Zero trust has become one of the biggest buzzwords in the industry today. Many vendors claim to have a “widget” that if purchased will “automagically” implement the zero trust model into one’s organization. That is simply not true.
The current landscape of cybersecurity threats facing an organization today can be daunting. Organizations have to contend with insider threats, phishing attacks, APTs, hacktivists, script kiddies—the list goes on and on.
According to Accenture’s “State of Cybersecurity Resilience 2021” report, security attacks increased 31% from 2020 to 2021. The number of attacks per company increased from 206 to 270 year over year.
Topping the list of concerns for many organizations is ransomware. Ransomware attacks are a constant threat affecting all sectors. According to Emsisoft’s “The State of Ransomware in the US” report , an estimated 2,323 local governments, schools, and healthcare providers were victims of a ransomware attack in 2021.
Consider the fact that a cybersecurity attack costs an organization an average of $200,000, and many affected companies go out of business within six months of the attack, according to insurance company Hiscox. It’s no wonder organizations are anxious to arm themselves with the latest in cybersecurity tools to help defend against the growing sophistication of cybercriminals.
This also means the adoption of new cybersecurity frameworks, concepts, and models. The zero trust model finds itself at the top of many CISOs’ lists as a way to potentially reduce or even eliminate cybersecurity attacks.
Let’s first define zero trust. Per NIST SP800-207:
“Zero trust is a cybersecurity paradigm focused on resource protection and the premise that trust is never granted implicitly but must be continually evaluated. Zero trust architecture is an end-to-end approach to enterprise resource and data security that encompasses identity (person and nonperson entities), credentials, access management, operations, endpoints, hosting environments, and the interconnecting infrastructure.”
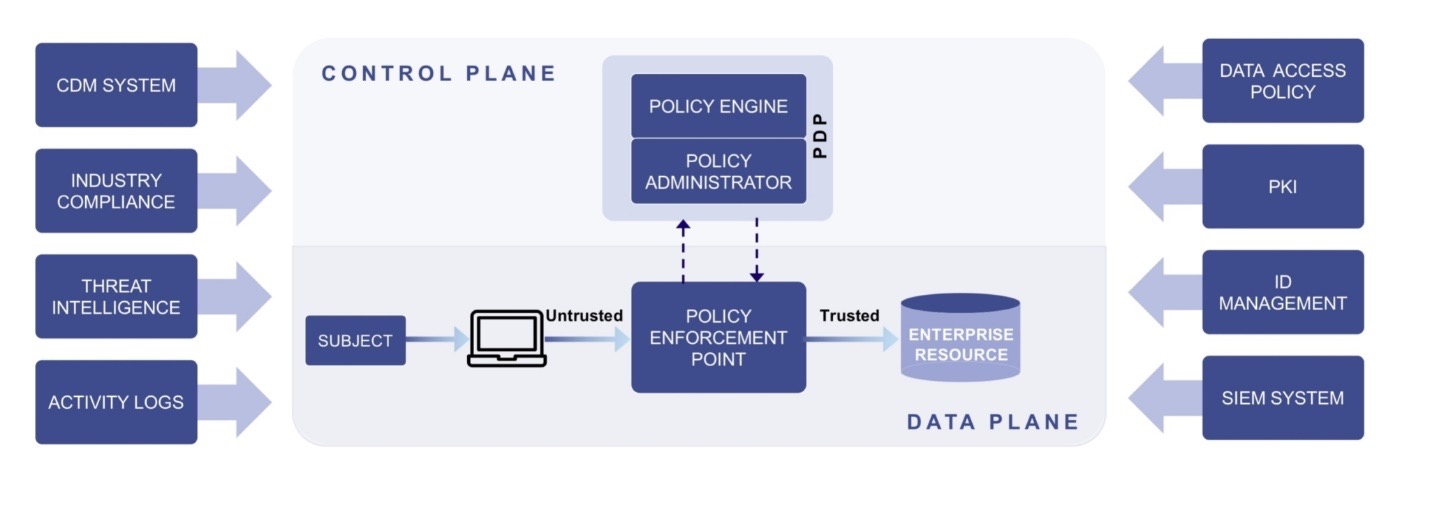
NIST Zero Trust Architecture Diagram
The zero trust ethos can be summed up by the statement “Never Trust, Always Verify”. However, from a technology perspective, zero trust will always have aspects of multi-factor authentication (MFA), Least Privilege, Segmentation, and IAM as part of its architecture.
However, with any framework, model, or concept there are exceptions and gaps. The same is true with the zero trust model. Here are some of the challenges with enacting a zero trust model:
- Per NIST, the zero trust ecosystem is not mature enough for widespread adoption.
- Despite what many vendors claim, there is no single solution that provides all the necessary components.
