State-sponsored cyber operations now target the private sector, not just other nation-states. They also take a wide variety of forms. To safeguard their organizations, CISOs must adopt proactive, intelligence-first strategies.
In today’s world, war is rarely just boots on the ground. Instead, warfare takes place on a digital battlefield where the combatants are often invisible.
It only used to be governments that needed to worry about cyber warfare. However, state-sponsored attackers now also target the private sector. Energy, finance, telecoms, healthcare, and cloud platforms have become strategic targets, at risk of attack from nations that are hostile to theirs. Cyber warfare is taking place constantly, not just during times of geopolitical tension.
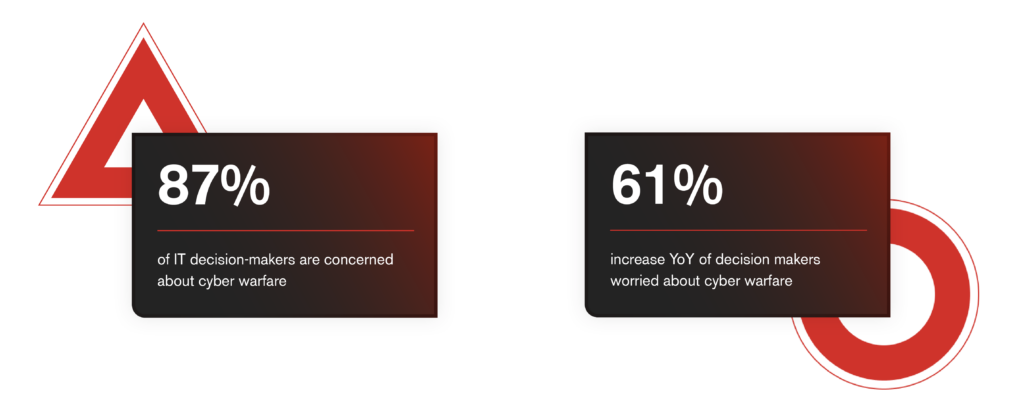
The 2025 Armis State of Cyberwarfare report found that 87% of IT decision-makers are concerned about cyberwarfare, up sharply from 54% in 2024. They’re worried because cyber warfare campaigns are designed to stay quiet, blend in to maximize dwell time, and gather sensitive information before any visible impact occurs.
For CISOs, defending against cyber warfare by reacting to incidents cedes control – and is a losing strategy. Instead, it’s about understanding enemy intent early and executing targeted counter-strategies while outcomes are still controllable.
What is Cyber Warfare?
Cyber warfare refers to politically motivated cyber operations conducted by nation-states or their allies. They aim to disrupt or destroy critical infrastructure and digital networks, giving the actor a strategic advantage without triggering conventional military conflict.
Nation-states use cyber warfare because it’s extremely accessible. You don’t have to be geographically close to an enemy nation to launch a cyberattack on it. Nations can run cyber attacks against anyone they choose, 24/7. There’s also a significant element of plausible deniability, particularly if a nation routes its cyber warfare through proxies or criminal groups. The impact is the same, but the government’s hands look clean.
Cyber warfare has a broad scope. It can create economic disruption, destabilize essential services, compromise national security, and in extreme cases, lead to loss of life. Energy grids, financial systems, communication, healthcare, transport, and cloud platforms are all targets.
For CISOs, the distinction between cybercrime and cyberwarfare matters:
- Cyber criminals– motivated by profit and payouts (e.g. ransomware)
- Nation-state actors – motivated by intelligence gathering, long-term disruption, or lower-level persistence. They have deeper pockets, patience, and sophisticated (often AI-powered) tools
AI has accelerated the rise of cyber warfare by drastically lowering the barriers to entry. Armis found that 64% of IT leaders agree that generative AI allows smaller nations and non-state actors to become near-peer threats.
What are the Goals of Cyber Warfare?
Cyber warfare serves a very different purpose from other types of cyber operations, such as ransomware. Ransomware gangs aim to extract money and move on. On the other hand, state-sponsored cyber operations aim to create strategic panic, long-term leverage, and political advantage.
