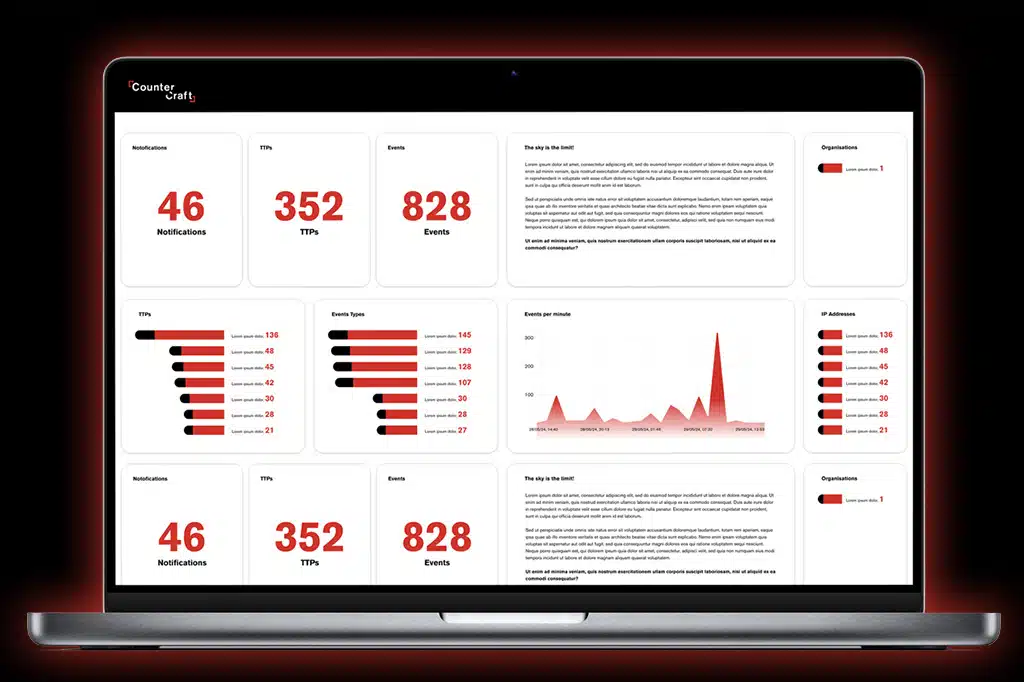
The Platform

Specific. Actionable. Threat intelligence powered by deception
The Platform gives security teams the ability to discover threats before they penetrate your network. This speed in detection is achieved thanks to unparalleled threat intelligence powered by deception which lures adversaries away from your critical systems, gathers real-time data, and allows you to understand their next steps.
No other platform takes your adversaries off your network, ensuring your live network and critical assets remain immune to attack.

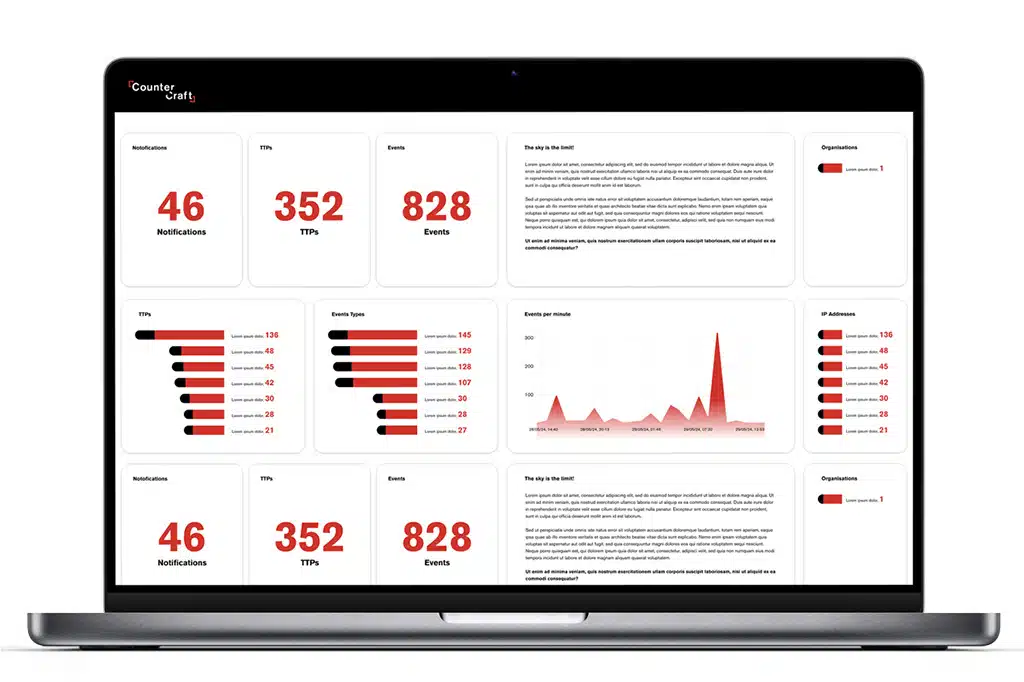
Discover how The Platform delivers rapid threat detection and specific actionable threat intelligence in real-time.
CounterCraft helps us prioritize real vulnerabilities, obtaining TTPs and IoCs we wouldn’t be able to get any other way.
Mario Castro,
Head of Telecommunications of Red Eléctrica
Frequently Asked Questions (FAQ)
CounterCraft’s The Platform is a cybersecurity solution built on deception technology. It deploys realistic decoy systems that look like real production assets, drawing attackers away from critical infrastructure. As attackers interact with these systems, The Platform captures real-time threat intelligence that helps security teams detect and respond to threats earlier than traditional detection tools. Find out more with a demo.
The Platform creates digital twin environments that mirror an organization’s real infrastructure. When adversaries interact with these decoys, The Platform records their actions and analyzes their tactics, techniques, and procedures. This allows defenders to understand attacker intent and behavior before real systems are impacted.
The Platform detects threats across multiple stages of the attack lifecycle, including reconnaissance, credential abuse, lateral movement, insider misuse, ransomware activity, and post-compromise behavior. Because detection is based on confirmed attacker interaction, the intelligence is both early and reliable.
A preemptive cybersecurity stance, which Gartner refers to as the future of cybersecurity. The Platform provides real-time threat intelligence based on confirmed malicious behavior. It enables earlier detection before attackers reach critical systems, diverts attackers away from real assets, supports both IT and OT environments, and can be deployed quickly, often within 30 days. This helps teams reduce false positives and make faster response decisions.
Yes. The Platform can be configured for on-premises, cloud, and hybrid environments. Deception assets are tailored to reflect each organization’s architecture, allowing detection across complex and distributed attack surfaces.
The Platform captures intelligence on ransomware operators and advanced adversaries when they interact with decoy systems during reconnaissance and lateral movement phases. This provides security teams with visibility into attacker tools, movement patterns, and intent before payload execution or encryption begins, enabling faster containment and mitigation.
Yes. Threat intelligence and alerts generated by The Platform can be integrated into existing security workflows, allowing teams to correlate deception signals with other telemetry and prioritize response without replacing their current tools.
The Platform is designed for enterprise organizations, including government, financial services, healthcare, telecoms, manufacturing, and critical infrastructure. It supports environments where traditional detection tools struggle to distinguish real threats from normal activity. Find out more with a demo.