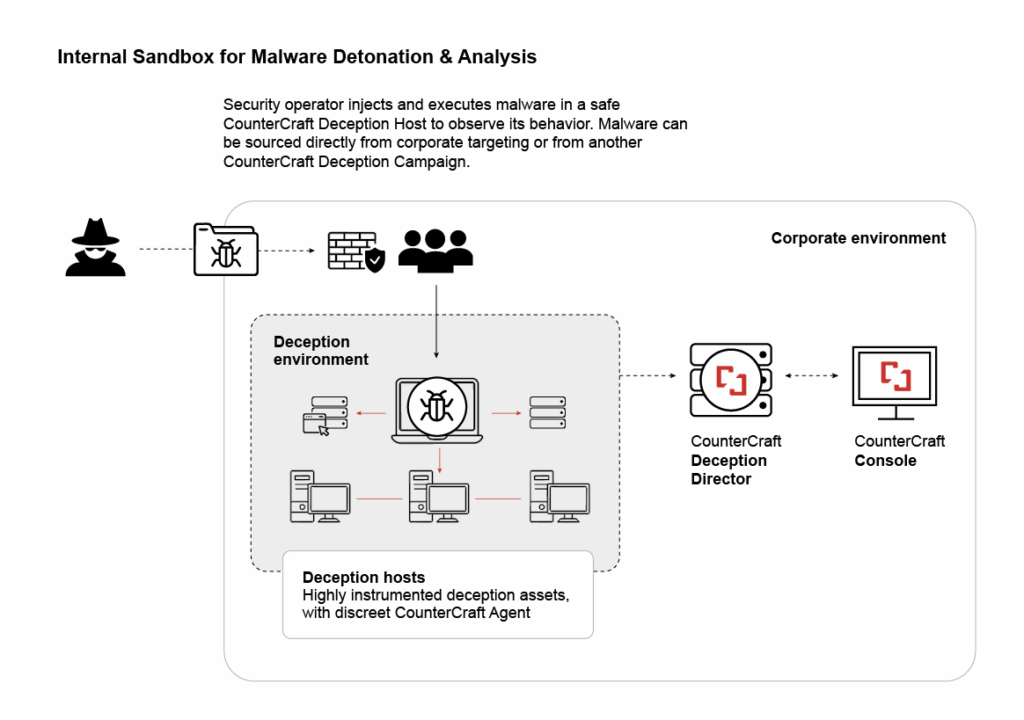
Traditional malware analysis sandboxes miss sophisticated threats that wait days or weeks before activating. CounterCraft’s realistic deception environments trick attackers into revealing their complete playbook, turning brief detections into comprehensive threat intelligence.
Your security team just caught something suspicious. Maybe it’s a strange email attachment that made it to the CEO’s computer, or a binary file that doesn’t look quite right. You know it’s probably malicious, but here’s the problem: you don’t know what it actually does.
Sure, you can block it, delete it, and move on. But what if this is just the beginning? What if there’s a sophisticated attacker behind this file, waiting to see if their first move worked before deploying their real arsenal?
This is where most organizations hit a wall. They have the suspicious file, but no safe way to see what the attacker was really planning.
The Problem with Traditional Sandboxing
Most security teams rely on automated malware analysis sandboxes that detonate suspicious files for a few minutes, extract some indicators, and call it a day. These traditional sandbox environments excel at catching commodity malware: the obvious, unsophisticated threats that immediately reveal their malicious behavior.
But modern attackers have adapted to this approach. They know their malware will likely end up in a sandbox, so they’ve developed sophisticated evasion techniques.
Here’s what’s happening: When attackers know their malware might be analyzed in a malware analysis sandbox, they build in delays and environment checks. The malicious file might sit dormant for days or weeks, doing absolutely nothing to avoid detection. Some malware even checks if it’s running in a virtual machine or looks for signs of a sandbox environment before activating.
It’s only after this waiting period, when the malware believes it’s in a real production environment, that the real attack begins.
So your sandbox sees a file that appears harmless, gives it a clean bill of health, and the sophisticated threat slips through undetected.
What Actually Happens When Attackers Strike
Let’s say an advanced attacker successfully plants their malware in your environment. Here’s their playbook:
- They start with something minimal, just enough to establish a foothold.
- The malware performs checks to determine if it’s running in a real environment or a sandbox.
- If it passes the checks, the malware sits quiet for days or weeks, looking completely innocent
- Only after they’re confident they haven’t been detected do they deploy their actual tools and start their real operation.
Traditional malware analysis sandboxes catch step one but miss steps two through four entirely. You’re left knowing you had a suspicious file, but with no insight into what the attacker was actually trying to accomplish.