The types of strategic panic that nation-states and aligned actors aim to create can be divided into four broad categories:
Espionage
Nation-states use cyber operations to steal sensitive information, thereby gaining an advantage. This includes military secrets, government data, and intellectual property. This is where persistent access matters more than speed. If an adversary can linger in the network for longer, they’ll discover more critical information.
Sabotage
Cyber operations are used to disrupt essential services such as power, water, financial networks, and transport. Even the slightest disruption can cripple a nation, creating economic disaster and undermining confidence in the country as a whole. For example, a cyber attack on Iran’s network of 4,300 gas stations meant that no one could use their government-issued fuel payment cards for more than two days, creating long lines and massive disruption.
Destabilization
Propaganda and disinformation operations aim to erode trust, manipulate public opinion, and interfere with the democratic process. AI has accelerated the scale of these campaigns and made them more realistic. On social networks, a single video can incite public unrest in the real world.
Strategic Advantage
In hybrid war scenarios, cyber operations can bolster physical action. Malicious actors can blind radar systems, leak sensitive troop movements, or weaken a nation’s ability to respond. The goal here is to secure an advantage before the confrontation takes place. This was especially prevalent in the run-up to Russia’s invasion of Ukraine.
What are the Most Common Types of Cyber Warfare?
There are four common ways that state-sponsored attackers can achieve those goals:
Espionage and Data Theft
Advanced Persistent Threats (APTs) focus on long-term access rather than a quick hit. When an attacker can linger undetected in the network for an extended period, they can gather more information and exert greater leverage.
For example, the China-linked Salt Typhoon campaign targeted US broadband providers, including Verizon and T-Mobile, attempting to access legitimate, court-ordered wiretapping systems that live on their networks. The objective was intelligence and surveillance, not data theft alone.
Infrastructure sabotage
State actors use digital means to target operational technology (OT) and industrial control systems (ICS), causing physical disruption.
In 2023 and 2024, a group called CyberAv3ngers, linked to Iran, targeted water and energy grids in County Mayo, Ireland, leaving residents without water for two days. There was also a less disruptive attack in Aliquippa, Pennsylvania. CyberAv3ngers are known to use AI models like ChatGPT to refine their techniques. It’s no surprise that 80% of respondents in the utilities sector to Armis’ survey believe AI-powered attacks are a significant threat.
Distributed Denial-of-Service (DDoS)
DDoS is used in warfare as a tactical smokescreen. It distracts security teams, disrupts communication, and suppresses government and media messaging during wider operations.
Propaganda and Disinformation
Cyber warfare increasingly targets the human mind. AI-generated deepfakes and bot networks on social media can influence public opinion at scale, spreading disinformation around the world before the truth can mobilize.
What are Recent Examples of Cyber Warfare?
Recent conflicts show how cyber warfare now operates in conjunction with political and military action, rather than as a standalone activity.
The Russia-Ukraine Conflict
Cyber warfare was an essential part of Russia turning the screw on Ukraine, even before the armed invasion began.
In this war, cyberspace is an active digital front, with Russia employing destructive “wiper” malware used to erase essential data within Ukrainian organizations in the energy and media sectors. See how we uncovered nation-state threat actors before a DDOS attack on Ukraine in this webinar.
There is also the hybrid nature of cyber warfare on display in this conflict, with cyber attacks timed to coincide with missile strikes and physical operations, adding to the disruption and chaos during critical moments.
Global Election Interference
State-aligned actors from Russia, Iran, and China have targeted elections across the US, UK, and EU. GenAI has amplified these campaigns, with AI-generated fake news, audio, and video employed to undermine trust, distort narratives, and cast doubt on democratic outcomes. We have a webinar on the threats to elections, Democracy Goes Digital.
Critical Infrastructure Targeting
Pre-positioning has overtaken immediate disruption as the goal when targeting essential infrastructure. In this more strategic approach, adversaries embed themselves long-term in the systems of ports, rail networks, power grids, and more, creating leverage that can be activated during future political or military conflicts.
