Cyber deception is the most effective way to identify threat actors in any organization’s network. Read on for insight into how it works to deliver actionable threat intelligence across industries.
Highlights.
-
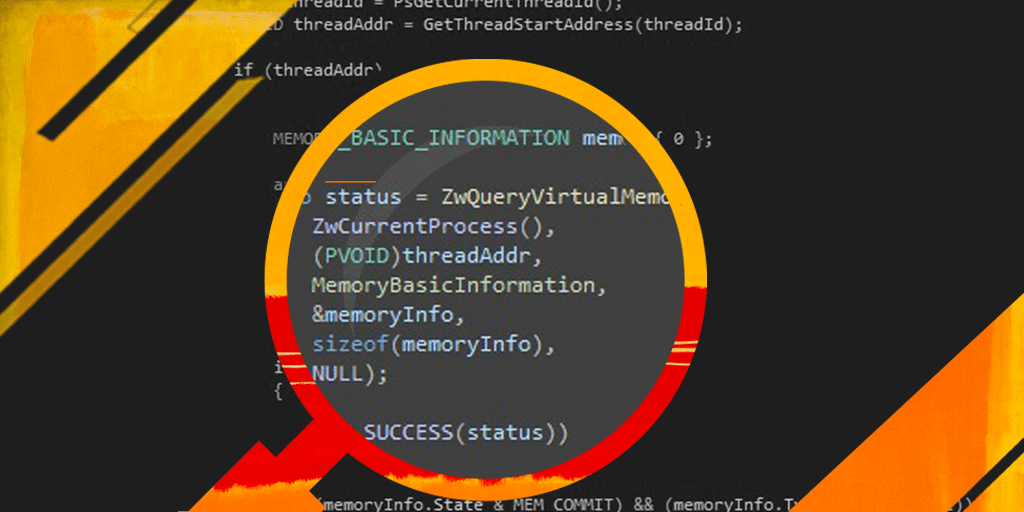
Post-exploitation tooling is becoming increasingly sophisticated and often evades detection by EDRs, meaning sometimes we will not be able to detect when an attacker is able to load his code into memory. Here’s a way to detect artifacts that are already loaded in memory from kernel and in real time Read more
-
Categories: Deception Technology
Cybersecurity news in December. Click through to find out what our team of experts was reading and talking about this month Read more
-
Categories: Company News
CounterCraft is counting down the days to MITRE ATT&CKcon 3.0, where our CEO David Barroso will be speaking at the conference. The conference, dedicated to the MITRE ATT&CK community, will take place on March 29 30, 2022, at the MITRE headquarters in McLean, Virginia. With a focus on how to make the most of ATT&CK,… Read more

-
Categories: Company News
Join us in celebrating Cyber Deception Day. You can tune in virtually to round tables and chats with MITRE and Kevin Fiscus Read more

-
Categories: Deception Technology
Threat Deception in a Minute highlights just how simple it is to get powerful deception technology set up in your network. This edition features how to set up a deception host. Whether you’re a current customer or wondering what it’s like to utilize deception, you’ll find these videos quick, interesting and helpful Read more
-
Categories: Company News
CounterCraft is counting down the days to MITRE ATT&CKcon 3.0, where our CEO David Barroso will be speaking at the conference. The conference, dedicated to the MITRE ATT&CK community, will take place on March 29 30, 2022, at the MITRE headquarters in McLean, Virginia. With a focus on how to make the most of ATT&CK,… Read more


















