Cyber deception is the most effective way to identify threat actors in any organization’s network. Read on for insight into how it works to deliver actionable threat intelligence across industries.
Highlights.
-
Categories: Product Features
Deception tech enables you to be one step ahead of attackers. It’s a much more proactive approach to security strategy. Read more

-
Our VP of Sales comments that he’s never before seen such rapid adoption of an emerging technology and tells us why deception is a lucrative opportunity for MSSPs and service providers. Read more

-
Categories: Company News
The most effective deception technology immerses the attacker in a credible and complex environment in order to deliver increased clarity for the user. Read more
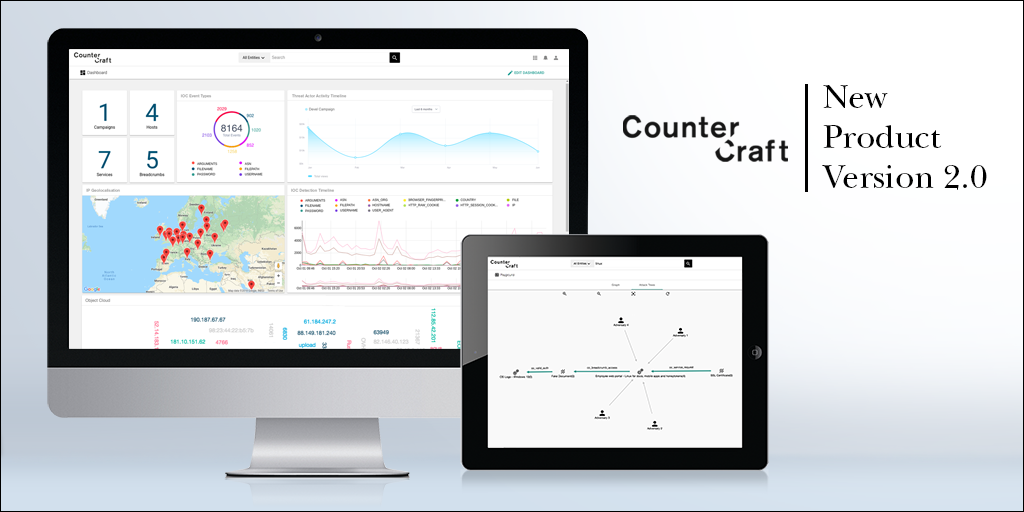
-
Cyber attacks are attributed to one criminal group based on some IOCs, the type of tools used by the attackers, or their modus operandi. The truth is that attribution is often difficult to determine. Read more

-
Categories: Company News
The CounterCraft Partner Program is an opportunity for Managed Security Service Providers (MSSPs), service providers and consultancies to offer enhanced protection to end customers with profitable new security services Read more
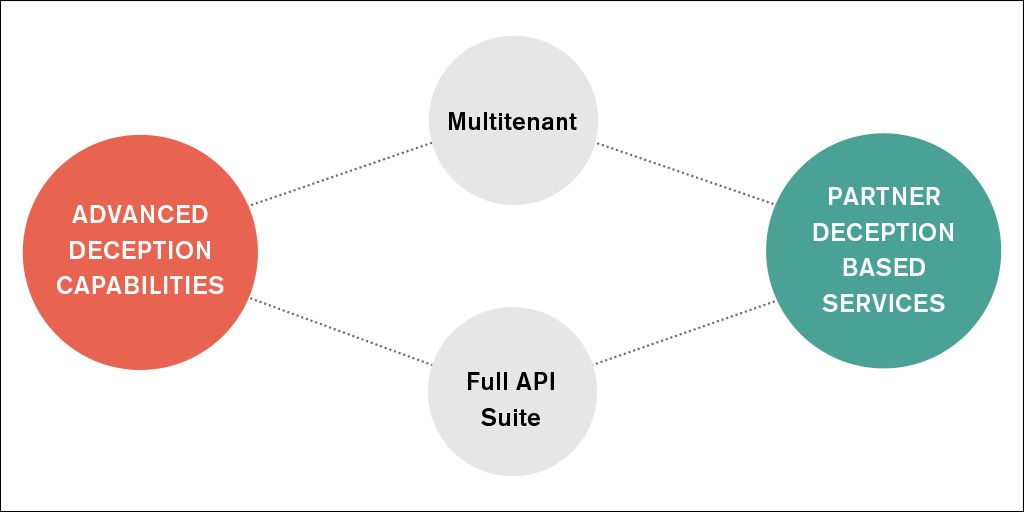
-
Categories: Company News
The CounterCraft team are preparing for a busy schedule, with attendance confirmed at a host of excitingevents to capture insights about latest trends in cybersecurity and showcase about cyber deception use cases. Read more


















