What is Profiling?
The FBI refer to profiling as ‘reverse engineering a crime’ – the process of analyzing a crime scene to build a picture of the criminal, ultimately leading to an arrest.
In cyber terms, profiling is a process of identifying individual characteristics and traits displayed by the adversary. This article aims to show how we can profile cyber adversaries using deception technology.

Some Context…
When tracking a serial killer, the FBI looks for characteristics they can use to identify the murderer. They base the profile on the how and when of the crime, and use detailed analysis of the crime scene to enrich the data they gather.
Characteristics such as the choice of victim, where the crime took place, the level of organization of the killer, the time taken and post crime behavior, the sophistication of the crime, and the choice of weapon all provide important data about the motives, tools, techniques and procedures of the criminal. In the same way, we build profiles of cyber adversaries to build a picture of their objectives, modus operandi, and ultimately their future intentions.
Another example of using telltale fingerprints to profile an adversary comes from the Operators at Bletchley Park, once the top-secret home of the World War Two Codebreakers, who were able to identify U-Boot radio operators by the way they keyed their messages. On some occasions, they were able to identify troop movements just by how the Operators changed.
In CounterCraft, we have some telltale clues, too. Finding certain tell-tale commands in a history file is a dead giveaway that our Customer Success Manager has been active on a deception host!

How profiling is useful
Let’s be clear, we’re not talking 100% guaranteed attribution here. Profiling is not about getting the name, address and social security number of an adversary— that is a whole different story. What we mean is the process of gathering a body of evidence that matches witnessed activity with known traits related to a given adversary.
A good profile provides valuable awareness in four areas:
- What has the adversary been able to do?
- What are their objectives?
- Who are they?
- What are they going to do next?
This is vital situational awareness that only real-time threat intelligence can provide.
With this data, you can respond effectively to any attack with the confidence that your response is correct and justifiable based on the threat you have identified. That means you can be sure that the response is the right one at the right time.
Read our popular post on how understanding the enemy can lead to prevention.

How CounterCraft Helps you Profile an Adversary
The key to profiling an adversary is the ability to detect and collect their activity from the deception environment in real-time. The CounterCraft Deep Sense™ Agent captures all adversary activity from the deception host. It is able to relay this data via the ActiveLink™ command and control to the Deception Director in real time. As has been discussed elsewhere, this data is converted into event data.
Event data is actionable, timely and accurate threat intelligence. We use the event data as the foundation of the adversary profile. The following section describes how event data can be exploited.

IP Addresses and other Indicators of Compromise (IoCs)
IoCs are extremely useful for linking to known Threat Actors. Event data is parsed to extract key observables. These observables provide really useful IoC data such as IP address data or command arguments. As an example, the CounterCraft Threat Actor database contains hundreds of IP addresses that are linked to known APTs. Identifying a source IP address is an important adversary characteristic. Linking to the CounterCraft Event enrichment data allows you to obtain a wealth of information about the adversary.
You may be thinking that IP addresses can be spoofed, and are easy to change. While that is true, it’s still a good technique to take any IP address detected within a deception environment and pipe it directly into your SIEM. If you detect the same IP address anywhere else in your network, you have direct evidence that that machine is compromised.
In addition, the CounterCraft Deception Director has access to external data feeds that can be used to enrich this data and enhance the power of their threat intel. In the case of IP addresses, we can automatically provide geo-location data; identify if this IP address is linked to any previous malicious activity or if it is a known Tor-node.

Patterns of Behavior & TTPs
We are creatures of habit. We all have our own ways of doing things, and cyber adversaries are no exception. David Bainco introduced the concept of the Pyramid of Pain in 2013 (which we talk about here ) to quantify this. In a nutshell, changing the hash value of a payload is trivial, but changing the tools or TTPs from attack to attack is really challenging.

