Stop spear phishing and gather valuable intel.
Download our ebook today to find out how to effectively stop spear phishing and gather threat intel specific to your organization.

Get it now.
Fill out this form to receive the ebook Don’t Toss the Phish. The information inside will help you and your organization detect, deter, document, and defend against cyberattacks.
Over 90% of cyber attacks begin with spear phishing, highly targeted, often sophisticated campaigns.
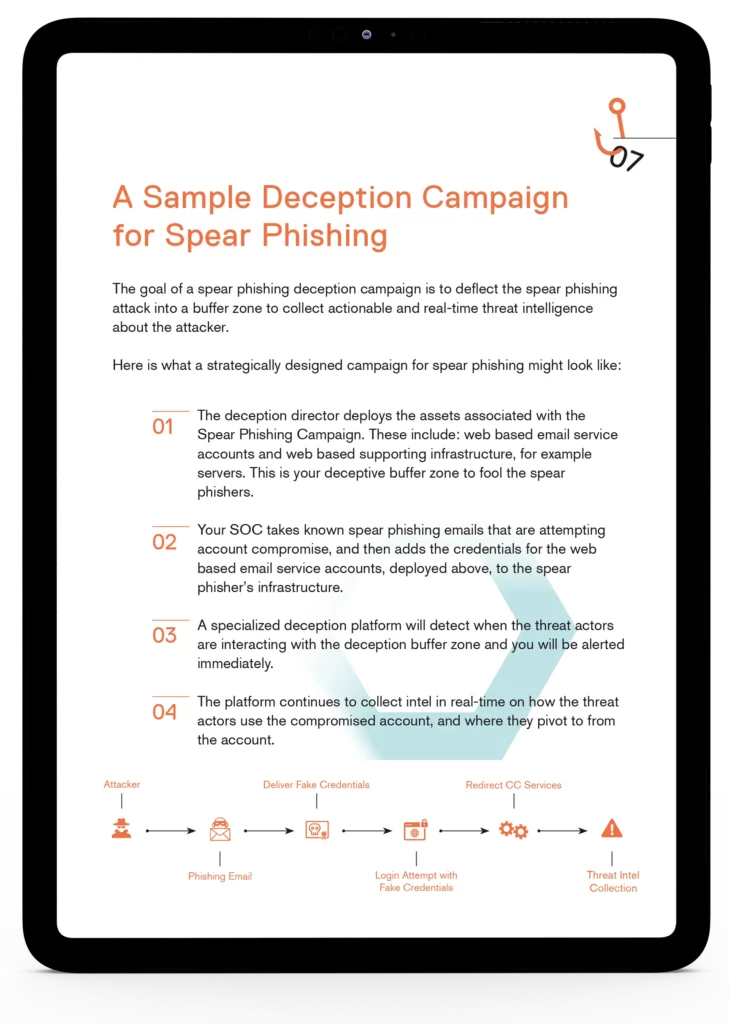
What’s inside your ebook?
Want to gain threat intel to prevent further spear phishing attacks?
Over 90% of cyber attacks begin with spear phishing. These hackers seek access to your network and have targeted your organization with laser focus —but they can also serve as a fantastic source of information.
What if you looked at spear phishing attacks as an opportunity to learn how to strengthen your security posture?
Turn the tables on spear phishing. Using deception techniques, gain unique intel on how to protect your network. The information provided by a deception campaign for spear phishing is delivered in real time, composed of contextual and relevant IoCs, and cannot be sourced from anywhere else. Find out more in our ebook.
Download now.
Detect, deter and defend against cyberattacks.