Industrial Control Systems (ICS) play a vital role in ensuring the secure and efficient operation of critical infrastructure (CI) across diverse sectors. The security and resilience of ICS is a foremost objective for both governments and private organizations. Today, we find ourselves in the Fourth Industrial Revolution, in which the fusion of IT and Operational Technology (OT) systems offers new opportunities for organizations to enhance operational efficiency, meet customer demands, and keep up with the pace of digital transformation.
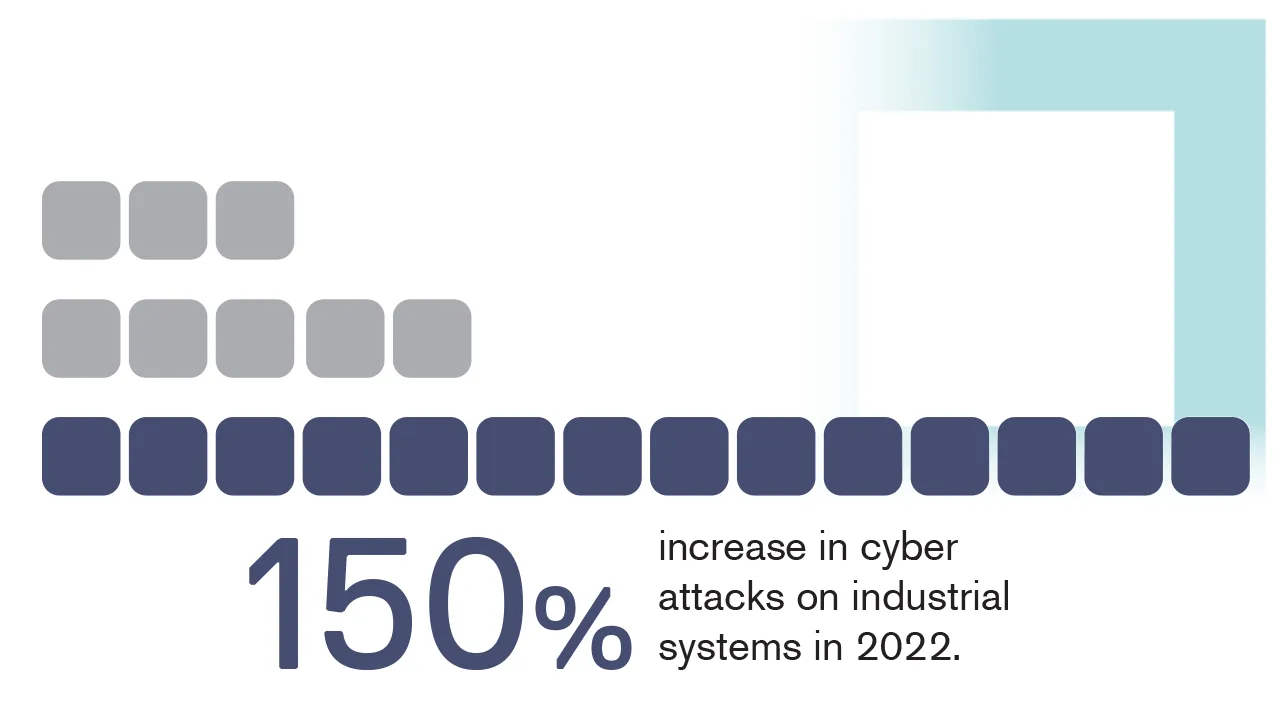
However, it also significantly amplifies the complexity and vulnerability of OT cybersecurity by expanding the attack surface and introducing new digital risks to critical infrastructure. And that means business disruption. In fact, in 2022 there was a 140% increase in cyberattacks on OT, SCADA, Critical Infrastructure, and Industrial Control Systems (ICS) with direct real-world repercussions1. The deployment of cutting-edge technologies is a must to fortify critical infrastructure against contemporary and emerging threats.
We’ve created a full datasheet on how deception technology can improve the security posture of ICS and OT networks that that you can download here >>>
The Top 10 Threats to OT/ICS/Critical Infrastructure/SCADA Security
ICS/Critical Infrastructure/SCADA/OT systems share common vulnerabilities and common threats. Here is a top 10 list of common threats to ICS/Critical Infrastructure/SCADA/OT systems.

