Gartner has released its Hype Cycle for Security Operations 2020 report. It is a thought-provoking read, spanning a diverse range of technologies. What I want to focus on here is the report’s approach to deception, where it stands in the hype cycle and how the level of maturity in your security operations may not be relevant to the central question: am I ready for deception?
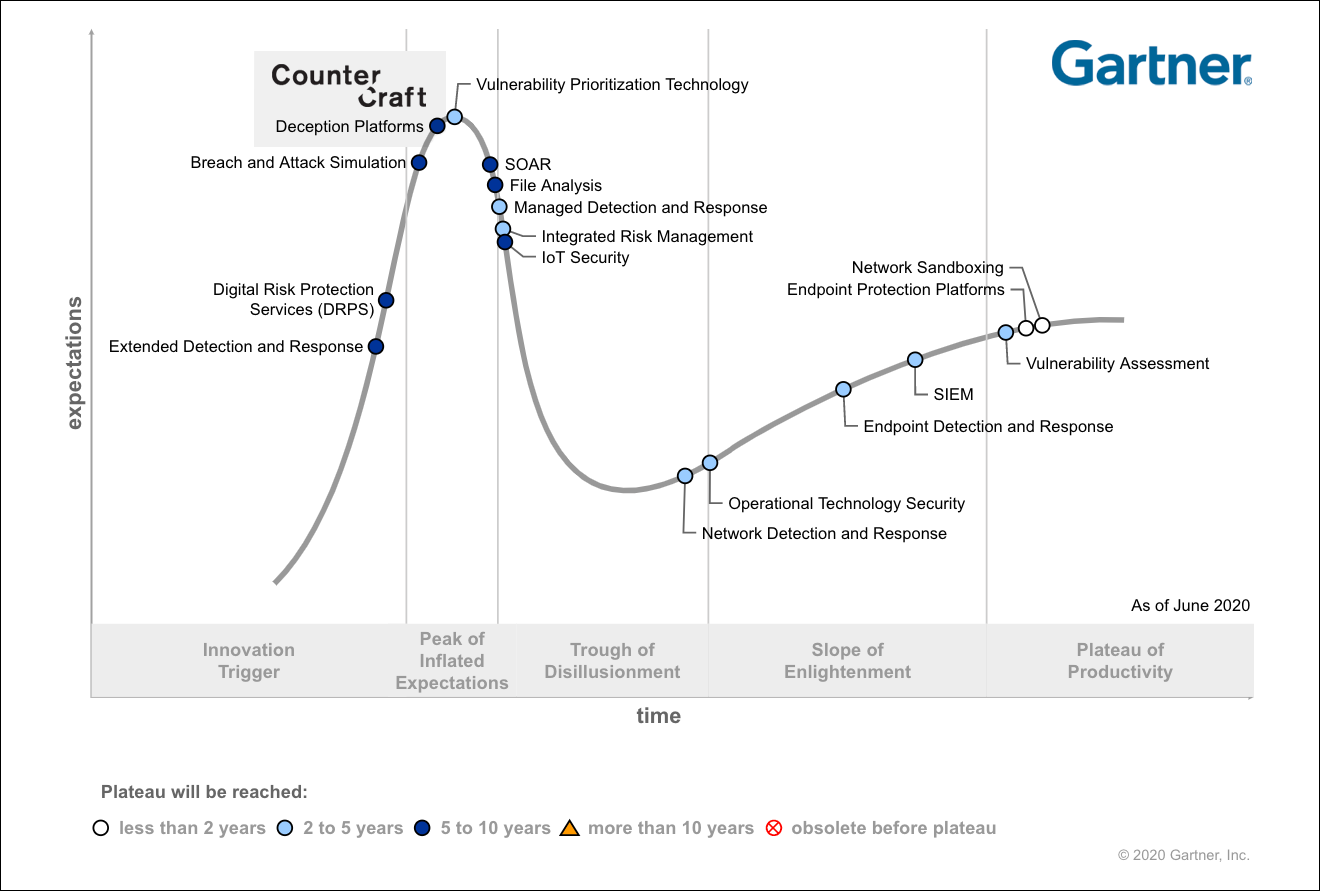
Let us begin by taking a look at where deception is in the hype cycle.

