The world of deception technology is still evolving, as is to be expected in a developing sector. Today, CounterCraft presents what we believe to be a watershed moment in its evolution: the introduction of our new technology, ActiveBehavior™. This technology breathes convincing life into deception environments, automating a job that was previously manual and very costly—and it is fully integrated into our Cyber Deception Platform as a deception service. Read on as our Product Manager, Rich Barrell, explains this new technology.

The Ghost in the Machine
A couple of weeks ago, I was doing some deployment work for a client on a Windows host that had our new ActiveBehavior technology activated. I didn’t realise that it was on, and when suddenly a browser opened and “another user” started to download a file, it was a real shock! I immediately got on the phone to check that no one else was logged in. Imagine how real this makes the deception environment feel -and how a real adversary would react. Any doubts of this being just a honeypot will be immediately dispelled!
The exciting new ActiveBehavior feature for the Countercraft Cyber Deception Platform is the first step in a new suite of features that take credibility for deception environments to a new level.
Read on to find out how it came about—and how it works.

The Problem / Deserted Deception Environments
In order to understand why this is so important, let’s go back to December 1872. Adrift and deserted in the Atlantic, the ship Mary Celeste was discovered with no sign of crew. She was completely empty but there was no sign of disaster. Even the crew’s belongings were largely intact. Since then, the name Mary Celeste has become synonymous with being empty or deserted.

This is just like a honeypot deployment. Unless you make a huge effort to keep things fresh, a honeypot becomes like the Mary Celeste in short order—Stale, just an empty server, with no logs, history or signs of life. This is a big giveaway to any adversary who interacts with the honeypot, which means keeping things fresh is essential to maintain credibility within a deception deployment.

The Solution / Activity and History with Active Behavior
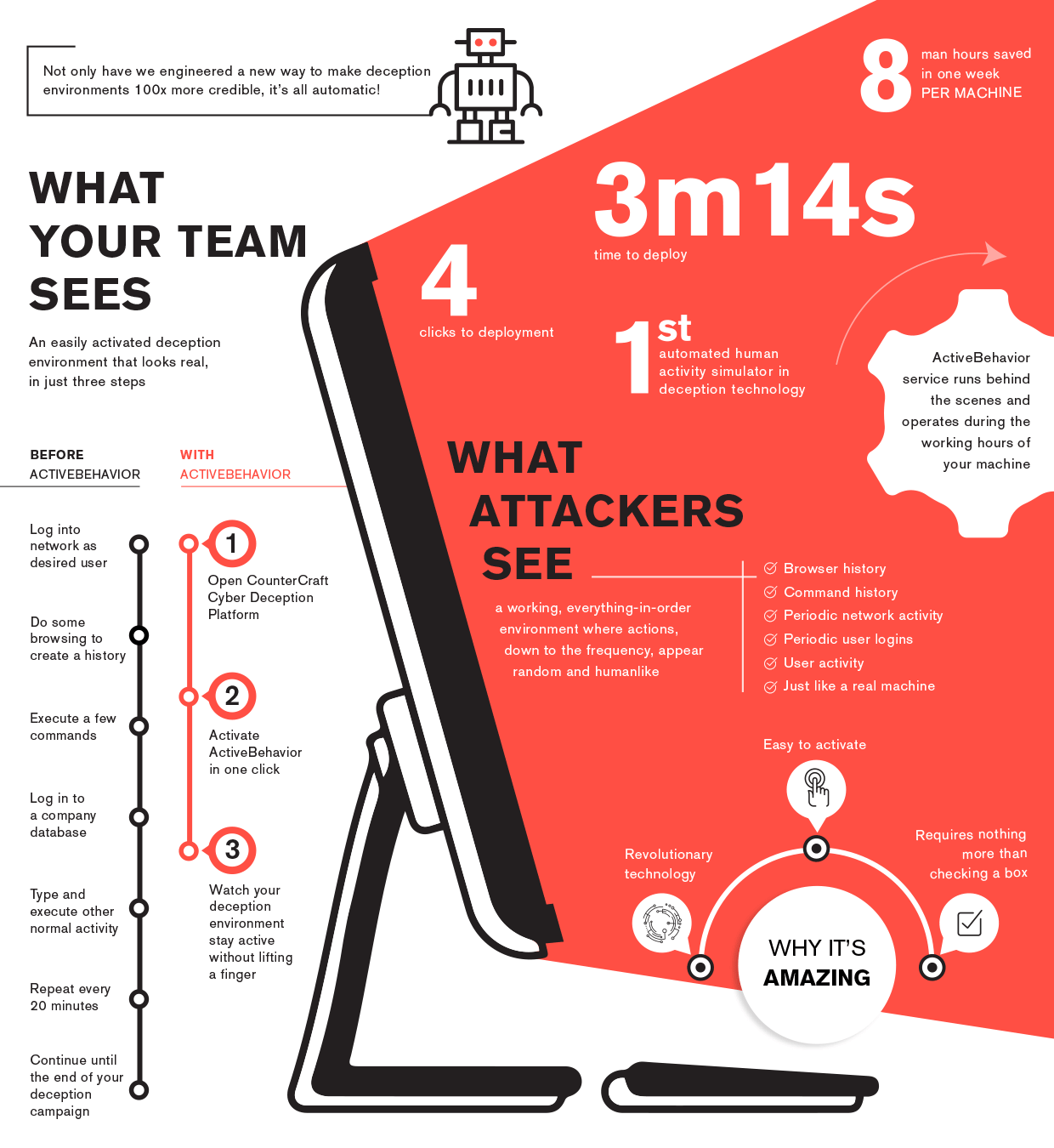
This is where ActiveBehavior comes in. Up until now, the only practical way to keep things fresh was to have someone log in to the honeypot to make some noise and generate logs. Now, we have ActiveBehavior that does the same thing, automatically, removing the need for all that effort!
ActiveBehavior – or, the “Human Interaction Simulator” as it was known in development – is a tool that totally automates this process of logging in and performing “typical” user activities, or basic SysAdmin tasks.
Download our data sheet for more information on this new ActiveBehavior technology.

