The problem with IT environments is that they are built to operate in relatively static configurations, meaning adversaries can easily study any organization’s static systems and networks and execute their attacks. Moving Target Defense (MTD) assumes that all systems will be compromised at some point, so it seeks to make systems more difficult to breach by constantly changing the attack surface (IP addresses, operating systems, software versions, and configurations). Automated Moving Target Defense (AMTD) is the evolution of this strategy, leaning in towards an automated version that can be incredibly effective.
Gartner is encouraging the market to focus on this promising new prevention-based strategy. DHS warns that the static defense approach most organizations apply leaves them vulnerable and recommends embracing proactive security solutions such as AMTD.
Take our quiz today to find out how deception technology can work for your organization >
Unlike other traditional cybersecurity tools that focus on detection and remediation, AMTD is a proactive solution. The idea behind AMTD is to move away from the static paradigm and create moving targets that constantly shift and change, disrupting the traditional attack path used by adversaries.
AMTD and Cyber Deception : The Way Forward
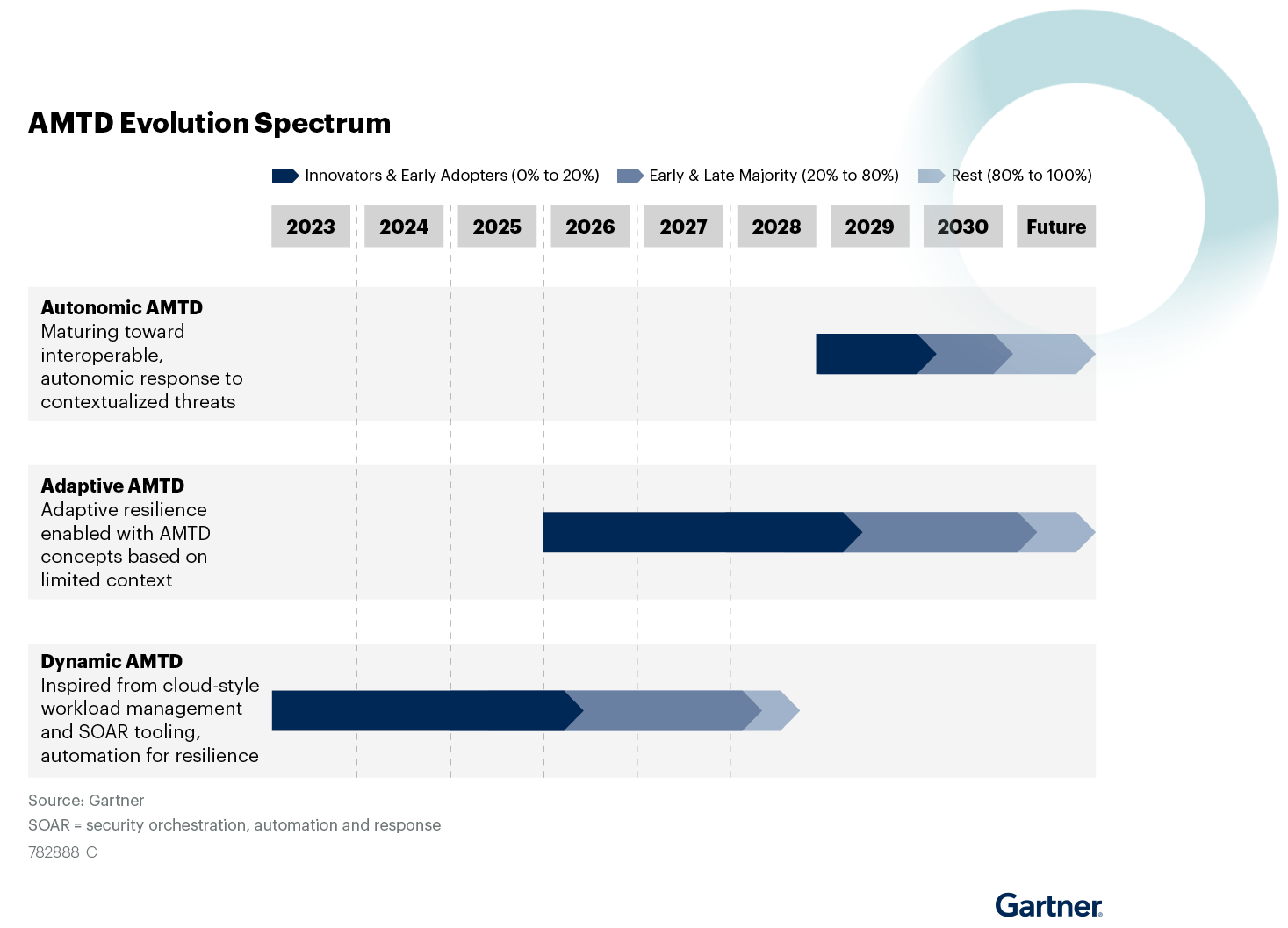
Gartner has mapped out an AMTD Evolution Spectrum that shows how this dynamic approach might transition to a fully automated solution in 10 years.
Deception techniques are part of the “future of cyber defense”, according to Gartner, with the clear objective to make adversaries’ lives more difficult and allow organizations to take back control of the situation.
