Gartner has recently published the Market Guide for Security Threat Intelligence Product and Services by analysts Craig Lawson, Brad LaPorte, Ruggero Contu, John Collins and Mitchell Schneider, which provides end users with guidance on how to ensure that they are getting the best value from threat intelligence services. This excellent piece of research is extremely valuable for those that do not have a threat intelligence service and are currently looking at what potential options they may have. Over the course of this blog post you’ll have a synopsis of its key points from our own perspective and what we believe are the key takeaways for end users.

Deception and Threat Intelligence
An important component of the report is the introduction of the concept of using intelligence that you can produce yourself. How would you do that? You can do this through the use of deception technology. By using deception technology end users can generate highly actionable threat intelligence that is delivered in real time. A rich seam of TTPs and IOCs, which are immediately actionable, can be used, so that end users can better understand what threat actors and threat vectors are targeting them. Users can accurately curate intelligence that addresses both business risks and technical risks to their organisations. A simple example would be spear phish attacks. You may be receiving generic enterprise intelligence that you are being targeted. But are you receiving real-time intelligence that informs you who might be behind those attacks, what their strategic objectives may be and who are they looking to attack? Is it your VIP suite or operators in the security operations centre? Having threat intelligence that can answer these questions allows an organisation to take its limited security budget and align its security controls to the actual threats that are targeting it. The use of deception technology to generate actionable intelligence also delivers one further critical ability to an organisation: the ability to adapt your security posture to the actual threats targeting you at any given moment in time. We all know that the threat landscape is constantly evolving and what you need to ensure is that your current control set is aligned to the current threat landscape.

Pain Points
The Gartner’s Market Guide highlights that end users are constrained by their ability to “afford, absorb and contextualise the intelligence that is provided”. CounterCraft is able to deliver its intelligence in a number of different formats. For example, it can deliver MRTI, TTPs and IOCs in real time. Below is a pictorial representation of some of our key integrations:
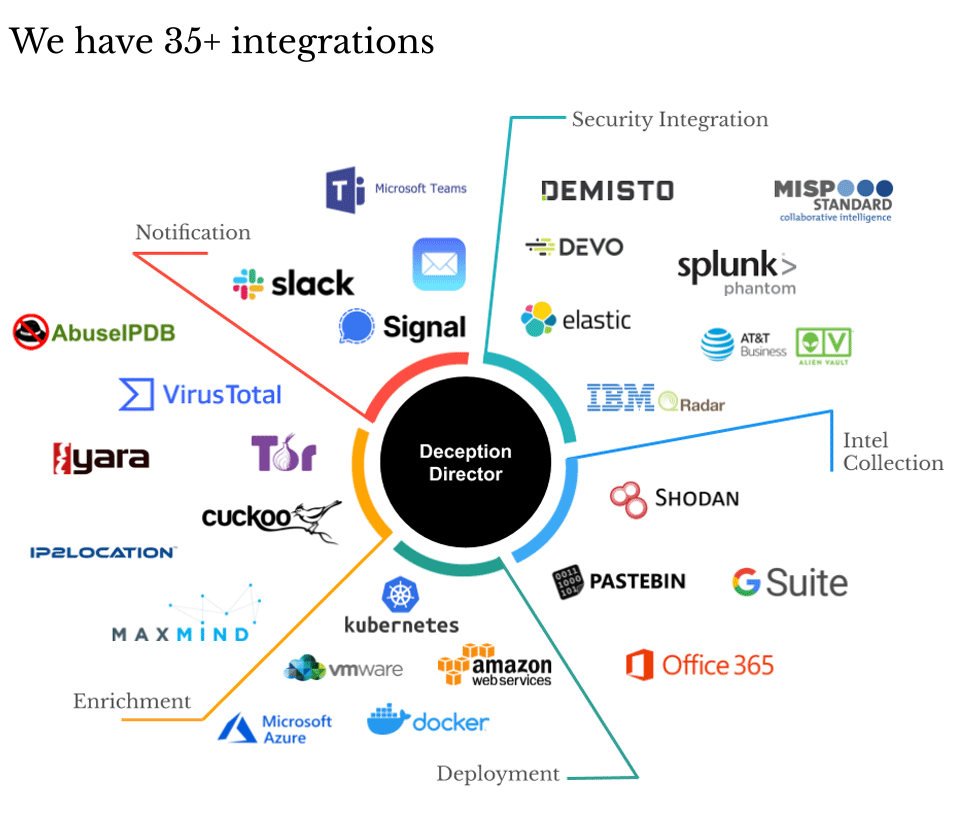
The ability to absorb intelligence therefore is no longer an issue. But the key here is the end users’ need for threat intelligence to be specific to them and actionable. How does CounterCraft address these pain points? By delivering deception scenarios we are able to deliver precisely the enterprise intelligence that end users need. But we do not stop there: CounterCraft has the ability to take any IOC that it sees and match it in real time (if it is an IOC that is used by one of the many threat actor groups that we are tracking) to a known threat actor group. So, now the end user not only has context and actionability, but they also gain situational awareness. This is achieved without the need to deploy an army of analysts because the automated deception platform takes this task away from the analyst so that they can focus their attention on how to mitigate the TTPs and IOCs that have been identified.

Big Data v. Right Data
The Market Guide highlights that one of the key constraints for end users when using threat intelligence services is their inability to act on the sheer volume of the intelligence that comes their way. We call this problem “the big data v. the right data challenge”. Through the use of deception technology, end users can craft deception campaigns that answer intelligence questions and this approach avoids the pitfalls of big data. By deploying deception scenarios that address a specific intelligence question you only receive TTPs and IOCs that are directly related to that question. What are the specific attack vectors and TTPs that are being leveraged against my VPN infrastructure? What intelligence can I gather that informs me about my insider threat, and more specifically, how is that risk spread out across my organisation? Does that insider threat manifest itself in more than one part of the business than another? This brings us to the final point we would like to address in this post. The focus on collecting intelligence is concentrated more often than not on externals attackers looking to hack into online services or the corporate network. Very few services have the ability to deliver real-time intelligence about threats from within your organisation and external threats. It does not stop there. Do you want to generate your own intelligence to understand potential attacks against your business applications, web portals, from APT groups or against VIPs? The architecture that the CounterCraft Cyber Deception Platform is built upon allows it to be deployed effectively to answer a diverse range of threat intelligence questions without creating intelligence that is too generic for customers. High fidelity intelligence that is specific to your organisation can be curated by the end user by leveraging the unique feature set that is built into the CounterCraft automated deception platform.

One Last Thing
So, are you receiving value from your threat intelligence service? If you are suffering from any of the pain points that we have covered in this post then perhaps it’s time for a change. Ask yourself: does the threat intelligence that I am receiving deliver the right information to the right people at the right time? Does my threat intelligence arrive in real time, so that it can be leveraged by people, technology, and processes simultaneously? And finally: is that threat intelligence that I am receiving empowering my business stakeholders, allowing them to deliver a digital transformation programme that has security built into its foundations?

Author: Nahim Fazal, Head of Cyber Threat Intelligence