Although many principles of deception have been applied in military and intelligence domains for many years it has only been applied within the enterprise space for the past few years as technology and understanding has grown to provide cyber defenders with a new capability.
If your organisation is new to the concept of Cyber Deception as an emerging component in an enterprise defence in depth strategy, then we hope to introduce you to some of its value now.
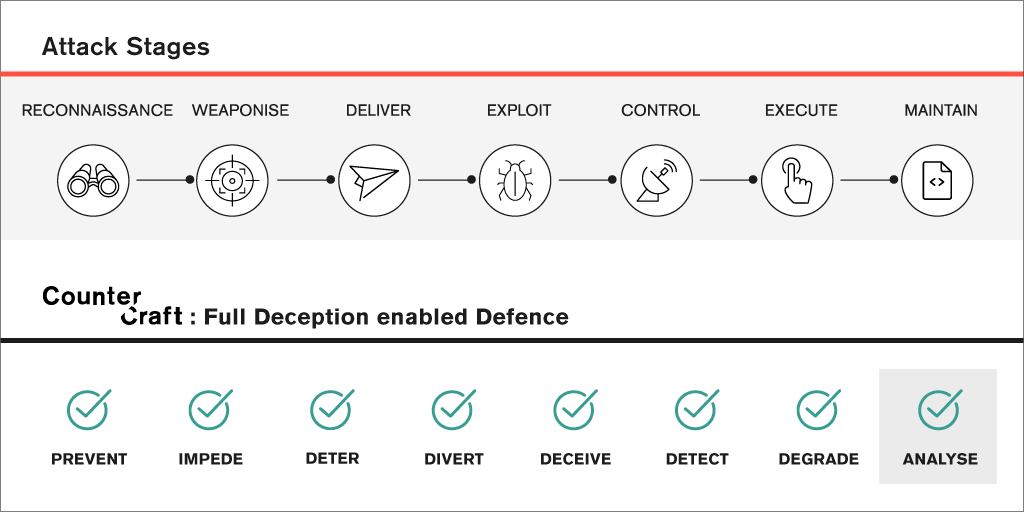
To understand how cyber adversaries may behave, models that are termed Attack Lifecycles, have been developed to describe the stages that most attacks will go through to reach a goal, the most commonly referenced model being that originally developed by Lockheed Martin – the Cyber Kill Chain®.
Using this model as a background we can describe how deception thinking and technologies can really improve the ability of organisations to protect their information assets and business resilience. Below is the blend of stages and the potential deception options that can be part of a relevant defender Course of Action (CoA).
The Defender Deception options were originally articulated by Mitre Corporation in a paper published in November 2013 looking to establish vocabulary that described cyber defence approaches in support of Cyber Resilience.
We can use the Kill Chain model interacting with Defender Deception methods to describe some of the ways that deception can work through an Attack Lifecycle. We could have chosen the Mitre ATT&CK model which has more stages, or other models, but we feel that once you have the sense of any Attack Lifecycle then you can choose the specific models that resonate best with your particular environment and granularity of analysis.
The stages are labelled primarily from the attackers’ viewpoint:
Critically you can see that at every stage, analysis is a major outcome, which is the basis for good cyber threat intelligence production.

Improve Cyber Defence Using a Protect, Detect & Respond Philosophy – How Deception Helps
As in many areas of life and business the Pareto principle appears to apply, and the world of cyber security is no different. Through deploying standard enterprise security technology such as firewalls, anti-virus, IDS & IPS; adopting security controls such as CIS Top 20, ISO 27001; staff security & awareness training; and maintaining good software patching disciplines it is likely that 80% of cyber attacks will be successfully mitigated.
Which leaves the 20% that aren’t being mitigated for a range of reasons.
No matter how good the defenders get the over-riding issue is that organisations are made up of people, processes and technologies, all of which have vulnerabilities that can be exploited. So with the sheer scale and dynamics of modern organisations it is becoming apparent that if you have something of value – intellectual property, money, personal information, competitive advantage – then a motivated cyber adversary will have found a way to access your systems.
It could be argued that our vulnerability landscape is increasing rather than diminishing due to the rate that software, the app economy, mobile devices and the rush to digital business transformation causes quick semi-tested solutions to be deployed. There is a desperate need to minimise the impact this is having on information and cyber security.
Deception technologies and deception operations work on the principle that the adversary is either already in your enterprise, and is well hidden, or that they are making their way through the stages of an attack lifecycle – and critically that they also have vulnerabilities.

Building an Advantage Through Intelligent Deception
Improving knowledge of your adversaries ahead of any subsequent breach or cyber incident will give you as a defender the beginning of an advantage. The topic of threat intelligence and organisations in both the public and private sectors being providers, consumers and sharers has grown quite dramatically over the past 5 years. As this has happened there have been major moves to standardise language and processes related to how threat actors behave and can be categorised according to their visible Tactics, Techniques and Procedures (TTPs).
Whilst this undoubtedly provides Chief Information Security Officers with better information that can be applied to evolving their organisational situational awareness, getting to a point of relevant, actionable threat intelligence has remained difficult to achieve – until now.
Deploying Deception Assets across an enterprise all the way from remote internet-based cloud services through to executive mobile devices, servers or even WiFi access points enables a business context specific 1st Party Threat Intelligence capability to be built, refreshed and acted upon in real time.
The software-based Deception Assets are designed to blend in with the standard enterprise ICT environment, and are deployed intelligently as required by the nature of the enterprise cyber defence strategy and threat landscape. The assets can be scaled to match the breadth and depth of a required deception layer, in effect offering an attractive and dynamic “attack surface” to engage multiple adversaries with targeted Deception Campaigns.
As adversaries engage with aspects of the deception environment, believing they are navigating the real enterprise, specific information is gathered by the assets through a combination of agentless and complex software Deception Agents™ at many levels, building a comprehensive activity trace record.
This detail is gathered across a secure deception telemetry network embedded across the enterprise that is managed by Deception Support Nodes (DSN) feeding in to the CounterCraft Deception Director™.
From this central vantage point enterprise cyber defence personnel can both create and deploy Deception Campaigns as well as monitor in real time the current visual status of ongoing campaigns and adversaries in different stages of an attack lifecycle.
Subsequent strategic and operational decisions can then be based on real evidence – before a breach, exfiltration of data or manipulation of critical business processes has occurred.


Why not consider using deception technologies and methods as part of your enterprise defence strategy?

Feel free to download our latest documents or contact our deception artists team to Learn more about the CounterCraft Cyber Deception Platform.

Author: Michael Eaton, Product Marketing at CounterCraft