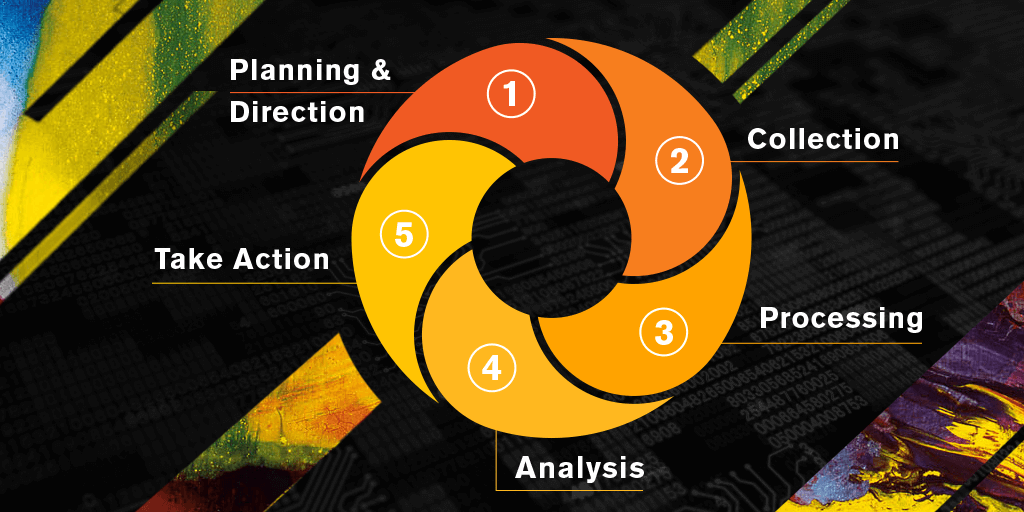
Cyber deception is the most effective way to identify threat actors in any organization’s network. Read on for insight into how it works to deliver actionable threat intelligence across industries.
Highlights.
-
Categories: Deception Technology
Cybersecurity news in March. Click through to find out what our team of experts was reading and talking about this month Read more

-
If you have been following our blog, you already know that we are big fans of the MITRE ATT&CK framework. ATT&CK has become the de-facto framework for describing attacker tactics, techniques and procedures (TTPs). Another MITRE framework that we really love is MITRE Engage, a framework built to describe the different approaches and activities for engaging with adversaries.… Read more

-
Categories: Deception Technology
Visibility is key to stopping sophisticated threat actors. Here are the three strategic points you should cover to ensure you can detect attackers and protect your network from them. Read more
-
Categories: Cybersecurity Trends
The founders of CounterCraft talk about the recent Lapsus$ hack of Okta. Watch the video Read more
-
Learn how deception is uniquely positioned to help protect financial services. Download the data sheet for more information. Read more

-
Generic threat intel wastes a lot of time. As technology evolves, so does the threat actor. Threats and techniques change on a daily basis, making the job of the cyber defender incredibly difficult. Our approach to threat intel is the use of deception technology to collect real-time threat intel specific to your environment. This is… Read more