Recently, Fortinet released security updates to address critical remote code execution vulnerabilities in FortiOS (CVE-2024-21762, CVE-2024-23113). This vulnerability was serious enough that CISA decided to weigh in, publishing an advisory to security professionals everywhere. According to Fortinet, CVE-2024-21762 is potentially being exploited in the wild. This is a very serious vulnerability, since a threat actor could exploit these vulnerabilities to take control of an affected system.
Our threat intel team is currently investigating this vulnerability and its implications. However, it reminds us of an incident our deception technology detected and observed some months ago.
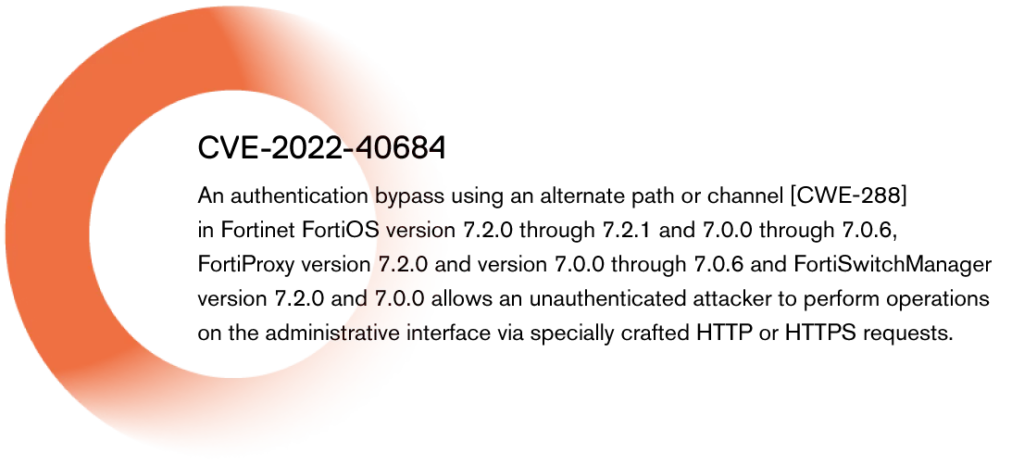
There was a significant security loophole within FortiOS SSL VPN, denoted as CVE-2022-40684, carrying a substantial CVSS score of 9.8. This vulnerability, acknowledged as “potentially being exploited in the wild,” heightens the risk for organizations relying on Fortinet appliances, yet the specifics of its exploitation remain undisclosed. CVE-2022-40684 thrust organizations into a high-stakes scenario, given its “critical” CVSS score.
Enter CounterCraft’s innovative approach: faced with the dearth of available information on this CVE, our seasoned research team swiftly orchestrated a highly convincing deception environment. This simulated the vulnerability in a fictitious FS organization, a strategic move that would later yield invaluable findings.
Almost immediately after becoming visible to potential attackers, our deception environment witnessed an exploit targeting the vulnerability. This marked the inception of an insightful analysis, facilitated by CounterCraft’s advanced deception platform, enabling us to deconstruct the exploit and discern critical details.
Check out the Attack Timeline below to see how the exploit unfolded and the intel we were able to gather in our deception environment.
To enhance transparency and understanding within the cybersecurity community, CounterCraft offers a comprehensive exploration of the forensic playout of the exploit. The captured data, now available in a JSON file from The Pulse, CounterCraft’s contextualized threat intelligence feed, unveils not only the intricacies of the exploit but also crucial information, including the Russian IP address to which it communicated.
We invite you to delve deeper into our findings by exploring the forensic playout in the provided JSON file. Gain insights into the exploit’s modus operandi, the processes it invoked, and other relevant details that shed light on the potential ramifications for organizations utilizing Fortinet appliances.
Our deception technology was able to so convincingly replicate the network environment of an organization operating with this vulnerability that it lured attackers away from critical assets and enabled us to observe their every move and adjust security posture accordingly.
Feel free to reach out for further discussions about how this can work for your organization or to request access to the detailed forensic playout of the exploit. The cybersecurity landscape is dynamic, and together, we can navigate its complexities with informed resilience.
About the Authour
Richard Barrell is the Head of Product Management, responsible for the company’s product development and growth. Follow him on LinkedIn.
