On May 24, the United States National Security Agency (NSA) issued a Cybersecurity Advisory on a recently discovered use of Living Off the Land Binaries (LOLBins) techniques to evade detection by EDR, XDR and SIEM solutions. A Chinese hacker group known as Volt Typhoon attacked US critical infrastructure using Living off the Land (LotL) techniques (and was discovered by the Microsoft Threat Intel team). Volt Typhoon has been active since mid-2021 and has targeted critical infrastructure organizations in both the continental United States and Guam across multiple verticals (communications, manufacturing, utility, transportation, construction, maritime, government, information technology, and education).
Take our quiz today to find out how deception technology can work for your organization >
These LotL attacks pose a huge security challenge, as they utilize common system administration tools that are often part of operating system builds. The normal, benign, use of these tools drowns out any malicious activity. If defenders alert on use of these tools they would be swamped in false positives. Defenders have a tough task, to be able to detect malicious usage they have to know exactly what bad use of those tools looks like, down to the level of all the argument strings used on the command line and the relevant timing of the tool use with other activities on the system. When the have this specific information they can filter for just the malicious usage. But, how do they gather this intel, in real time, whether before, or while attacks are underway? CounterCraft can help. Our technology does this automatically—and we ran a test this week to prove it.
The NSA’s Cybersecurity Advisory, released May 24, 2023
The CSA advisory explains:
“One of the actor’s primary tactics, techniques, and procedures (TTPs) is living off the land, which uses built-in network administration tools to perform their objectives. This TTP allows the actor to evade detection by blending in with normal Windows system and network activities, avoid endpoint detection and response (EDR) products that would alert on the introduction of third-party applications to the host, and limit the amount of activity that is captured in default logging configurations”.1
This is not to say that EDR and SIEM don’t do their job. They collect tons of in-depth telemetry from endpoints. However, this very selling point can also become a problem, because this glut of data becomes a “security data lake of telemetry”. Besides, living off the land attacks rely on using legitimate tools and features that are already present on the system. These tools are often trusted and widely used, making it difficult for EDR solutions to distinguish between legitimate and malicious usage. So despite having and evaluating the telemetry, they do not alert on it. So it’s normal for EDRs to struggle to detect LOLBins attacks. The threat actors are just doing regular things, executing system commands or using binaries and processes that already run on the system. The challenge is knowing that the intent of the command is malicious.
Detecting living off the land attacks
So how do organizations predict and, more importantly, detect LotL attacks? At CounterCraft we are passionate about deception techniques as the solution.
A deception environment is very good at detecting malicious behavior. This is where deception has a significant advantage over EDR/SIEM: it immediately investigates any activity on decoy machines and quickly analyzes it for malicious intent. In a matter of 20 seconds, CounterCraft’s deception technology informs the EDR / XDR / SIEM system that this process call and arguments set is a live attack and evidence of malicious behavior. As an added benefit, the EDR / XDR / SIEM system now knows what “bad” looks like. This means they can search across the entire security data lake and instantly detect similar activity across the organization’s network.
CounterCraft ran the Volt Typhoon command on a decoy network to see if CounterCraft The PlatformTM would be able to detect the LOLBins attacks described in the CSA.
This was the result:
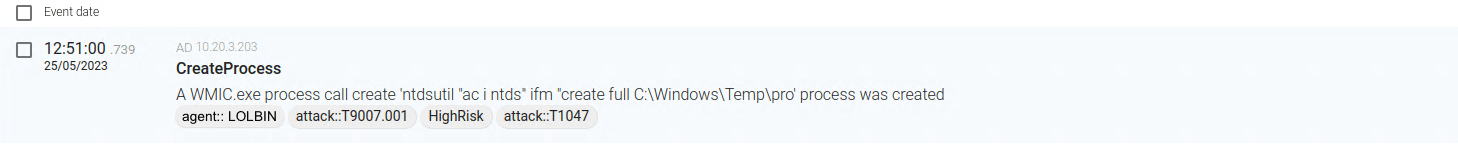
This image from our platform shows the telemetry returned on this staged attack. You can see the “attacker’s” (in this case, our) executed command, and just below you can see the type of attack, the mapping to MITRE, and the HighRisk alert designation—game-changing information for your security team.
Takeaways for defenders : information to action
CounterCraft was not only able to detect the Volt Typhoon LOLBins attacks described in the advisory, but also notified SOC teams with a high-fidelity alert in less than 30 seconds, a boon for situational awareness and proactive threat hunting.
This then enables the SOC team to use their SIEM/XDR/EDR to compare historical telemetry against the argument string to see if this behavior has already occurred before in different parts of the network. If it hasn’t, the SOC team has gained knowledge over an unknown vulnerability and has time to proactively defend by reconfiguring current security controls. If they have already been infected by this attack, not only have they been alerted of an active breach, they now have all the information they need to start the remediation processes.
The immediate, detailed information provided by The Platform makes it simple and quick to detect novel attacks and gives organizations the real-time intelligence they need to remediate immediately. Want to try it for yourself? Get in touch today.

Dan Brett is the Chief Product Officer and co-founder of CounterCraft. Highly accomplished in achieving outstanding growth for B2B startups, he contributes a great depth of cybersecurity knowledge and understanding of consumer behavior. Follow him on LinkedIn.
1https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-144a
Adversary-generated Threat Detection Powered by Deception
CounterCraft provides actionable threat intelligence in real time using deception technology. Unlike comparable technology, which takes up to 270 days to provide threat intelligence that requires an analyst to determine if it’s relevant or not, CounterCraft delivers intelligence generated by your adversaries, in real time, that enables you to implement remediation immediately. Active defense allows organizations to identify unknown risks and threats tailored to their external and internal attack surface and delivers detailed telemetry.





