Cyber deception is the most effective way to identify threat actors in any organization’s network. CounterCraft delivers actionable threat intelligence across industries.
-
{Webinar} Destroying the Barrier to Sophisticated Detection and Response
Your security infrastructure is under attack. And your SOC team is drowning in alerts from the entire security stack. Something is broken—and that’s where advanced detection and response comes in. When your organization has real-time, adversary-generated threat intelligence, it makes it easy to cut through the fog of data and get a concrete idea of… Read more
-
{VIDEO} Detect and Mitigate Threats Faster with New Features
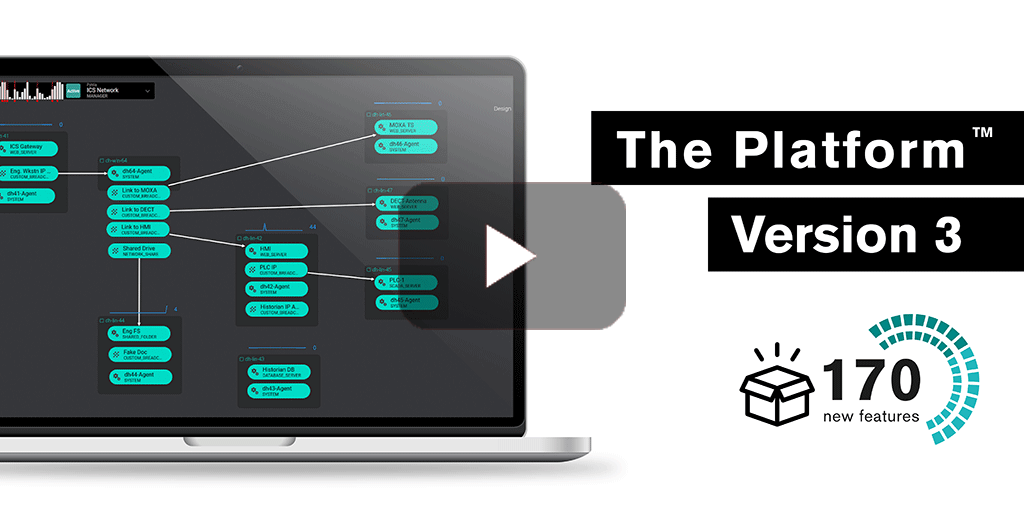
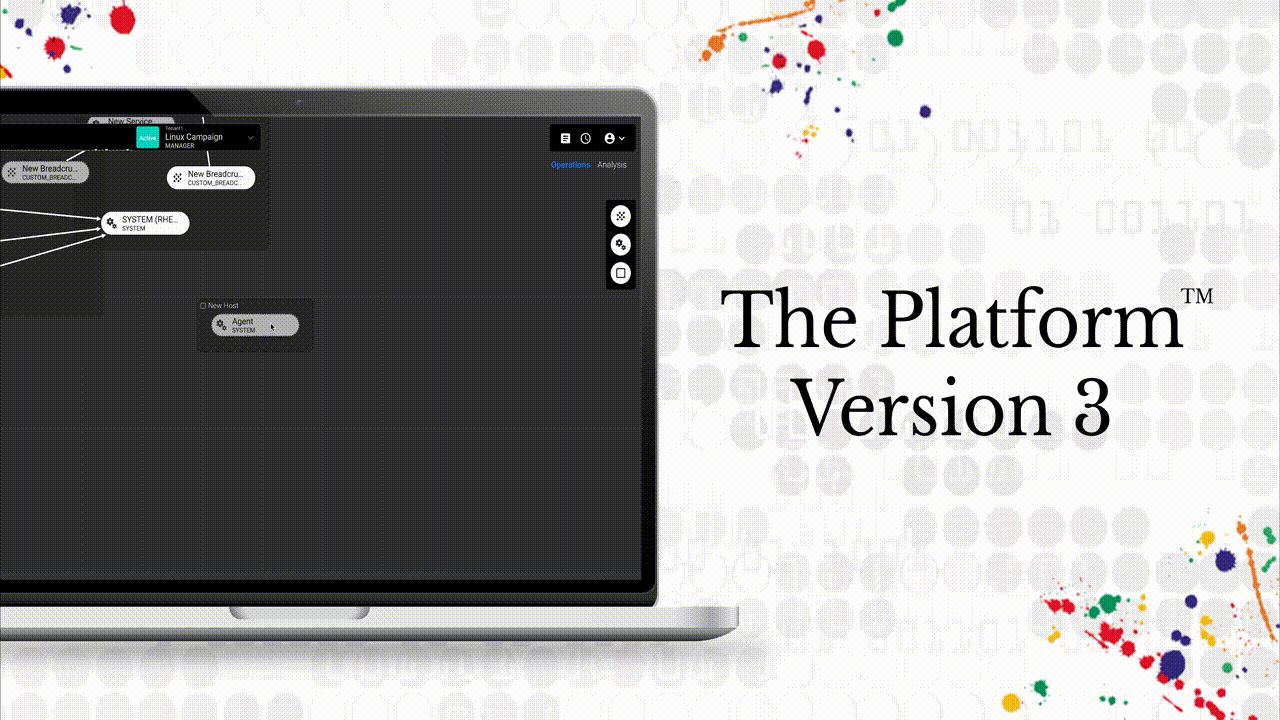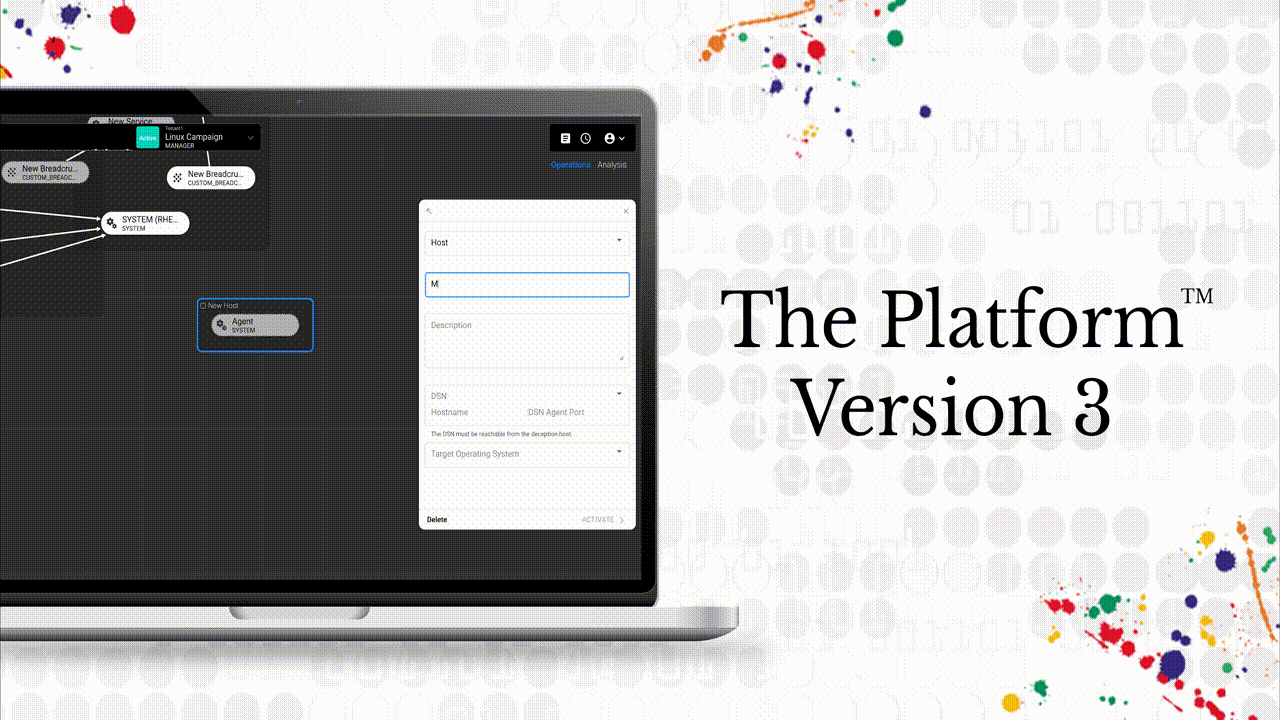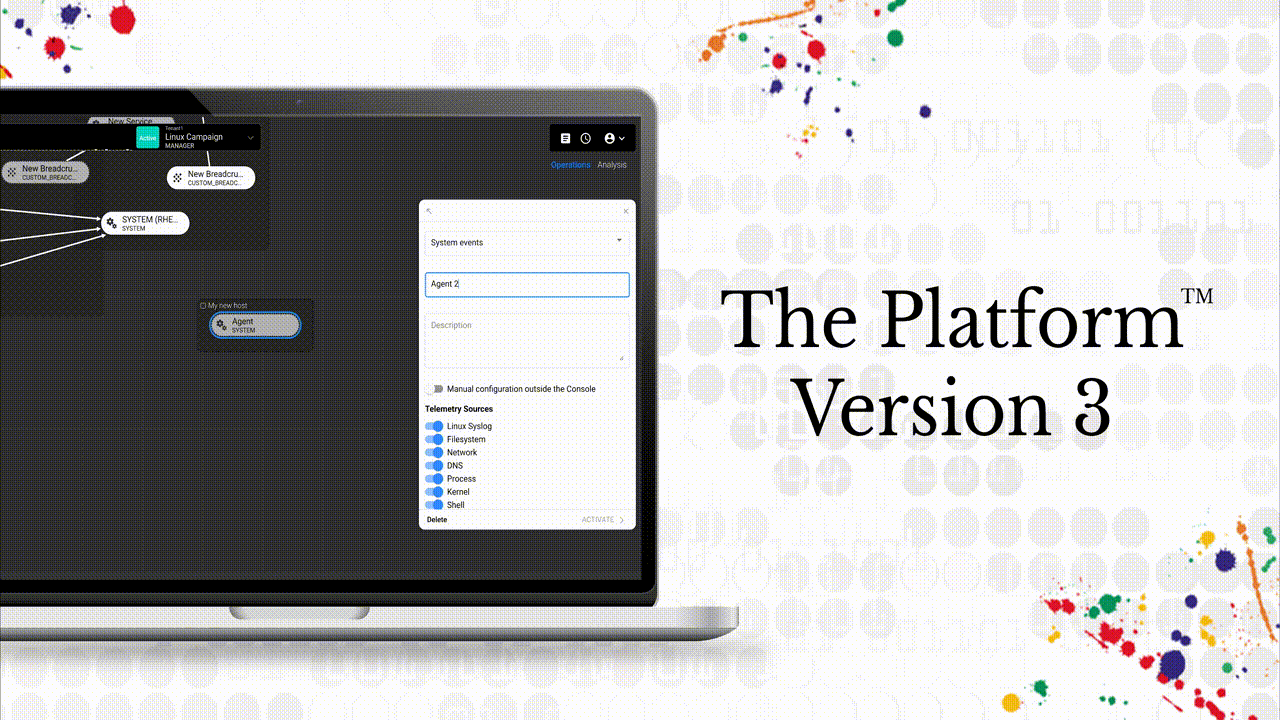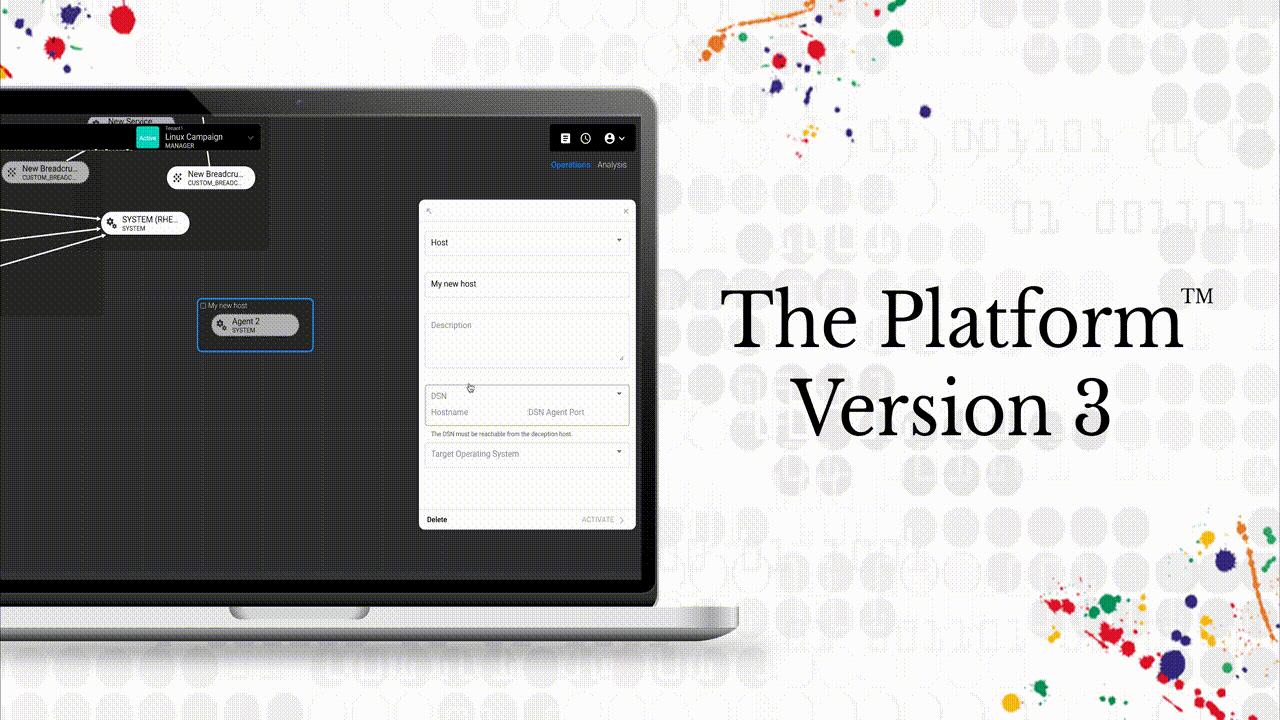
CounterCraft The Platform™ V3 revolutionizes the way security teams deploy and analyze deception campaigns, thanks to more than 170 new features focused on our customers’ needs and designed to actively defend their organization’s cybersecurity posture. Read more
-
The Platform v3: Now with Attack Trees to Implement Sophisticated Active Defense
CounterCraft The PlatformTM v3 revolutionizes the way security teams deploy and analyze deception campaigns, thanks to more than 170 new features focused on our customers’ needs and designed to actively defend their organization’s cybersecurity posture. Read more
-
Categories: Deception Technology
What We’re Reading
Cybersecurity news in January. Click through to find out what our team of experts was reading and talking about this month. Read more
-
Cybersecurity in Banking: Global Bank Uses CounterCraft to Detect Lateral Movement in a SWIFT Network
CounterCraft helps mitigate threats to cybersecurity in the banking industry. To learn more about how deception helped our client to detect and respond to attacks on their SWIFT network, download the full case study here Read more
-
Categories: Deception Technology
What We’re Reading
Cybersecurity news in December. Click through to find out what our team of experts was reading and talking about this month. Read more