Curious about which blogs were the most popular this year here at CounterCraft?
From highly technical posts with practical applications to in-depth looks at deception technology, our blog featured all manner of articles written by experts in the field. Read on to get the best of what everyone was reading on our website in 2021.

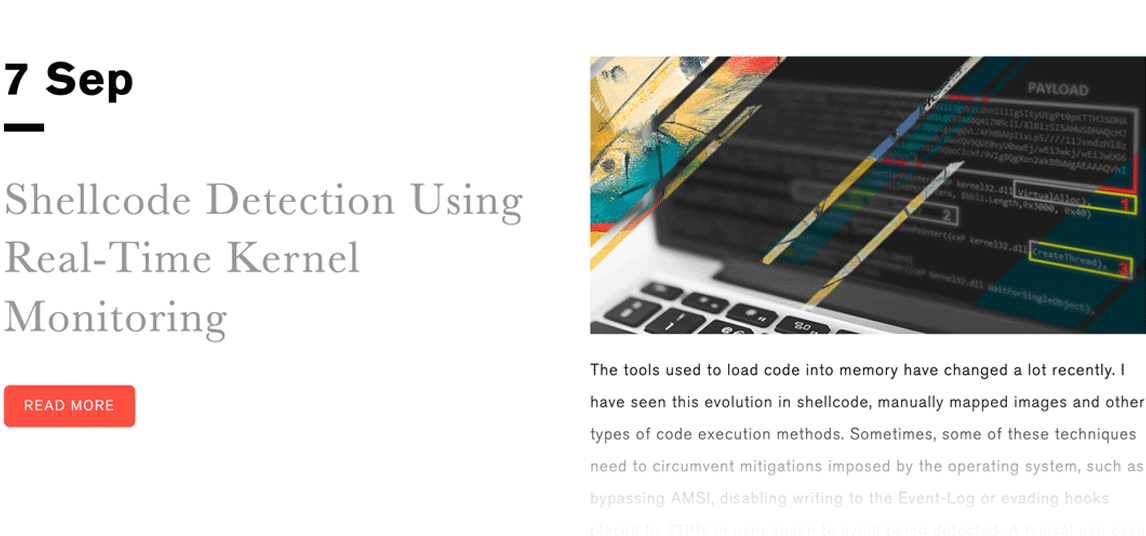
Shellcode Detection Using Real-Time Kernel Monitoring
This article, written by Alonso Candado, a security software engineer here at CounterCraft, is a quick overview of how to detect shellcodes from the kernel in real time using specific examples. The post proved very useful for researchers, who develop offensive security tools, making it worthwhile to consider these methods in addition to EDR userland hooks.
Read the full blog here.


Improving OT Security
Cyber attacks on critical infrastructure and physical systems are on the rise. However, there are unique challenges to protecting operational technology. This post on improving OT security was extremely popular. It includes a data sheet, which you can download here. Read more about the specific challenges and our solution, named a 2021 Gartner Cool Vendor in Cyber Physical systems.
Read the full blog here.


CVE-2021-26084, Payloads and OOB Interaction
In this article, written by our CEO David Barroso, we get a glimpse into how attackers are exploiting CVE-2021-26084. As soon as we realized that many different attackers were going to actively use this vulnerability, we immediately deployed several Confluence servers in different locations to collect as much activity as we could from such attacks. The moment we installed the Confluence servers, we started to receive hits from different ip addresses. This blog explores the different payloads and interactions.
Read the full blog here.



CounterCraft Awarded Production Contract by the U.S. Department of Defense
This was definitely one of our most exciting announcements of the year, and it was an important one not just for CounterCraft but for global security. In this article, we announced that CounterCraft was awarded a production contract in order to more easily scale our deception technology solution across the United States Department of Defense. The DoD chose CounterCraft after an industry-wide down selection process to meet key mission-critical performance requirements, such as: Advanced Threat Detection and Response, Local Indicators of Compromise, Machine-Readable Threat Intelligence, Proactive Threat Hunting, and Active Attacker Engagement. This contract allowed our award-winning and innovative Cyber Deception Platform to be used not just with back-office software but high-priority operational units
Read the full blog here.


New Threat Actor Alert: CC0628
This article was the first in our series of New Threat Actor alerts. Written by our threat intel team, the post outlines the first of several new threat actors in the wild. By locating a decoy machine in a U.S. web server of a well-known provider, with an ssh port open to the outside network, we have found many attackers that approach the machine and try to access it, oftentimes with sheer brute force. Read the article to discover the IOCs and TTPs of different threat actors we have uncovered, and be sure to check back or follow us on LinkedIn for updates.
Read the full blog here.