Legacy Software Leverage
Outdated programs enable uncontrolled access, lacking authentication and data integrity.

Command Intrusion
Unchecked data permits arbitrary commands, risking manipulation of OT systems.

DDoS Disruptions
Limited access-controls enable DDoS attacks, sabotaging vulnerable unpatched systems.

Default Dangers
Insecure defaults and simple passwords make OT systems easily compromised.

Remote Risks
Unaudited dial-up connections provide attackers backdoor access to SCADA systems.

Policy Pitfalls
Mismatched IT and OT security approaches create vulnerabilities; unified policies are essential.

Security Shield Shortcomings
OT systems need anti-malware, host-based firewalls and patch management for protection.

Flat Network Flaws
Misconfigured networks allow attackers easy access to Internet-connected OT systems.

Web-Accessible Weakness
Increased web access to traditional OT systems invites cross-site scripting and SQL attacks.

Encryption Exclusion
Legacy SCADA controllers lack encryption, exposing credentials to sniffing attacks.
Making things worse, the sector is an attractive target due to its growing size, yet security teams remain understaffed and under-resourced. As these high-value networks are ever more vulnerable to attack, it is vital to find new security solutions. The adversary-generated threat intel and threat detection that deception technologies provide can address these challenges to OT networks. With deception, it is possible to detect malicious activity, collect valuable threat intel and also create and respond to adversary activity in real time.

Find out how to protect ICS/OT systems today.
A Solution to the Challenges of OT/ICS/Critical Infrastructure/SCADA Security
What if there were a solution you could deploy in minutes without interrupting your existing architecture? Only by adopting an adversary-centric approach can security professionals truly defend against sophisticated and novel threats targeting OT/CPS. Deception technology provides actionable intelligence in real time, with zero false positives, connected to your existing systems to allow automated remediation. It can be deployed across any network, on premise, in the cloud, across air-gapped networks and at speed.
Even if your OT organization already has a network monitoring solution like Dragos, Nozomi, or Claroty, there is still a need for CounterCraft, thanks to the following capabilities:
30-day (or less) deployment
CounterCraft’s speed of deployment is 30 days—on cloud, on premise, hybrid or air gapped. Comparable solutions can take 12 months to deploy, and even in that time only reaching 80% of your network, leaving the typically valuable systems in the remaining 20% vulnerable.
Hardware agnostic and non-intrusive
Our solution is not hardware dependent, unlike other vendors that use physical appliances resulting in a more intrusive, less flexible and scalable approach. They also require full access to the production network environment, creating a more noisy solution with a higher number of false positives.
Protects production assets
Our technology creates an external environment that provides a containment area for attackers, safe from production assets.
Endless integrations
Our software complements your existing OT network monitoring solution. Our software integrates with just about everyone, including your SIEM, SOAR, XDR, EDR, NDR.
With CounterCraft, there is:
- No need to modify the existing ICS/OT network.
- No need to insert additional inline devices.
- Quick and safe OT adversary campaign deployment.
To Learn more about how CounterCraft’s adversary-generated threat intelligence is uniquely positioned to protect OT networks, download the full data sheet here.
For more examples of how deception has prevented cyber attacks and to Learn more about CounterCraft, contact us.
Adversary-generated Threat Detection Powered by Deception
CounterCraft provides actionable threat intelligence in real time using deception technology. Unlike comparable technology, which takes up to 270 days to provide threat intelligence that requires an analyst to determine if it’s relevant or not, CounterCraft delivers intelligence generated by your adversaries, in real time, that enables you to implement remediation immediately. Active defense allows organizations to identify unknown risks and threats tailored to their external and internal attack surface and delivers detailed telemetry.