The Integration / How We Integrated ActiveBehavior into the CounterCraft Platform
ActiveBehavior has been integrated into the Cyber Deception Platform as a deception service. Deployment of this service is simplicity itself, as it only takes four mouse clicks to activate the service on the target deception host.
Just like any other deception service, you click on the “add service” button, select the ActiveBehavior option from the drop down menu, add the user credentials for the target host, save and activate. Simple. The credentials you use can be the same fake credentials you used as a breadcrumb, as long as you’ve set up the user on the host.
Once the service has been activated, the ActiveBehavior engine triggers random “user” activity during a predefined working time. The timing of activity is unpredictable, and mimics real user behaviour, and depends on the OS of the deception host as to the type of activity that is generated. As an additional plus, the activity generated by the ActiveBehavior engine is automatically filtered, so there’s no risk of potential false positives.

The Future / The Road Map
We’ve mentioned that this is just the tip of the iceberg, so what for the future? This current iteration of the ActiveBehavior technology is just the beginning. For version 2.9.0 to be released at the end of Q2 this year, we will be including different user profiles, from a standard desktop user to a full SysAdmin to mimic behaviour patterns of different user types.
The goal is to make it look like the user has stepped away for a coffee. At the moment the user activity is defined by a series of predefined configurations. The goal is to make this fully customizable from the CounterCraft Cyber Deception Platform console, to allow users to set up custom schedules and behaviour patterns to more closely mimic their typical usage – getting ever closer to the goal!

Next Steps / Visit Our Resource Center and Get In Touch
To find out more about ActiveBehavior or about deception in general, please have a look at our resource center to get more info or get in touch, directly. You can download our data sheet on ActiveBehavior here for more detail on how this technology works. We are only too happy to explain what we do and how we can help you get the best out of deploying deception – from an initial conversation or simple demo, to a fully featured deployment.