- Few zero trust components available today can be used for all of the various workflows present in an enterprise.
- Additionally, the zero trust security models assume that an attacker is present in the environment and that an enterprise-owned environment is no different—or no more trustworthy—than any non-enterprise-owned environment.
Working towards achieving zero trust in an organization is a move in the right direction to protect against cyberattacks. However, to truly defend against cybersecurity threats, an organization has to take an active defense approach to cybersecurity threats.
This can be achieved by incorporating deception technology into your overall cybersecurity plan. Deception technology enables an organization to take a proactive cybersecurity stance in conjunction with models like zero trust to create a comprehensive cybersecurity plan. The table below highlights how deception technology can complement a zero trust architecture.
Tenets of Zero Trust
1. All data sources and computing services are considered resources. A network may be composed of multiple classes of devices. A network may also have small footprint devices that send data to aggregators/storage, software as a service (SaaS), systems sending instructions to actuators, and other functions. Also, an enterprise may decide to classify personally owned devices as resources if they can access enterprise-owned resources.
| HOW COUNTERCRAFT HELPS |
|---|
| CounterCraft can mirror the assets within your production environment. CounterCraft doesn’t emulate environments. CounterCraft installs on real non-production virtual machines and/or servers to provide credibility. We have support for essentially all x86 Linux distributions and Microsoft Windows Operating System. You can create the following assets within our deception environment:– Servers – Desktops – HMI – Historian – PLC – Other asset types include: mobile phones, routers, deception personas, and Windows/Linux servers with no Monitoring Agent installed. |
2. All communication is secured regardless of network location. Network location alone does not imply trust. Access requests from assets located on enterprise-owned network infrastructure (e.g., inside a legacy network perimeter) must meet the same security requirements as access requests and communication from any other non enterprise-owned network. In other words, trust should not be automatically granted based on the device being on enterprise network infrastructure. All communication should be done in the most secure manner available, protect confidentiality and integrity, and provide source authentication.
| HOW COUNTERCRAFT HELPS |
|---|
| CounterCraft has a flexible deployment model. CounterCraft can be deployed on-premise within the network, outside the network {DMZ}, and in the Cloud. All communication within the deception environment utilizes SSH connections and TLS Encryption. |
3. Access to individual enterprise resources is granted on a per-session basis. Trust in the requester is evaluated before the access is granted. Access should also be granted with the least privileges needed to complete the task. This could mean only “sometime recently” for this particular transaction and may not occur directly before initiating a session or performing a transaction with a resource. However, authentication and authorization to one resource will not automatically grant access to a different resource.
| HOW COUNTERCRAFT HELPS |
|---|
| CounterCraft has Role Based Access Control (RBAC) to ensure that users only have the appropriate amount of privileges within the deception environment. There are three user accounts: Administrator, Super Architect, and Standard. User account permissions are further subdivided at the Tenant level into two sorts of Tenant members: Tenant Architect and Tenant Standard. User account permissions are further subdivided at the Campaign level into three sorts of Campaign members: Manager, Operator, and Guest. |
4. Access to resources is determined by dynamic policy—including the observable state of client identity, application/service, and the requesting asset—and may include other behavioral and environmental attributes. An organization protects resources by defining what resources it has, who its members are (or ability to authenticate users from a federated community), and what access to resources those members need. For zero trust, client identity can include the user account (or service identity) and any associated attributes assigned by the enterprise to that account or artifacts to authenticate automated tasks. Requesting asset state can include device characteristics such as software versions installed, network location, time/date of request, previously observed behavior, and installed credentials. Behavioral attributes include, but not limited to, automated subject analytics, device analytics, and measured deviations from observed usage patterns. Policy is the set of access rules based on attributes that an organization assigns to a subject, data asset, or application. Environmental attributes may include such factors as requestor network location, time, reported active attacks, etc. These rules and attributes are based on the needs of the business process and acceptable level of risk. Resource access and action permission policies can vary based on the sensitivity of the resource/data. Least privilege principles are applied to restrict both visibility and accessibility.