The AI Multiplier
Artificial Intelligence has accelerated cyber warfare by saving time, lowering costs and adding scale. What once required long preparation times and skilled teams of cyber attackers can now be automated and adapted in minutes.
State-sponsored adversaries now use AI as a production line for cyber attacks. Examples include:
- Automated vulnerability discovery – AI can scan vast attack surfaces to identify weaker potential entry points faster than defenders can patch
- Better phishing materials – Adversaries use AI to create hyper-realistic emails to bypass filters and look believable to the recipient in language, tone, and context
- Disinformation at scale – With AI, bad actors can flood information channels with deepfakes, manufactured audio, and false narratives to confuse incident responders and decision-makers during a crisis
Traditional defense methods struggle here. Firewalls, EDR, and standard SIEM rules are designed to spot known malicious behaviors. But they are far less effective against a human adversary using harvested legitimate credentials, living off the land in your network.
This is where it’s essential to engage with the adversary as early as possible, before the main strike takes place. Deception changes the dynamic by forcing interaction. When AI-driven operators probe for vulnerabilities, test access privileges, and gather information, deception assets directly expose their intent and methods. Instead of responding to alerts when it’s already too late, defenders gain evidence and can take action while outcomes are still controllable.
How Can Organizations Defend Against State-Sponsored Threats?
State-sponsored cyber warfare exposes the limits of traditional defense. Perimeter tools and reactive monitoring fail against APTs using legitimate credentials and native tools to operate quietly inside the network.
The key to effective defense is early engagement. Here are four strategies that work.
Deception Technology
Deception deploys realistic digital twins that mirror production systems but without risk. When attackers conduct reconnaissance, they interact with decoys instead of real assets. This flips the advantage:
- Attackers expose their intent through interaction
- Alerts are high-fidelity. Any interaction with a decoy is automatically a bad actor
- You can deploy deception early in the kill chain before final impact
What makes deception technology so effective against cyber warfare tactics is early adversary engagement. To an attacker, a decoy system is a target they cannot resist. They can’t help coming out of the shadows to examine what’s inside. By the time they realize it’s a decoy, they’ve already shared their compromised identities and malicious tactics, delivering rich, behavioural threat intelligence to you in real-time.
Stronger Active Directory Security
Attackers make identity their primary target, so they can escalate privileges and conduct lateral movement within the environment. CISOs can defend against this by deploying continuous monitoring for unusual authentication patterns, in conjunction with decoy credentials inside Active Directory. This exposes malicious behavior without disrupting legitimate users.
Discover more about Active Directory attacks and the hybrid cloud conundrum in this article from CounterCraft.
Threat-Informed Defense
Don’t rely on generic threat feeds that lack relevance. Defenses should map directly to MITRE ATT&CK techniques based on known adversaries targeting your industry.
Enhanced Malware Analysis
Advanced malware can evade standard sandboxes. Instead, execute malware in realistic, instrumented environments to reveal intent, behavior and next steps.
Discover more about malware analysis with CounterCraft’s tailor-made resources.
The Strategic Shift to Active Defense
State-sponsored threats against civilian targets have changed the rules. Security that is merely “good enough” is no longer viable. Passive controls and reactive alerts leave defenders scrambling after lost leverage.
Today, defense requires a shift to active engagement. Organizations must expose intent early, disrupt adversaries during reconnaissance, and act while they still control the outcomes. When state-aligned actors use AI to increase scale and effectiveness, proactive defense is all the more critical.
Ready to turn the tables on advanced adversaries?
Request a demo with CounterCraft today and see how threat intelligence powered by deception protects your most critical assets.
Key Takeways
- Motivation matters – Cyber warfare is driven by strategic and political goals, making state-aligned attackers more persistent than other cybercriminals
- Hybrid threats – Modern conflicts combine data theft, infrastructure sabotage, disinformation, and more to maximize impact
- AI is the accelerator – GenAI has enabled state-sponsored threat actors to work faster and more effectively to cause disruption
- Deception is critical – High-fidelity decoys are one of the few ways to reliably detect human adversaries and reveal their methods
- Be proactive – Waiting for an alert is too late. To protect your assets, you must actively hunt and engage threats in controlled environments