Cyber deception is the most effective way to identify threat actors in any organization’s network. Read on for insight into how it works to deliver actionable threat intelligence across industries.
Highlights.
-
This is the first of several blog posts in the Kubernetes as a Deception Platform series. In this series, you will learn about Kubernetes and why it matters to you from a cybersecurity point of view. Discover what Kubernetes is, why use it, if it is secure, if it can be exploited and a brief… Read more

-
The founders of CounterCraft talk about how this generation of Docker daemon worms are working. Watch the video Read more
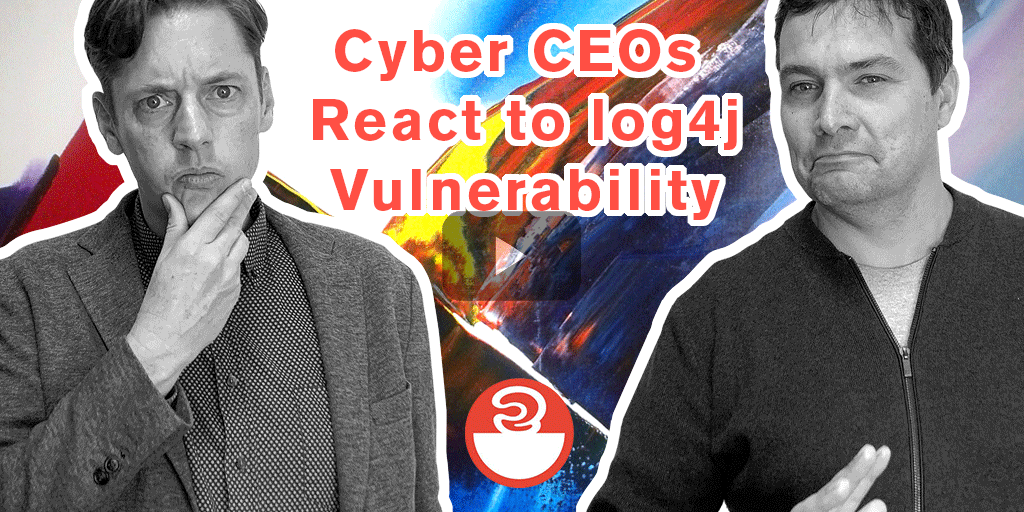
-
Categories: Deception Technology
Digital attacks are often faceless assaults that have a global impact and a huge economic toll. Even so, behind every attack is not some super computer, but a person. Cyber criminals are human, too. The human nature of attackers is a weakness to be exploited by defenders in the cybersecurity realm Read more
-
From highly technical posts with practical applications to in depth looks at deception technology, our blog featured all manner of articles written by experts in the field. Read on to get the best of what everyone was reading on our website in 2021 Read more

-
Categories: Threat Intelligence
We set up deception decoys across the Internet to gather threat intel. With these decoys, we succeeded in luring this threat actor, which could be the beginning of a new malware family. It is based on a botnet that attacks servers with vulnerabilities, and their main objective is to obtain a shell where they can… Read more

-
Are you wondering what solutions really provide your organization with a resilient and strong posture against the digital adversary? Read on to discover how the use of digital twin environments can help you clone your organizations operational infrastructure and behaviors to draw, deter, detect, document, and defend against cyberattacks within your organization. Read more


