This gap is particularly problematic for financial institutions, healthcare organizations, and other high-value targets that sophisticated threat actors specifically hunt. These aren’t opportunistic attacks; they’re planned campaigns where attackers invest significant time and resources to understand their target before striking.
A Different Approach: Advanced Malware Analysis Sandboxing
What if instead of just detonating the file and hoping for the best in a basic malware analysis sandbox, you could let the attacker think they’ve successfully compromised a real environment?
That’s exactly what CounterCraft’s approach does. When you find a suspicious file, instead of just running it in a standard sandbox, you deploy it in a realistic, isolated environment that looks and feels like your actual network but is completely separate from your production systems. This approach makes our customers jump out of their seats with excitement. This is the chance to see what would have played out and how your security stops would have performed if you had not detected the malware. There is no better tool to improve your system’s security.
This approach turns your malware analysis sandbox
from a brief detection moment into a comprehensive intelligence-gathering operation.
The environment includes:
- Realistic user accounts that look like your employees
- Company wallpapers and branding that match your organization
- Domain names and network topology that mirrors your real infrastructure
- The kind of data, applications, and systems an attacker would expect to find
- Simulated user activity that makes the environment feel “lived in”
To the attacker, it looks like they’ve successfully compromised a workstation in your network. But in reality, they’re completely isolated in a controlled environment where you can safely observe everything they do for extended periods, days or even weeks if necessary.
This approach turns your malware analysis sandbox from a brief detection moment into a comprehensive intelligence-gathering operation.
What Makes This Different from Standard Automated Malware Analysis?
When attackers think they’re in a real environment, they drop their guard. Instead of waiting weeks to deploy their tools, they start working immediately. Your malware analysis sandbox becomes a window into their entire operation, not just the initial file.
You get to see:
- Complete Attack Chains: What tools they’re actually using and how they deploy them
- Lateral Movement Techniques: How they move through networks and escalate privileges
- Data Targeting: What information they’re specifically looking for
- Command and Control: How they communicate with their infrastructure
- Persistence Methods: How they maintain long-term access
- Attack Methodology: Their complete playbook from initial access to final objectives
This transforms your understanding from “we detected something suspicious” to “we know exactly how this threat actor operates and what they’re trying to achieve.”
The intelligence you gather goes far beyond traditional sandbox analysis reports. Instead of just seeing process execution and network connections, you observe actual attacker decision-making and behavior patterns that help you strengthen your defenses against similar future attacks.
How Does This Compare to Traditional Sandbox Solutions?
Standard malware analysis sandboxes are excellent at what they do: automated dynamic malware analysis that quickly identifies malicious behavior. They process thousands of samples efficiently and provide valuable indicators of compromise.
But they’re designed for speed and automation, not for understanding sophisticated human adversaries. They run samples for minutes, not days. They don’t interact with attackers or try to convince them the environment is real.
CounterCraft’s approach is the gold standard for cases where you need deeper intelligence about advanced threats that traditional automated malware analysis might miss or misclassify.
We go even deeper into the technical side of what this sandboxing strategy looks like on our blog Sandboxing 2.0. Read it here.
Real-World Results
Financial institutions are already using this approach to understand sophisticated threats that would otherwise slip past traditional defenses. When they find something suspicious, instead of just blocking it, they can:
- See the full scope of what attackers were planning
- Understand their tactics and techniques
- Build better defenses based on actual attacker behavior
- Often keep attackers engaged for 24-48 hours, buying time to secure the real network
Is Your Malware Analysis Sandbox Ready for 2025 Threats?
Your existing malware analysis sandbox is likely incomplete for handling today’s sophisticated threats. It tells you that something might be malicious, but it can’t tell you what advanced attackers are really trying to achieve.
In 2025, several top-tier malware sandboxes offer powerful detection, evasion resistance, and automation capabilities, but attackers have developed sophisticated techniques to evade traditional sandbox analysis. Identity-first attacks, token replay, and cloud-native threats often bypass file-based detection entirely.
Modern attackers also leverage AI to optimize their evasion techniques, test multiple variants of their malware, and develop environment-aware payloads that behave differently in sandboxes versus real environments.
By combining traditional automated malware analysis with realistic deception environments, you transform brief detection moments into comprehensive intelligence about your adversaries. Instead of just knowing you were targeted, you understand exactly how sophisticated threats operate and can build defenses that actually work against real-world attack methods.
Your organization will face advanced threats…will your malware analysis sandbox will give you the intelligence you need to understand and counter them when they arrive? Explore real-world use cases through a personalized demo and walk-through of some of our deception campaigns to adopt a preemptive cybersecurity posture.