Cyber attacks on critical infrastructure and physical systems are on the rise. From the Colonial pipeline attack to the Florida water plant hack, the threat has become so imminent that the Cybersecurity & Infrastructure Security Agency has released several warnings, including the October 2021 “Ongoing Cyber Threats to U.S. Water and Wastewater Systems” alert.
Operational Technology (OT) networks, such as SCADA and Industrial Control Systems (ICS), have many unique characteristics that make defensive countermeasures against cyber attacks a challenging job.
We’ve created a full data sheet on improving OT security that you can download here. Read more about the specific challenges and our solution below.

The Specific Challenges of OT Security
OT networks are critical, occasionally fragile, and often employ obsolete IT technology. Industrial machines can have an operational life of many years. This means that there are systems in the wild that are using operating systems that are no longer supported by the manufacturer. And this is only the beginning of the challenges posed by these OT networks:
- The use of legacy systems no longer supported by the manufacturer is the norm in OT.
- Many HMI systems run on bare-bones operating systems and hardware that has been “optimised” to be the minimum necessary.
- Patches are often not compatible, or you have to wait months for an “HMI compatible” patch to be made available by the manufacturer.
- An “air gapped” network is not always an option, as there may be data from those devices that needs to be accessed.
- Patching devices may require a connection to either the Internet or a central patching server, such as a Windows Server Update Service (WSUS) or RedHat Satellite.
- Consultants and vendors may bring malware in on laptops and connect those systems to the SCADA network for maintenance purposes.
- Performing software updates on SCADA devices can be difficult. The vendors of these devices or the integrators used to bring them online may not allow them to be updated without the vendor or integrator first performing appropriate regression testing.
- There is a fear of disturbing equipment that has been operating fine for years, sometimes decades, for a security patch.
- Implementing additional security controls on SCADA networks or devices like anti-virus or a host-based intrusion detection system might cause some unexpected behaviors, such as system slowdowns or active responses to perceived attacks.
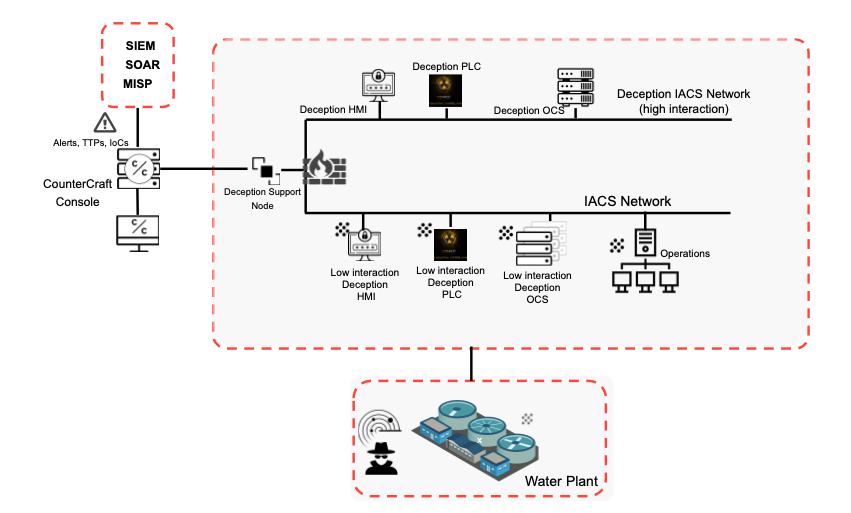
As these difficult-to-defend networks are ever more vulnerable to attack, it is vital to find new security solutions. Deception technologies can be used to provide an extra dimension of security to OT networks. With deception, it is possible to detect malicious activity, collect valuable threat intel and also create and respond to adversary activity in real time.

“The CounterCraft Cyber Deception Platform can be used to add zero impact security and gather valuable first-hand threat intel on those who are targeting your OT systems.”

All of this is achieved with zero impact on existing systems, and zero risk to business continuity. It goes without saying that as OT is such a critical component, protecting it correctly is key. Using deception technology provides an effective way to add an extra layer of protection to your existing security systems.

Example Deception Campaign for OT Security
Here is a real-life example of how deception has worked to protect OT networks. An attacker gained access to a plant network and scanned the network for information on network nodes looking for unpatched systems and points of entry to exploit.
Plant Network Attack

- The Deception Director deploys an OPC server, HMI, and emulates PLCs.
- The attacker is lured with deception techniques and is deceived into thinking he has discovered a production OPC server. He starts to engage by scanning for open ports known to exist on vulnerable OPC servers.
- Because the deception platform was deployed, the attacker was actually lured into the CounterCraft engagement rules as the bad actor began his initial reconnaissance. Believing that he was successful, he dropped the payload with the intent to complete his mission. This occurred in a contained decoy on the deception host.
- In this process, the CounterCraft DSN captured the attacker’s IP address and the information on the infected node. Additionally, a port was opened up to the attacker command and control and additional information on attack methods and tools was collected.
- A substantiated alert was recorded in the threat intelligence dashboard and was sent to the security operations team. The infected device was immediately blocked, quarantined, and taken off-line for remediation.
- The forensics information was captured and forwarded to the SIEM for appropriate action. The security team used the forensics information to identify remediation activities for existing production OPC servers.

The Result
The shutdown of water process control pumps and potential inconvenience and harm to human life was successfully avoided.

Benefits
Deception can help in the proactive protection of critical assets without imposing any burden on the normal operation of services.
- CounterCraft’s approach does not require modifying the existing SCADA network.
- No need to insert additional inline devices.
- Deception assets are simply plugged into the network as any other system would be and set up to run services that look like other devices on your SCADA network. Further intelligence will be obtained from the attacker’s actions, leading to a better understanding of the attacker’s objectives and TTPs used. Other deception hosts like physical WiFi routers or PLC emulations can also be an effective part of a deception campaign.
- The CounterCraft Cyber Deception Platform does not base detection on known signatures or traffic analysis, but on human actions.
- It can be configured to look like specific devices on a typical SCADA network.
- CounterCraft allows for the monitoring of attacks designed specifically to target the current infrastructure.
- Deception offers you earlier detection, along with immediate identification of the breach and compromised asset.
- Understanding TTPs of the attacker leads to local actionable Intel to share with SIEM, SOAR and the rest of the security team.

To learn more about how deception can help you improve your OT security, download the full data sheet here.
For more examples of how deception has prevented OT attacks and to learn more about CounterCraft, contact us.





