Cyber deception is the most effective way to identify threat actors in any organization’s network. Read on for insight into how it works to deliver actionable threat intelligence across industries.
Highlights.
-
Categories: Company News
Black Hat is back! Read about what to see at the 2021 Black Hat Conference here. Read more

-
CounterCraft goes to great lengths to make sure our platform is the most secure in the industry. Read on to find out what we do to make sure our platform is a safe base for your deception-powered threat intelligence. Read more

-
Categories: Product Features
CounterCraft integrates with all your favorite security software, as well as the communication tools your team uses. Learn about our integration with Splunk. Read more

-
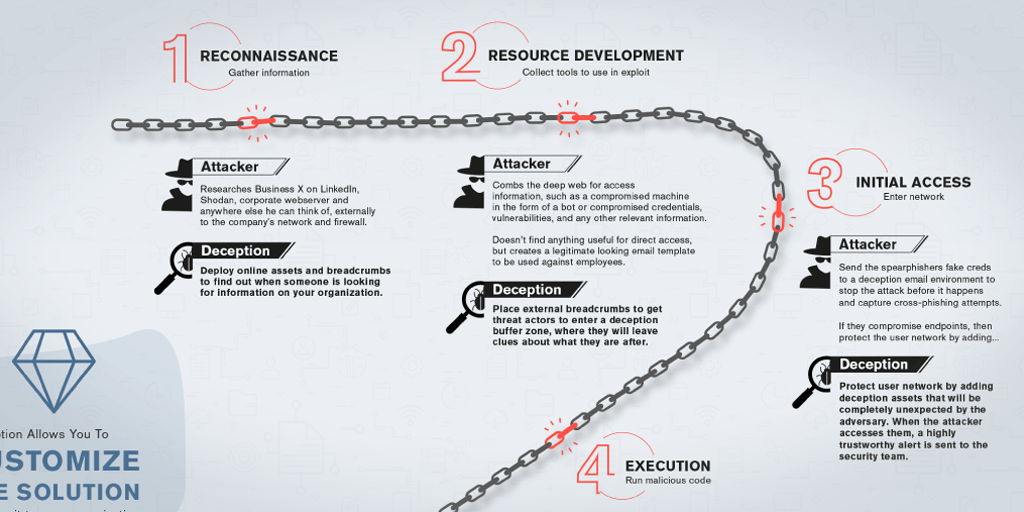
This infographic breaks down the stages of a typical cybersecurity incident and shows you how to stop it. Read more
-
Categories: Deception Technology
Cybersecurity news in April. Click through to find out what our team of experts was reading and talking about this month. Read more

-
Every cyber attack consists of various stages, from pre breach to the moment of impact. We believe every stage is an opportunity to trip up and trap cyber criminals. Keep reading to get a breakdown of the stages of a typical cybersecurity incident.100 character intro: An infographic that shows how a typical cybersecurity incident unfolds. Read more