Imagine a threat actor that has legitimate credentials to make their way to their objectives, inside knowledge of network architecture, and plenty of time to ponder over what next action is to be taken. This scenario, a threat actor that is already in the network and not easily identifiable by patterns, baselines or known behavior, is a security team’s worst nightmare. This is the insider threat.
Insiders are undoubtedly one of the most concerning threat actors when it comes to establishing a solid cybersecurity posture. An insider with trusted access can have high impact with a relatively low execution cost, meaning they can affect organizations of all sizes and industries.

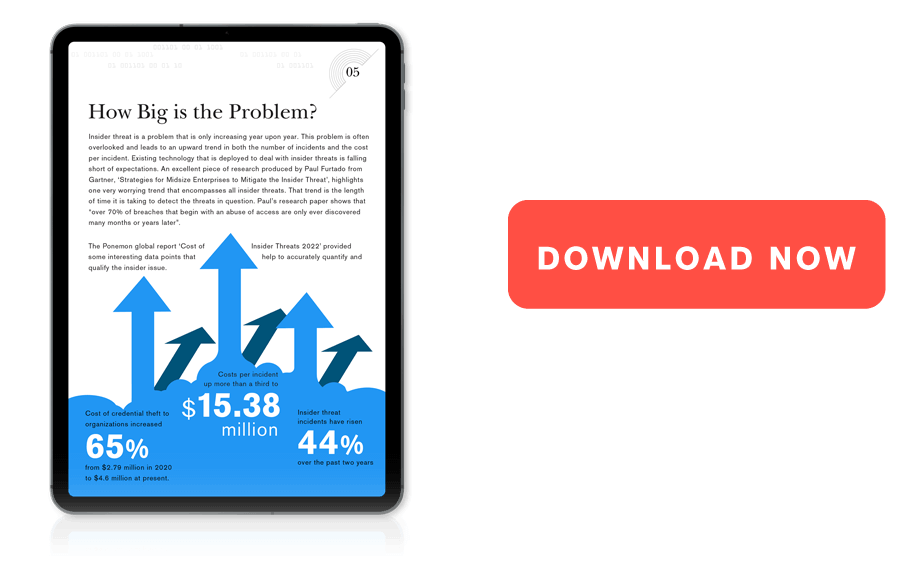
Insider threats can hang out in your network for months undetected, with the cost for mitigation rising exponentially. In fact, on average, incidents that take more than 90 days to contain cost organizations an average of $17.2 million on an annualized basis.
What if you could provide high-confidence alerts to adversarial presence within your network?
In this ebook, you will find a comprehensive look at insider threat. We will start by looking at examples and indicators of insider threat. Then, we will take a closer look at how to best detect and mitigate this important risk.
Cyber deception is especially apt at detecting threatening behavior without relying on known malicious patterns, signatures, baselines or other big data. In fact, deception is virtually the only way to detect insider threat behavior when the attack comes from within a network via someone with access credentials. Deception is agnostic as to threat types; it lures the insider into the deception environment. This is done by socially engineering the insider by crafting lures that will appeal to them. The end user has high fidelity alerts that will detect that they have a potential insider with malicious intent within their network within seconds of an artifact being touched.
We’ve created a free deep dive into this fascinating subject. Our free e-book Cyber Deception for Insider Threats features nearly twenty pages of information containing everything you need to know about insider threat.
CounterCraft-ebook-insider-threat.pdf
Take on insider threat, one of the most difficult cyber threats to detect, and turn the tables on the attacker. Gather information on what an insider wants before they achieve their objectives and stop them in real time.
Find out how cyber deception can help with insider threat, allowing you to collect intel from attackers in real time and actively defend your organization from current and future attacks.
What’s inside?
What’s inside the e-book?
- 17 pages about how to identify, detect, and stop insider threat
- A list of types of insider threat
- A list of common indicators of insider threat
- An example of an insider threat deception campaign
- A case study
- Contact information to get an in-person assessment if you desire
Want to keep your company safe from internal attacks?
Make malicious actors within your network work harder. Using deception techniques, you can create deception environments that will contain adversaries and collect threat intel to protect your network. The information provided by a deception campaign for insider threat is delivered in real time, composed of contextual and relevant IoCs, and cannot be sourced from anywhere else.
Find out more and download the e-book Cyber Deception for Insider Threats today.
Curious about deception technology? Learn more about cyber deception at Cyber Deception 101, the primer we’ve written on the subject.





