Cyber deception is the most effective way to identify threat actors in any organization’s network. Read on for insight into how it works to deliver actionable threat intelligence across industries.
Highlights.
-
Categories: Product Features
Come take a look inside CounterCraft’s Cyber Deception Platform with our Product Manager, Rich Barrell. From the standardization of EQL to broader coverage for all licenses, the latest version of CounterCraft is full of ease of use improvements. Read more
-
Categories: Product Features
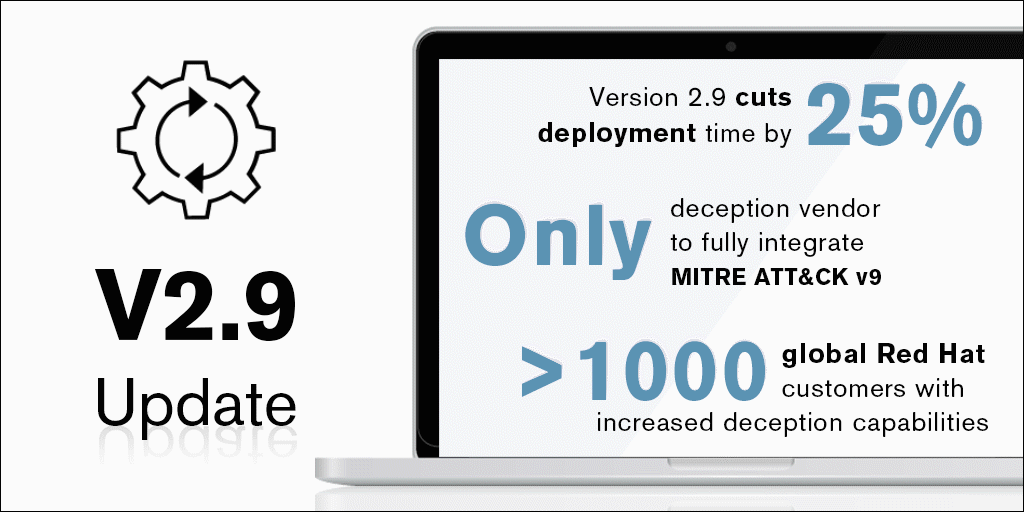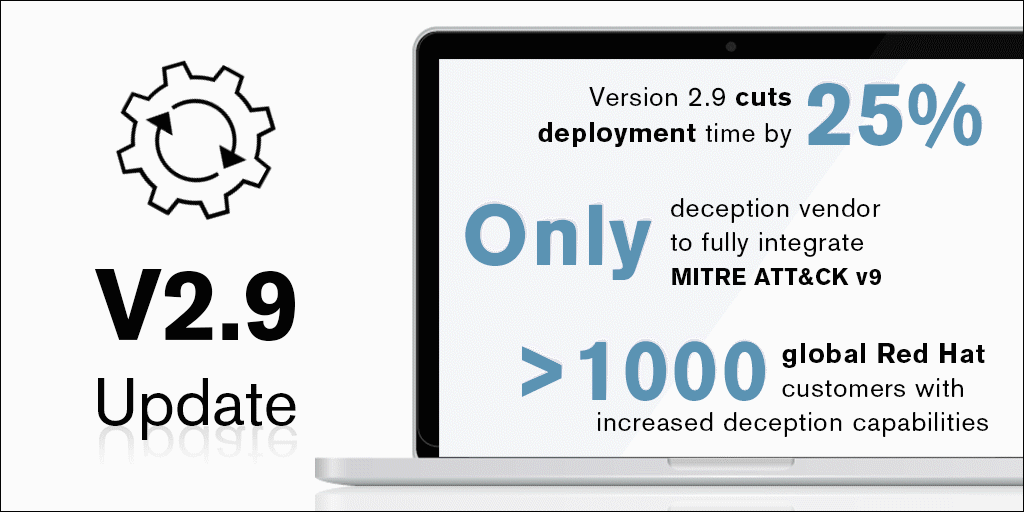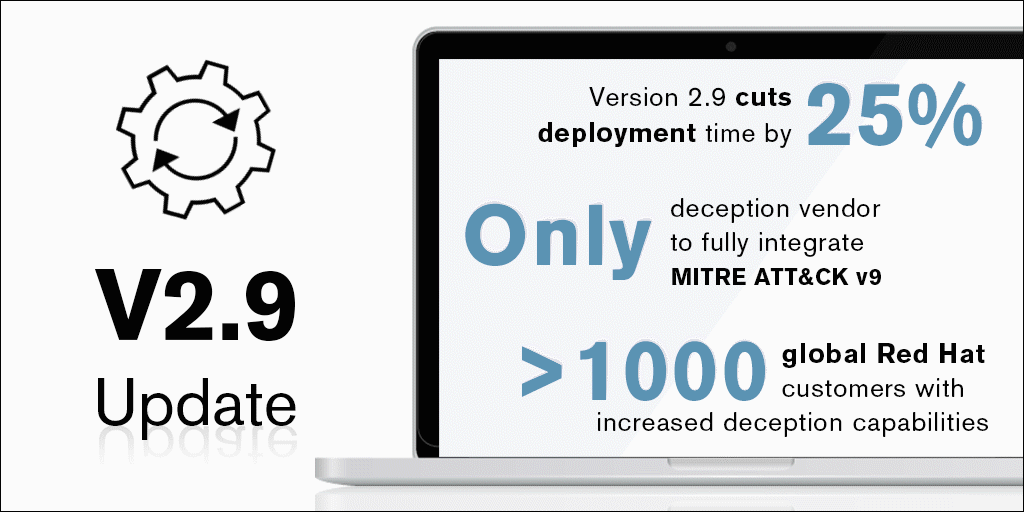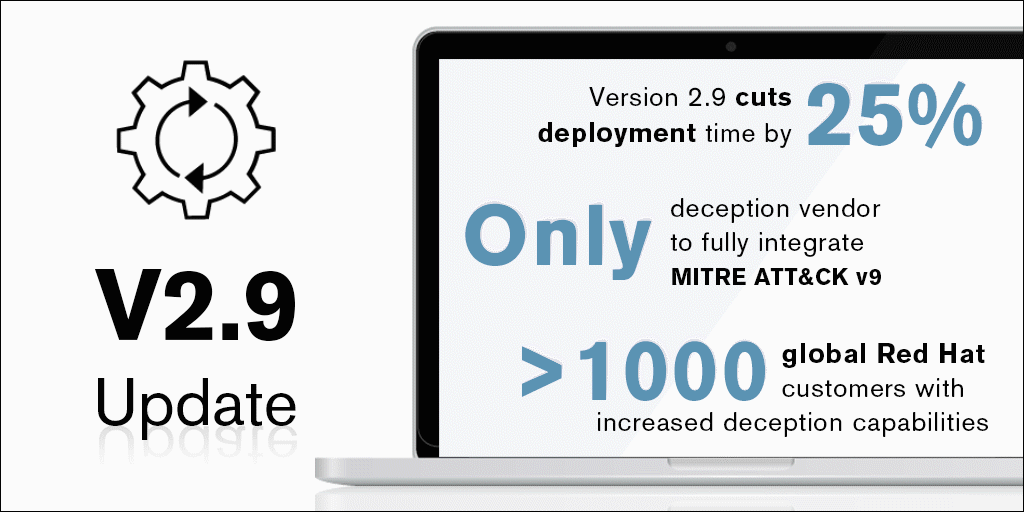
CounterCraft’s latest release features a bundle of improvements made with our clients in mind. Version 2.9 is all about refining different aspects of our platform to make them easier to deploy and more user friendly, from further integration EQL to new solutions specific to specialized sectors. Read more
-
Categories: Company News
Meet the team behind CounterCraft’s award-winning deception-powered threat intelligence cyber platform. Today, meet Xabier Eizmendi, our Senior Architect. Read more
-
Harnessing big data can be a powerful tool. But right data can help you identify threat actor behavior much more quickly. Read on to find out. Read more

-
Categories: Product Features
Threat Deception in a Minute highlights just how simple it is to get powerful deception technology set up in your network. Whether you’re a current customer or wondering what it’s like to utilize deception, you’ll find these videos quick, interesting and helpful. Read more
-
How can organizations implement a defend forward cybersecurity posture? And why is it a good idea? Read this post by Luke Wilson to find out. Read more