AMTD and deception techniques often go hand-in-hand in cybersecurity strategy, as deception creates environments that alter the attack surface from the attacker’s point of view, providing a perceived path of least resistance to achieve their goals and objectives. This lures them into a thoughtfully designed trap, pushing them to execute malicious activity and expose their tactics, techniques and procedures.
Four Ways to Use Deception Technology in AMTD
One of the four elements that makes up an ATMD strategy, according to Gartner, is the “use of deception technologies”. AMTD has various applications across different domains to enhance overall cybersecurity posture against advanced persistent threats, and CounterCraft’s sophisticated deception platform is an integral part to implementing them.
Read on to find out how AMTD works in the following use cases, and how deception technology supports its implementation:

Cloud Security
AMTD can enhance the security of cloud environments by continuously shuffling and reassigning virtual resources, from machines to containers, across different physical hosts.
CounterCraft in the cloud: CounterCraft supports deploying deception at multiple layers in cloud environments and has automatic cloud host management capabilities. The PlatformTM configures real vulnerable virtual machines (AWS EC2, Azure VMs, Digital Ocean Droplets, and more), altering the attack surface from the attacker’s point of view, luring them into exploiting these services to gain control and move laterally. The Platform then collects adversary intelligence and sends high-fidelity alerts to users’ security tools.
Hardware Protection
AMTD techniques can dynamically alter system configurations, routes, or access controls, making it difficult for attackers to understand and exploit system vulnerabilities.
CounterCraft in ICS/OT: CounterCraft can be deployed in ICS/OT networks across critical infrastructure, manufacturing and oil & gas plants, and supports deploying deception at multiple layers in ICS/OT environments (PLC/RTU, IEDs and controllers, HMI systems, applications, databases and file Servers and breadcrumbs). CounterCraft can deploy an OPC server, HMI, and emulated PLCs, which then works to lure adversaries in and engage them by scanning for open ports known to exist on vulnerable OPC servers. The security team is alerted from the moment the adversary begins their initial reconnaissance and is able to observe as the adversary drops a payload with the intent to complete their mission.
Host and Endpoint Security
AMTD techniques can be applied to individual hosts and endpoints, randomizing system attributes, such as operating system versions, software configurations, or user privileges. By frequently changing these attributes, AMTD can mitigate the impact of zero-day vulnerabilities and limit an attacker’s ability to exploit specific system weaknesses.
CounterCraft in endpoint & hosts: CounterCraft is able to create credible decoy SWIFT terminals, creating uncertainty and confusion for the adversary. The portal itself has a login function that corresponds to the distributed credentials and decoy users that have been planted in the Active Directory. Adversaries are tempted to exploit these vulnerable hosts while the security team observes their attack vectors, paths and TTPs, learning in real time from their behavior.

Network Security
AMTD can be used to dynamically change network configurations, such as IP addresses, port numbers, or network paths, making it harder for attackers to identify and target specific network components, thereby reducing the risk of successful attacks.
CounterCraft in internal networks: CounterCraft can be deployed in an organization’s VLAN by configuring a similar VLAN to their production with vulnerabilities that are attractive from an adversary’s point of view. This allows organizations to identify exploitable vulnerabilities (even new ones) in software used across the corporate network, and gain advanced insight into production service weaknesses.
Benefits of Deception as Part of an AMTD strategy
Above, we have seen how deception plays a critical role in AMTD’s comprehensive approach to cybersecurity, allowing organizations to stay ahead of novel threats and safeguard their assets and reputation. The integration of these deception techniques as part of an AMTD security infrastructure has several benefits.
- Detect threats early: As soon as there is activity in a decoy breadcrumb or server, a high-fidelity alert is delivered to the security team in about 20 seconds, providing the team with situational awareness, threat hunting capabilities, and the ability to respond quickly and mitigate the damage caused by the attack.
- Deflect adversaries: CounterCraft’s real IT environments make it difficult for attackers to distinguish between what’s real and what’s fake, increasing the chances of them interacting with decoys and honeypots. This provides valuable intelligence on attackers’ tactics and techniques.
- Reduce of risk: Deception reduces the risk of real assets being compromised, as attackers are deflected to decoys and honeypot servers, which do not contain valuable data.
- Be cost-effective: CounterCraft customers reduce adversary dwell time from 100+ days to just hours. Reducing attacker dwell times results in less impact and a much lower cost, as breaches with lengthier dwell times tend to be proportionally more expensive. Reducing dwell times by using deception technology results in a cost of breach savings of approximately 51% ($4.35M cost of a data breach in 2022).
- Collect user and device behavior: By analyzing adversary behavior on a system or network, it makes it easier to identify potential threats and take action to prevent them thanks to proactive threat hunting capabilities.
As you can see, AMTD is a proactive approach that ensures organizations can detect and respond to attacks before adversaries reach the production environment. And, more importantly, it allows teams to gather intelligence on attackers’ tactics and techniques. This is one of the reasons why Gartner forecasts AMTD as “the future of security”.
CounterCraft’s solution provides rich adversary-generated threat intelligence in seconds and adds a valuable data stream to EDR/XDR/SIEM/SOAR and AI-based detection systems. CounterCraft fills the gap where other security systems fail.
To find out if your organization is ready for deception, take our quiz here. Get in touch if you’d like to schedule a demo to see our cyber deception solution in action.