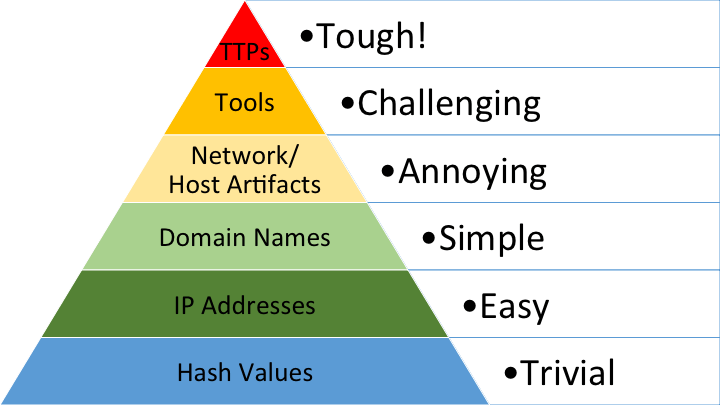

Using Red Teamers as an example, each member of the team will have their own set of tools, their own penetration methods and their own sequence of actions that they perform to try and compromise a system.
By cataloguing these characteristics, you have a powerful way to identify an adversary, even to the point of identifying a specific individual by their characteristic tools, techniques, tactics and procedures.
The CounterCraft Shell-Line event type is a specific tool that is a real help with identifying unique adversary behavior by providing specific detail on what commands are being executed on the deception host. This can include, for example, everything that is executed through a bash shell – mistakes and all. Similar coverage exists for Windows hosts too.
By monitoring the commands used by an adversary, you can tell a lot about them: how familiar are they with the OS, or distribution; do they use specific command arguments (netsat -nt, -upant etc), do they always use commands in the same order; do they make frequent mistakes?
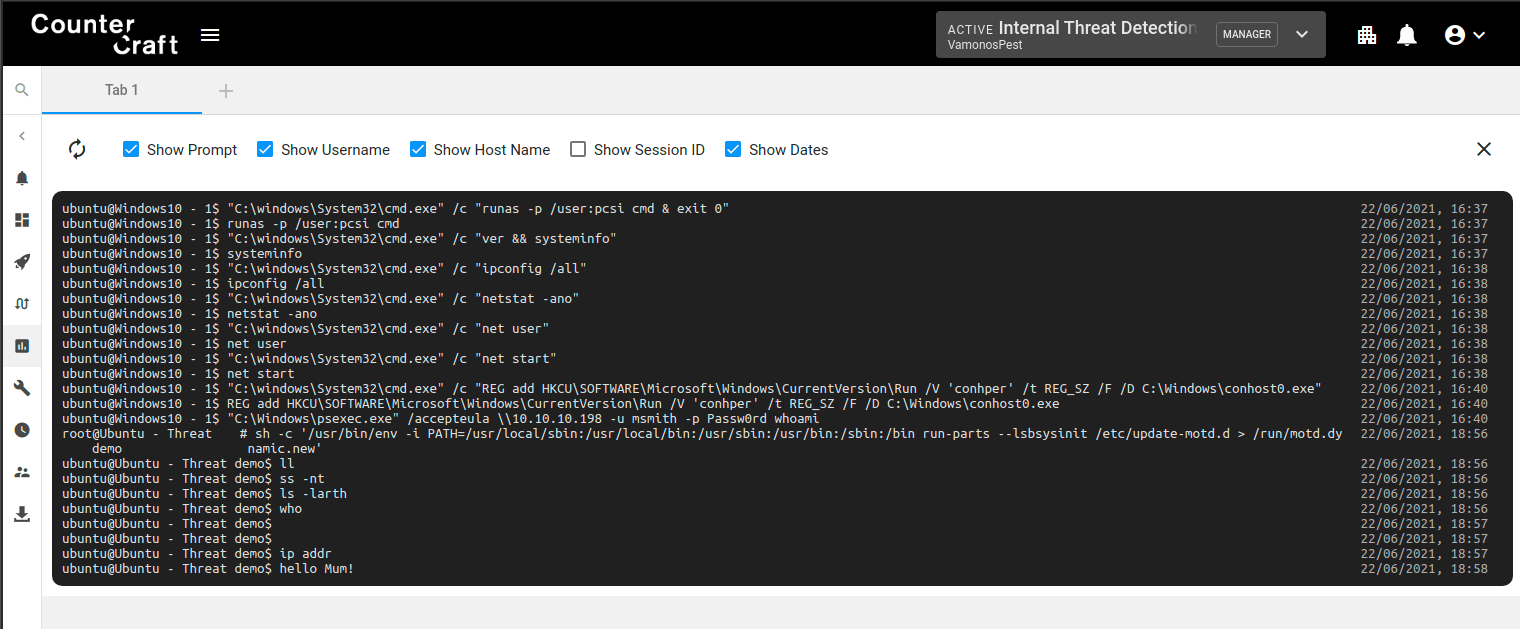
Shell-line screenshot, showing mistakes and command usage.

By profiling the commands and techniques an adversary uses, and by noting their quirks and idiosyncrasies, it makes identification of this adversary much more likely if they are spotted again. You can only get this sort of attribution by monitoring adversary behavior, and the best way to do this is within a deception environment.

Objectives
Identifying the attack objective is an important part of the adversary profile. Is this just an opportunist who got lucky or is this part of a focused criminal attack aimed specifically at your organization? Using deception is a unique way to identify an attacker’s objective.
By creating deception campaigns with attack trees that provide the adversary with choices, you can gain valuable intelligence from how they respond: DOS or data? Do they go for the user data? Do they go for the tactical data? Do they go for the IP or production data? How long do they spend in a particular area? Do they ignore everything and just upload a malicious payload?
You can use these observed behavior patterns to identify how the adversary prioritized their actions, and combine this with the IoCs and TTPs deployed to see how the tools they use advance their goal. You can also measure the time taken in different areas to judge the importance to the attacker.

What Next? Using the Profile
So we’ve discussed various tools to help you profile your adversary, so now how do we use this profile?
As we discussed before, a profile provides answers to the four key questions:
- What has the adversary been able to do?
- What are their objectives?
- Who are they?
- What are they going to do next?
These questions provide you with the awareness of the situation to respond effectively. The response may be a change in a configuration or a modification to a security policy or an update to user training. It could also be an automatic change by setting up rules to trigger on a specific behavior pattern to manipulate the adversary within the deception environment or link to an orchestration platform to initiate a response in the wider security ecosystem.
Whatever the response, by having a good understanding of the activity, motives and identity of the adversary gained from profiling techniques and data gathered from your deception environment, you can predict with greater confidence what they are going to do next and defeat them. In the words of our old friend Sun Tzu:


Next steps:
To find out more about any of the topics discussed in this article, please reach out and get in contact with CounterCraft. We are only too happy to explain what we do and how we can help you get the best out of deploying deception – from an initial conversation or simple demo to a fully featured deployment.



Richard Barrell is the Product Manager at CounterCraft, as well as managing projects in the Government sector. You can find him on LinkedIn.
