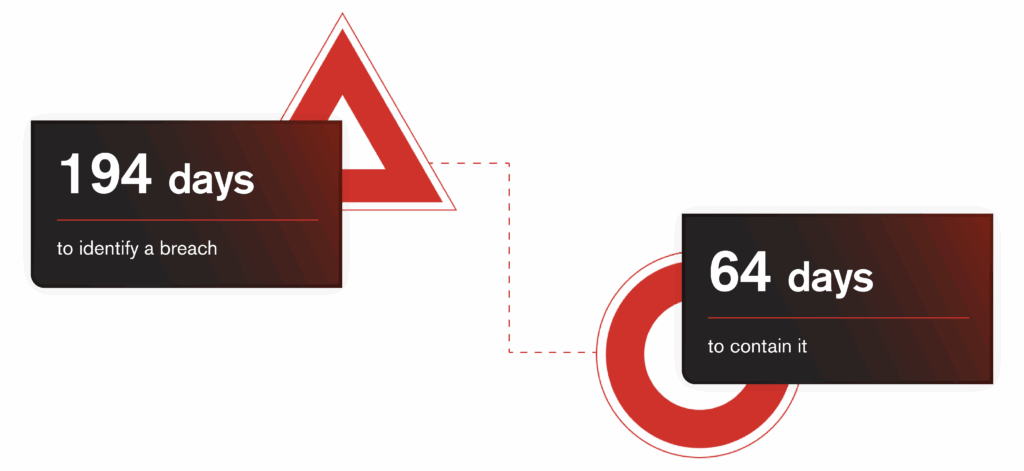
Proactive threat hunting uses deception and AI to lure attackers into fake environments, reducing breach detection from months to hours. Security teams still spend months finding breaches that, according to IBM’s 2024 cost of a breach report, cost an average of $9.48 million each. Proactive threat hunting, combining deception technology and security-focused AI can place you ahead of your attackers, providing you the control needed to reduce your discovery window from 194 days to mere hours, cut incident costs and relieve over-worked Security Operations Centers.
Ask any blue-team leader what keeps them awake at night, and they will inevitably list ransomware, credential-stuffing, and data exfiltration. Yet most organizations still rely on SIEM tools that pattern-match historical data; they are essentially rear-view mirrors. Modern AI cybersecurity
can sift millions of signals in seconds, but it’s the analyst’s intuition that turns those patterns into an actionable hunt hypothesis. When the two work in harmony, organizations swap rear-view monitoring for genuine tactical foresight.
Traditional hunts require weeks of senior-analyst time to craft hypotheses and sift logs. Proactive threat hunting with deception technology flips that dynamic by presenting attackers with convincing traps and instantly flagging the moment they engage.
What is proactive threat hunting and how does it work?
Proactive threat hunting is the process of actively searching for signs of cyber threats in your environment before alerts are triggered or damage occurs. Unlike traditional detection methods that rely on known patterns or past incidents, proactive hunting uses tools like AI, behavioral analysis, and deception technology to surface unknown or emerging threats. It shifts the focus from reacting to breaches to uncovering attacker activity early, cutting dwell time and reducing impact.
Picture your network as a bustling city at night. If the streetlamps (your alerts) only light up after a burglar has already copied every key in the utility shed, the damage is done. That silent interval is dwell time. IBM’s 2024 report lists a global average of 194 days to identify a breach and 64 days to contain it. Multiply those months across customer data, production databases, or Operational Technology (OT) environments and the price of passivity skyrockets.
The consequences of delay are real:
- Long dwell time equals bigger pay-outs: The longer attackers remain undetected, the more time they have to escalate privileges, exfiltrate data, or disrupt critical operations. In high-stakes OT environments, a delay of even a few hours can be the difference between catching reconnaissance and suffering a full-blown incident.
- Regulatory and insurance fallout: GDPR and cyber-insurers now expect ‘reasonable proactive controls’; failure can trigger fines, premium hikes, or denied claims.
- Opportunity cost and burnout: Analysts chained to consoles cannot work on strategic improvements, driving turnover and recruitment spend.
Remaining reactive is fiscally and operationally unsustainable. Every extra hour of dwell time fattens an attacker’s reward, heightens regulatory risk, and keeps scarce talent stuck in triage queues.
What are the risks of skipping proactive threat hunting?
Proactive threat hunting is sometimes dismissed as a ‘nice-to-have’ by leaders who are simply conditioned to pay invoices after an incident. When the quiet costs of passivity, which include ransoms, legal fees, and customer attrition, are tallied, the hunt program looks like a bargain.
- Brand Trust Erodes Faster Than PR Can Repair
A breach is no longer a one-day headline; it drags on share price and loyalty for quarters. Red Eléctrica with the help of deception powered threat intelligence restored confidence by detecting OT reconnaisance before attackers touched live systems. - Security-Team Churn and Burnout
Deception-led hunting delivers verified signals tied to live adversary behavior, reducing noise and cognitive load. Internal research shows analyst hours drop by up to 60 percent when hunts start with concrete telemetry rather than hunches. - Costs Across All Vectors
- Financial: multimillion-pound breach fines and ransom payments.
- Market: lost contracts and damaged reputation.
- Human: talent attrition and slower incident response.
Reallocate a slice of today’s budget to deception-powered threat hunting and you will sidestep tomorrow’s nine-figure liabilities.
What does a proactive threat hunting playbook look like?
Ready to act? A truly effective threat-hunting program isn’t a one-off exercise; it’s a repeatable, scalable process rooted in deception and speed. Here’s a five-step, deception-driven playbook to quickly deploy, safe to test, and repeat at scale.
- Define the hypothesis, not just the SIEM rule: Craft a clear hypothesis. Use intelligence triggers such as PowerShell abuse and Mimikatz dumps, supported with deception beacons.
- Instrument a safe ‘kill-box’: Now set the trap by deploying decoy hosts that mirror critical assets without touching production.
- Automate context collection: Layer in realistic context. AI populates realistic documents, inbox chatter, and user activity to keep adversaries engaged.
- Map to MITRE ATT&CK in real time: No waiting, no guesswork. Map every move to tactics and techniques to MITRE ATT&CK framework the moment it happens.
- Review, respond, repeat: Feed findings into incident-response plans, patch cycles, and new campaigns to ensure continuous improvement, not a one-off exercise.
How does deception technology improve threat hunting?
CounterCraft turns proactive threat hunting into a goal-oriented, low-noise operation. Rather than scattering generic honeypots, its platform launches targeted campaigns which includes , protecting merger documents, luring credential thieves, or shielding OT. The result is lean but laser-focused telemetry: only high-confidence alerts tied to real risk, not terabytes of SIEM noise.
How does CounterCraft support threat hunting?
Proactive threat hunting pays for itself. A modest, deception-enabled program costs far less than a single breach and can cut dwell time from months to hours.
Success comes from quality over quantity. CounterCraft’s AI-driven deception campaigns generate high-confidence, context-rich telemetry that frees analysts from alert fatigue and low-value triage.
Deception technology flips the power dynamic. By planting realistic breadcrumbs, it gives defenders early visibility, real-time MITRE ATT&CK mapping, and actionable intelligence—long before attackers reach production systems.
Ready to experience this in your own environment?
Schedule a personalized demo with our team and see CounterCraft supercharge your hunt strategy in real time.