Security Leaders
It will prove to be an impossible task for any leadership team to be confident that their current security control set allows them to be prepared for every eventuality. More importantly, leadership teams need to try and deliver cyber resilience and keep systems operational. Therefore, being able to detect threats on its own may not be enough. Detection and prevention need to be fused together in order to deliver operational resilience. The key here is not to spend the security budget entirely on detection but to think about being able to detect attack vectors well before they get anywhere near your networks. This is referenced in the Gartner report as “intelligent business-driven decisions”. The challenge for security leaders is how to get to the point whereby they are empowered to make those types of decisions. To empower yourself to make the right decision you need the correct data points.

Data Points
For data points to empower your decision making, they need to possess a number of key characteristics. The data points must be contextualised, relevant, timely and have a very low operational overhead to generate and process. So, what kind of security tool is able to produce these types of data sets? Deception technology can do so in an automated manner, delivering the right data at the right time, thus empowering decision making that is business-centric and intelligent. Most importantly, you do not have to wait to detect the attackers once they are inside your network and impacting your operational processes. Having the ability to deploy deception campaigns beyond your network perimeter (including cloud or a hybrid infrastructure) empowers you to get ahead of your adversaries. Understanding what tactics, techniques and procedures are being used against your organisation (TTPs) will enable a preventative posture to be adopted by leadership teams. Collect the correct data sets on attackers that enable you to detect them whilst they are trying to breach your network and not after the event. Data that empowers intelligent business-driven decisions.

Maturity
Reading all of this you may be wondering that it all sounds like the kind of activity that the very large global organisations would be undertaking because they have the resources that allow them to think about and execute intelligent business-driven security operations. Think again! In the Hype Cycle Report it is made clear that organisations of all security maturity should be examining the value that deception can bring them — allowing them to fuse prevention and detection into a fully strategic security operations model. Let us take a look at each maturity level and define the key strategic benefits of deception technology.

Low-Maturity Organisations
Low maturity organisations in the report are those that are defined as not being capable of managing solutions such as SIEMS due to a lack of resources. These type of organisations would benefit enormously from deception technology. The CounterCraft Cyber Deception Platform not only scales seamlessly but the scarcity of false positives and high fidelity of alerts powerfully remediates the pain points commonly suffered by such organisations. But it does much more than remediate paint points; it enables powerful new functionalities such as the ability to generate threat intelligence that is specific to such organisations and fully correlated and contextualised. Pivot away from simple detection and into prevention and actionable intelligence.

Medium-Maturity Organisations
These are defined as organisations that may already have SIEM and EDR-type technologies. We know that the cost in terms of time and resources can make leveraging such technology to deliver preventive security very difficult. EDR is also up against a number of different techniques that can circumvent it, such as process hollowing. So, in order to mitigate these pain points, deception technologies can provide a different means of detecting the attackers. How? By forcing the attackers to be right all of the time instead of those that are defending the network. Would you not rather turn the probability of detecting an attacker in your favour by forcing them into impossible choices? The CounterCraft solution will allow you to pivot away from detection into prevention by allowing you to deploy campaigns that enable you to map and correlate attackers well before they get anywhere near your network. Fusing together detection and prevention into a single platform allows you to develop a defence in-depth strategy that is coherent and forward thinking.

High-Maturity Organizations
High-maturity organisations, according to the report, may want to use deception technology in a number of different situations, such as in operational environments (SCADA, OT), where traditional security tool sets are not a viable option. In addition to this, the report states that deception technology has the ability to generate local threat intelligence. I would like to expand on this and suggest that mature security organisations use deception technology to actively collect data points on different types of threat vectors and actors that are looking to target them. Rather than wait for attackers to get inside your network, map adversary behaviour to draw out not only TTPs but also the strategic objectives of the threat actors. Understanding both data sets allows an organisation to understand if currently deployed security controls would be effective against attackers with these particular strategic objectives in mind. With the CounterCraft Cyber Deception Platform, multiple campaigns can be created and automated, allowing an organisation to create intelligence-led deception campaigns that allow an organisation to gather the intelligence they need to empower themselves and to make “intelligent business-driven decisions”.
The question is not if you are mature enough for deception, but: if you want to make “intelligent business-driven decisions”. If the answer is yes, then leverage the power of cyber deception to empower your organisation. Intelligence-led decisions will not only create a more cohesive security strategy, but it will drive down risk and the costs associated with those risks if they were ever to materialize.

Author: Nahim Fazal, Head of Cyber Threat Intelligence





