According to Gartner, Automated Moving Target Defense (AMTD) solutions will replace at least 15% of traditional detection and response solutions by 2025. That’s a big increase considering these solutions currently make up only 2% of detection and response market share. What exactly is AMTD? And, more importantly, why are organizations starting to implement it?
Take our quiz today to find out how deception technology can work for your organization >
What is Automated Moving Target Defense (AMTD)?
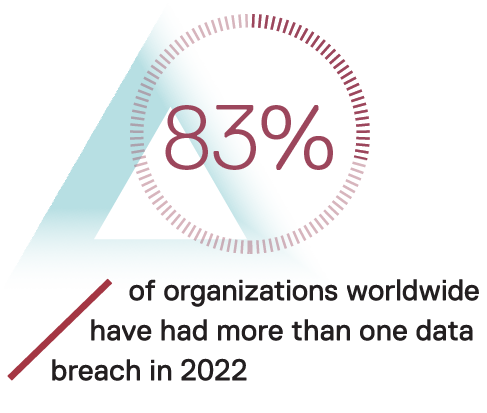
AMTD is the evolution of Moving Target Defense (MTD). MTD assumes that 100% security is unachievable1. Assuming that all systems will be compromised at some point, MTD seeks to make systems more difficult to target and to make it more difficult for an attacker to move laterally once inside by constantly changing the attack surface (IP addresses, operating systems, software versions, and configurations). The MTD assumption that perfect security is impossible to obtain is backed up by data— 83% of organizations worldwide have had more than one data breach in 20222. Nothing is secure, and this is one of the reasons why Gartner calls MTD the future of cybersecurity.
Static is Vulnerable: Embracing Change for the Future of Cybersecurity
One of the biggest challenges of current information technology environments is that they are built to operate in relatively static configurations. This means that adversaries can easily study any organization’s static systems and networks and execute their attacks thoroughly when they find vulnerabilities that they can exploit, putting organizations at an incredible disadvantage. Although organizations are using the latest and most innovative detection and response solutions, such as XDR or EDR, threat actors are still able to bypass these defenses.

That’s not to say they don’t do anything. According to Karsten Nohl, chief scientist at Berlin-based SRLabs, “Overall, EDRs are adding about 12 percent, or one week, of hacking effort when compromising a large corporation—judged from the typical execution time of a red team exercise”3. Even so, the security gap left by detection and response solutions is up to 30%. This is not a small number. Extended Detection and Response (XDR) solutions provide a holistic approach to cybersecurity, thanks to their integration of various cybersecurity solutions from different sources. But without behavior patterns from previous attacks, there’s no way to be able to automatically detect and respond to future malicious behavior. This is why XDR covers most of common threats and vulnerability issues, but is not yet capable of detecting unknown threats and APTs.
So how do organizations close the gap? The ultimate goal of AMTD is to use automation to dynamically change the attack surface of a system, making it more difficult for attackers to succeed and easier for security teams to identify threats or attacks. An attacker must remain present on the system they want to exploit, to further execute commands that allow for lateral movement or data exfiltration. But if the attacker is working in a constantly changing attack surface, their exploit capabilities vanish and their movements are stalled.
AMTD shows great potential to remediate the most relevant challenges detection and response solutions currently face. Thus, Gartner is encouraging the market to focus on this promising new prevention-related technology.
Battle-Tested Technology for Effective Defense
AMTD has been proven successful for many years in the military sector as part of warfare strategies and within core technologies we use on a daily basis. MTD is particularly effective in cases where the adversaries expend significant reconnaissance efforts to identify vulnerabilities or an attack path. The use of MTD within commercial cybersecurity is increasing especially in OT-related use cases, where the varied and specialized nature of industrial environments necessitates dedicated time and resources to gather the necessary information to be successful when attacking.
In its Emerging Tech: Security — The Future of Cyber Is Automated Moving Target Defense paper, Gartner incorporates four key elements that make up ATMD:
- Proactive cyber defense mechanisms
- Automation to orchestrate movement or change in the attack surface
- The use of deception technologies
- The ability to execute intelligent (pre-planned) change decisions
The use of deception techniques to mislead attackers plays a key role in creating a dynamic, ever-changing attack surface that makes it difficult for attackers to exploit vulnerabilities in a system. To Learn more about deception, download our Are you Ready for Deception? ebook and get in touch if you’d like to schedule a demo to see our cyber deception solution in action.
We are following these Gartner Analysts who are leading the research:
- Lawrence Pingree – https://www.gartner.com/analyst/38832 – Twitter
- Mark Pohto – https://www.gartner.com/analyst/111476 – Twitter
- Ruggero Contu – https://www.gartner.com/analyst/17278 – Twitter
- The latest paper is here https://www.gartner.com/document/4319299 And there is more to come!

Dan Brett is the Chief Product Officer and co-founder of CounterCraft. Highly accomplished in achieving outstanding growth for B2B startups, he contributes a great depth of cybersecurity knowledge and understanding of consumer behavior. Follow him on LinkedIn.
1https://www.dhs.gov/science-and-technology/csd-mtd