NIST SP 800-207 ZERO TRUST ARCHITECTURE
| HOW COUNTERCRAFT HELPS |
|---|
| The CounterCraft platform has a RESTful API to easily integrate with an organization’s IAM solutions to enforce dynamic policies. Additionally, CounterCraft has Role Based Access Control (RBAC) to ensure that users only have the appropriate amount of privileges within the deception environment and easily integrates with an Identity Provider (IdP) or MFA solution via the SAML federation protocol. |
5. The enterprise monitors and measures the integrity and security posture of all owned and associated assets. No asset is inherently trusted. The enterprise evaluates the security posture of the asset when evaluating a resource request. An enterprise implementing a ZTA should establish a continuous diagnostics and mitigation (CDM) or similar system to monitor the state of devices and applications and should apply patches/fixes as needed. Assets that are discovered to be subverted, have known vulnerabilities, and/or are not managed by the enterprise may be treated differently (including denial of all connections to enterprise resources) than devices owned by or associated with the enterprise that are deemed to be in their most secure state. This may also apply to associated devices (e.g., personally owned devices) that may be allowed to access some resources but not others. This, too, requires a robust monitoring and reporting system in place to provide actionable data about the current state of enterprise resources.
| HOW COUNTERCRAFT HELPS |
|---|
| Assets that are discovered to be subverted, have known vulnerabilities, and/or are not managed can easily be recreated within the CounterCraft deception environment where you can safely and securely gather real-time, actionable tailored threat intelligence on how a bad actor may attack such an environment. Information you can use to shore up your production defenses. |
6. All resource authentication and authorization are dynamic and strictly enforced before access is allowed. This is a constant cycle of obtaining access, scanning and assessing threats, adapting, and continually reevaluating trust in ongoing communication. An enterprise implementing a ZTA would be expected to have Identity, Credential, and Access Management (ICAM) and asset management systems in place. This includes the use of multifactor authentication (MFA) for access to some or all enterprise resources. Continual monitoring with possible reauthentication and reauthorization occurs throughout user transactions, as defined and enforced by policy (e.g., time-based, new resource requested, resource modification, anomalous subject activity detected) that strives to achieve a balance of security, availability, usability, and cost-efficiency.
| HOW COUNTERCRAFT HELPS |
|---|
| CounterCraft easily integrates with an IdP or MFA solution via the SAML federation protocol. Additionally, the user’s password is hashed using the PBKDF2 algorithm with a SHA256 hash, a password stretching mechanism recommended by NIST. Users can also protect their accounts by enabling two-factor authentication (2FA) that uses Google Authenticator. Both user’s valid and invalid login attempts are stored with their related information: date, IP address, and user agent. Users are disabled after a configurable number of invalid login attempts and they can only be enabled by the admin user. |
7. The enterprise collects as much information as possible about the current state of assets, network infrastructure and communications and uses it to improve its security posture. An enterprise should collect data about asset security posture, network traffic and access requests, process that data, and use any insight gained to improve policy creation and enforcement. This data can also be used to provide context for access requests from subjects.
| HOW COUNTERCRAFT HELPS |
|---|
| Within the CounterCraft deception environment, all security alerts are generated in real time and can be sent via various communication channels i.e., email, signal, mobile devices, etc. Additionally, there is out-of-the-box integration with SIEMS and SOAR platforms that alerts can also be sent in real-time. All activity within the deception environment is detected, logged, and automatically mapped to the MITRE ATT&CK and ENGAGE framework. It can also be viewed from a native fully customizable dashboard within the platform. |
As you can see, deception technology is an excellent way to complement the tools an organization is using to enact a zero trust strategy. Cyber deception has many other applications that strengthen security posture and cover ground no other software or technology can. Here are some additional benefits to deception technology:
- Misdirect bad actors away from your valued production assets
- Detect bad actors before they breach your production network
- Discover a dormant adversary and/or insider threat within your production network faster
- Obtain real-time, applicable CTI (Telemetry, TTPs, and IOCs) on the bad actor to make informed decisions on how to shore up production defenses and remediate the threat
- Gain insight into the tools attackers use to breach a network
- Safely capture and analyze the adversaries’ malicious software within a contained environment
- Learn how the adversary avoids detection of other commonly used cybersecurity tools
- Understand what the adversary wants, what they’ve done so far, and who they are (attribution)
- And more…
Final Thoughts
The zero trust model, if implemented correctly, can be effective when it comes to protecting against cybersecurity threats. However, it’s not the magic bullet many organizations are hoping for.
A mature cybersecurity approach involves incorporating models like zero trust, best-of-breed cybersecurity tools, training, integration, established SOPs + SLAs, and collaboration. It also involves taking a proactive cybersecurity stance instead of the standard reactive one.
To understand how CounterCraft can enhance your zero trust initiative and help your organization take a proactive cybersecurity stance please contact us for a technical briefing.

Shunta Sharod Sanders, the Head of Solutions Architecture – North America at CounterCraft, specializes in offensive and defensive cybersecurity technologies and is a recognized Data Storage Technology Subject Matter Expert by SNIA and CompTIA. Shunta currently leads all technical Presales activities in North America at CounterCraft. Where he works to help organizations eliminate data breaches from insider threats and external hacking attacks by taking a proactive cybersecurity stance utilizing Deception Technology. You can find Shunta here on LinkedIn.
